Cybercriminals using Prynt Stealer to collect data from victims are being swindled by the malware developer, who also receives a copy of the info over Telegram messaging service.
The malware developer has planted in the builder for the infostealer a backdoor that is present in every resulting copy that is being rented to cybercriminals for prices between $100 per month or $700 per year to $900 for a lifetime subscription.
Prynt Stealer can steal cryptocurrency wallet information, sensitive info stored in web browsers (credentials credit cards), VPN account data, cloud gaming account details.
Cyble analyzed Prynt Stealer back in April 2022 and highlighted that it included inactive code for a clipper and keylogger, both being unusual functions for an infostealer.
The data that Prynt Stealer grabs is typically compressed and exfiltrated through a Telegram bot to a channel controlled by the cybercriminal.
However, according to a report from cloud security company Zscaler, the malware comes with an additional, hardcoded Telegram token and ID to send stolen data to the author behind the operator's back.
Built for scamming
Prynt Stealer is based on the code of the AsyncRAT remote access tool and the StormKitty infostealer. The developer made some minor modifications to some of the features and removed others.
Zscaler's researchers also note that Prynt Stealer is very similar to the malware families WorldWind and DarkEye, suggesting that the same author is behind them.
Prynt Stealer's builder is meant to help unskilled cybercriminals configure the malware for deployment, setting all parameters and letting the automated tool do the work.
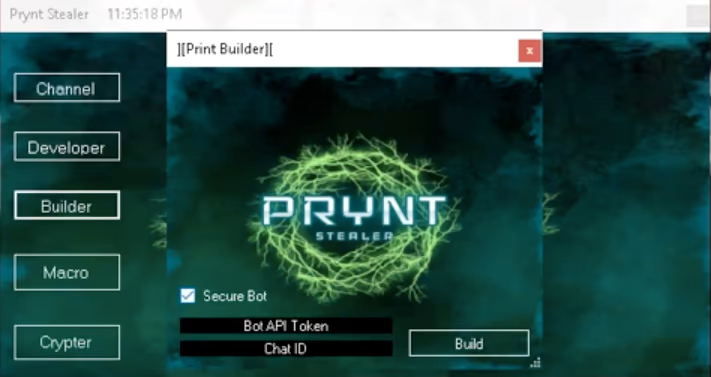
Zscaler's analysts acquired a leaked copy of the builder and found that during execution, a loader fetches 'DarkEye Stealer' from Discord and configures it to exfiltrate data to the author.
DarkEye is a variant of Prynt Stealer, the difference between them being that the clipper and keylogger functionality is enabled in the former and disabled in the latter.
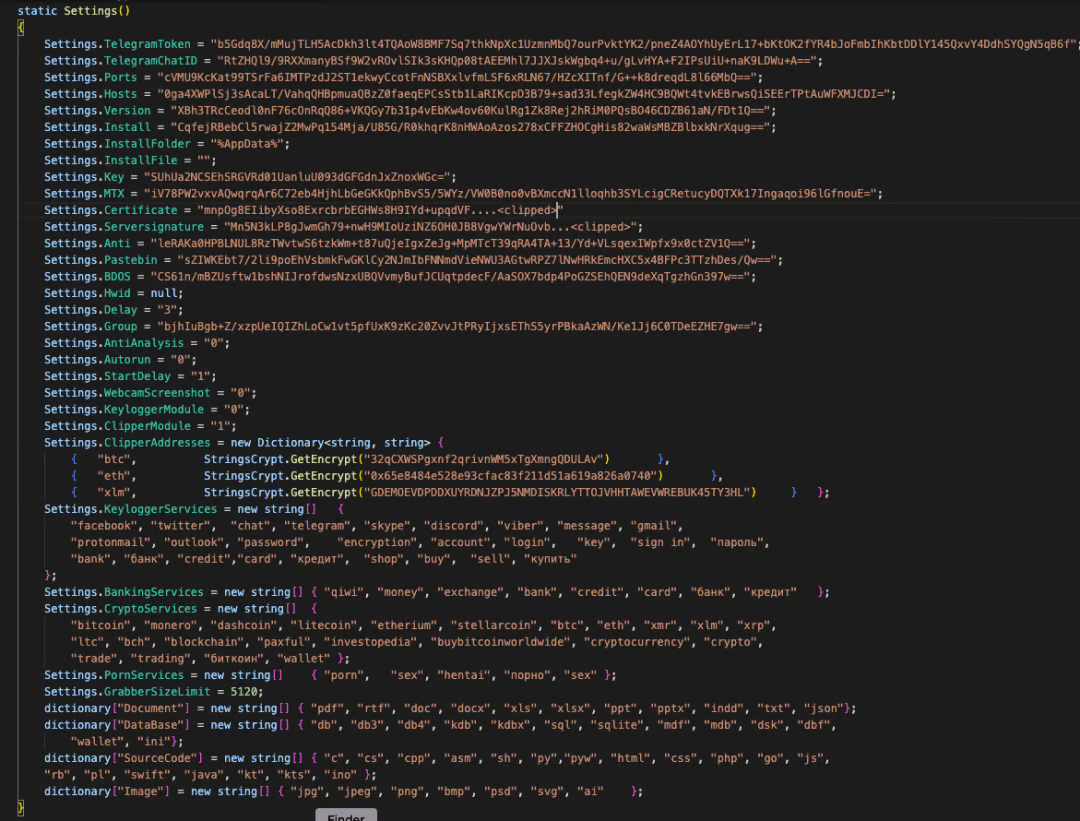
In addition, the malware author configures the builder to drop and execute LodaRAT, an old (2017) yet powerful trojan, that enables remote actors to take control of the infected system, steal information, fetch additional payloads, etc.
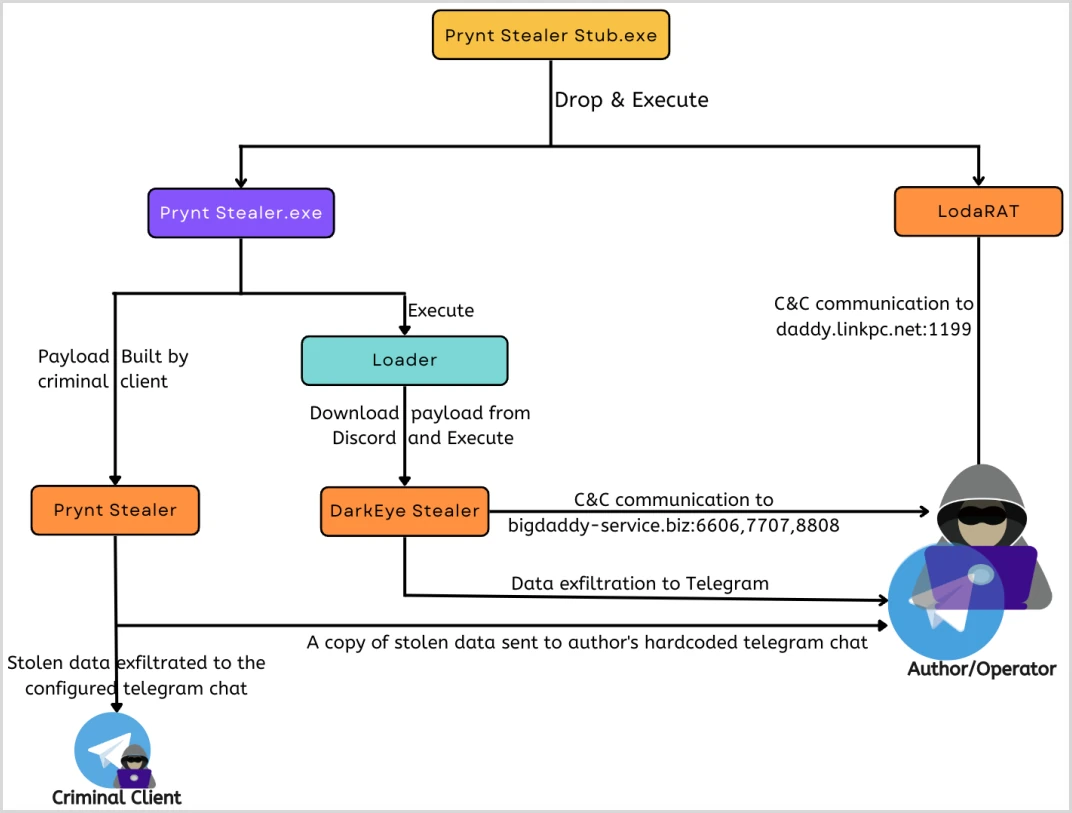
Now that the backdoor in Prynt Stealer has been exposed, the cybercriminals using it are likely to look elsewhere. It looks like the Prynt Stealer author already has two products waiting, since they are not currently actively promoted hacking forums.
Source: Bleeping Computer
- aum and Karlston
-

 2
2




Recommended Comments
There are no comments to display.
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.