A new reflection/amplification DDoS method is being used in attacks that provides a record-breaking amplification ratio of almost 4.3 billion to 1.
Distributed Denial of Service (DDoS) attacks target servers or networks with many requests and high volumes of data, aiming to deplete their available resources and cause a service outage.
The amplification ratio is critical when conducting attacks, as the higher the number, the easier it is for threat actors to overwhelm well-protected endpoints with less firepower.
A monstrous amplification level
As detailed in a report that Akamai shared with Bleeping Computer before publication, a new attack vector relies on the abuse of insecure devices that serve as DDoS reflectors/amplifiers.
Reflection attacks start with a small packet reflected inside a closed network while its size gets amplified with each bounce. When reaching the possible upper limit, the resulting volume of traffic is channeled to the target.
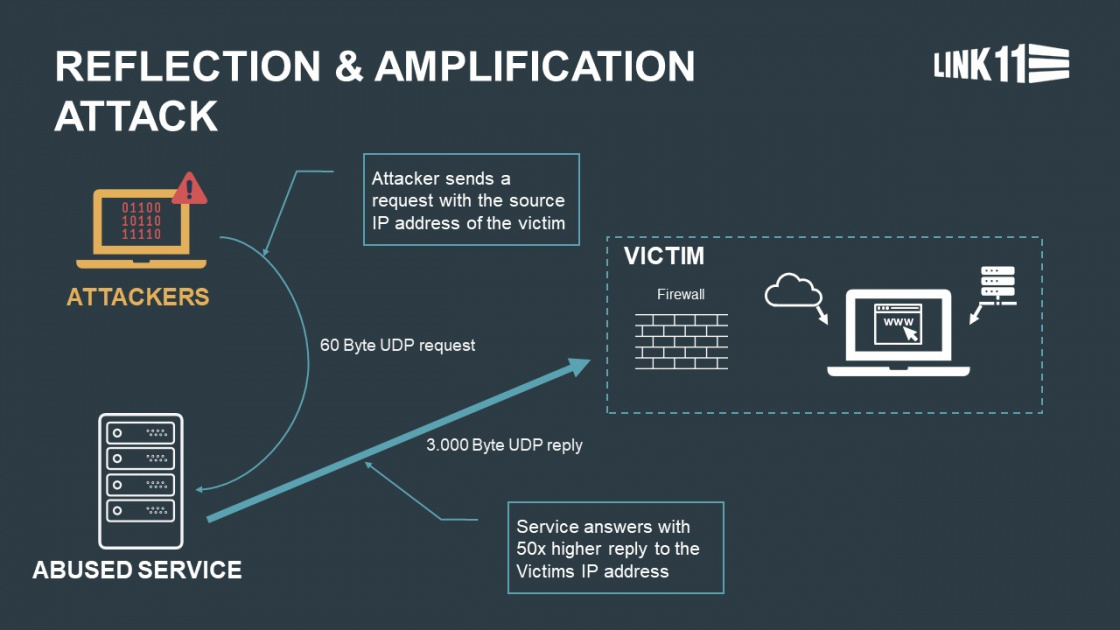
For this new DDoS method, threat actors are abusing a vulnerability tracked as CVE-2022-26143 in a driver used by Mitel devices that incorporate the TP-240 VoIP interface, such as MiVoice Business Express and MiCollab.
“The abused service on affected Mitel systems is called tp240dvr (“TP-240 driver”) and runs as a software bridge to facilitate interactions with the TP-240 VoIP processing interface cards,” Akamai explains in its report on the vulnerability.
“The daemon listens for commands on UDP/10074 and isn’t meant to be exposed to the Internet, as confirmed by the manufacturer of these devices. It’s this exposure to the internet that ultimately allows it to be abused.”
Akamai has counted 2,600 exposed Mitel devices currently vulnerable to this amplification flaw, while the vendor is already handling remediation with the customers.
The particular driver features a traffic generation command designed to stress-test the clients, used for debugging and performance testing.
By abusing this command, attackers can generate massive network traffic from these devices. Unfortunately, this is possible because the risky command is activated by default.
On a positive note, the associated daemon runs on a single-thread mode preventing parallel leverage, and due to the limited hardware resources on Mitel devices, the potential for attack volume has a relatively low upper ceiling.
Last week, Akamai disclosed a very similar DDoS method called “TCP Middlebox Reflection,” which leverages vulnerable firewalls and content filtering policy enforcement systems in middleboxes to achieve an amplification factor of 65x.
Attacks in the wild
The first signs of attacks abusing Mitel devices were noticed on January 8, 2022, while the first actual attacks leveraging the vulnerable driver began on February 18, 2022.
The targets were governments, commercial enterprises, financial institutions, logistic firms, broadband access ISPs, and other important organizations.
“Observed attacks were primarily predicated on packets-per-second, or throughput, and appeared to be UDP reflection/amplification attacks sourced from UDP/10074 that were mainly directed towards destination ports UDP/80 and UDP/443,” details Akamai in their report.
“The single largest observed attack of this type to date was approximately 53 million packets-per-second (mpps) and 23 gigabits-persecond (gb/sec). The average packet size for that attack was approximately 60 bytes, with an attack duration of approximately ~5 minutes.”
One notable difference of this vector against most UDP reflection methodologies is that it can sustain lengthy DDoS attacks, lasting for up to 14 hours.
When evaluated from this perspective, the packet amplification ratio reaches 4,294,967,296:1, and the attack traffic can go up to 400 mpps with a sustained flood of 393mb/sec.
Outlook and protection
Over the past month, DDoS attacks have become increasingly common, especially since Russia invaded Ukraine.
Even before the invasion, Ukrainian government agencies and banks suffered numerous DDoS attacks that took down their websites with the aim of sowing chaos within the country.
Since then, DDoS attacks have been conducted by Ukraine’s IT Army attacking Russian interests and supporters of Russia attacking Ukrainian and western entities.
With DDoS attacks becoming so widely used, it is essential to try and harden your infrastructure against these types of attacks, especially at the amplification levels seen in this new DDoS method.
Akamai says that monitoring UDP/10074 traffic and implementing active packet capture and analysts systems to block attacks using this port will help mitigate reflection/amplification attacks.
However, legitimate traffic may be using this port that would also be blocked.
The best way to prevent this new DDoS method is for organizations that use the TP-240 interface to follow Mitel’s remediation instructions, enforcing firewall rules to block malicious initiator packets or disable the abused command.
DDoS attacks now use new record-breaking amplification vector
- Ha91 and aum
-

 2
2



3175x175(CURRENT).thumb.jpg.b05acc060982b36f5891ba728e6d953c.jpg)
Recommended Comments
There are no comments to display.
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.