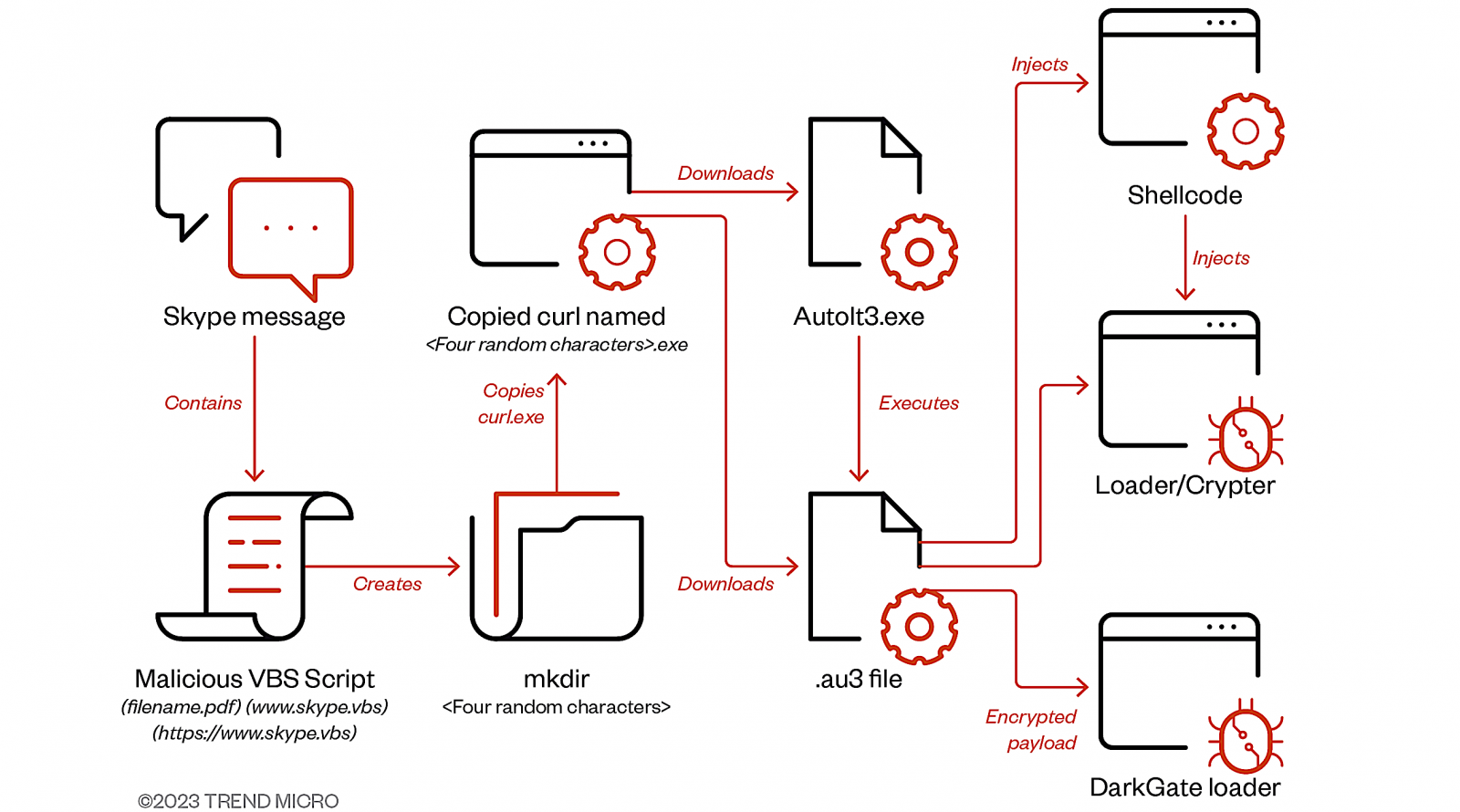
Between July and September, DarkGate malware attacks have used compromised Skype accounts to infect targets through messages containing VBA loader script attachments.
According to Trend Micro security researchers who spotted the attacks, this script downloads a second-stage AutoIT script designed to drop and execute the final DarkGate malware payload.
"Access to the victim's Skype account allowed the actor to hijack an existing messaging thread and craft the naming convention of the files to relate to the context of the chat history," Trend Micro said.
"It's unclear how the originating accounts of the instant messaging applications were compromised, however is hypothesized to be either through leaked credentials available through underground forums or the previous compromise of the parent organization,"
Trend Micro also observed the DarkGate operators trying to push their malware payload through Microsoft Teams in organizations where the service was configured to accept messages from external users.
Teams phishing campaigns using malicious VBScript to deploy DarkGate malware were previously spotted by Truesec and MalwareBytes.
As they explained, malicious actors targeted Microsoft Teams users via compromised Office 365 accounts outside their organizations and a publicly available tool named TeamsPhisher. This tool enables attackers to bypass restrictions for incoming files from external tenants and send phishing attachments to Teams users.
"The goal is still to penetrate the whole environment, and depending on the threat group that bought or leased the DarkGate variant used, the threats can vary from ransomware to cryptomining," Trend Micro said.
"From our telemetry, we have seen DarkGate leading to tooling being detected commonly associated with the Black Basta ransomware group."
DarkGate malware surge
Cybercriminals have increasingly adopted the DarkGate malware loader for initial access into corporate networks, a trend observed since the disruption of the Qakbot botnet in August due to international collaborative efforts.
Before Qakbot's dismantling, an individual purporting to be DarkGate's developer attempted to sell subscriptions on a hacking forum, quoting an annual fee of up to $100,000.
The malware was touted to offer a wide range of features, including a concealed VNC, capabilities to bypass Windows Defender, a browser history theft tool, an integrated reverse proxy, a file manager, and a Discord token stealer.
Following this announcement, there's been a noticeable uptick in reports documenting DarkGate infections via various delivery methods, such as phishing and malvertising.
This recent surge in DarkGate activity underscores the growing influence of this malware-as-a-service (MaaS) operation within the cybercriminal sphere.
It also emphasizes the threat actors' determination to continue their attacks, adapting their tactics and methods despite disruptions and challenges.
- Ha91
-

 1
1



3175x175(CURRENT).thumb.jpg.b05acc060982b36f5891ba728e6d953c.jpg)
Recommended Comments
There are no comments to display.
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.