While analyzing its capabilities, Akamai researchers have accidentally taken down a cryptomining botnet that was also used for distributed denial-of-service (DDoS) attacks.
As revealed in a report published earlier this month, the KmsdBot malware behind this botnet was discovered by members of the Akamai Security Intelligence Response Team (SIRT) after it infected one of their honeypots.
KmsdBot targets Windows and Linux devices with a wide range of architectures, and it infects new systems via SSH connections that use weak or default login credentials.
Compromised devices are being used to mine for cryptocurrency and launch DDoS attacks, with some of the previous targets being gaming and technology companies, as well as luxury car manufacturers.
Unfortunately for its developers and luckily for the device owners, the botnet doesn't yet have persistence capabilities to evade detection.
However, this means the malware has to start all over if it's detected and removed or it malfunctions in any way and loses its connection to the command-and-control (C2) server.
Tango Down
This is also what also led to the botnet's demise after the current versions of the KmsdBot malware was unintentionally deactivated by Akamai's researchers.
"In our controlled environment, we were able to send commands to the bot to test its functionality and attack signatures," Akamai vulnerability researcher Larry Cashdollar explained in a new report.
"As part of this analysis, a syntax error caused the bot to stop sending commands, effectively killing the botnet."
What helped take down KmsdBot was its lack of error-checking and "the coding equivalent of a typo," which led to the malware crashing and stopping to send attack commands due to the wrong number of arguments to the C2 server.
Basically, as Cashdollar explained, the crash was caused by issuing an attack command where the space between the target website and the port was missing.
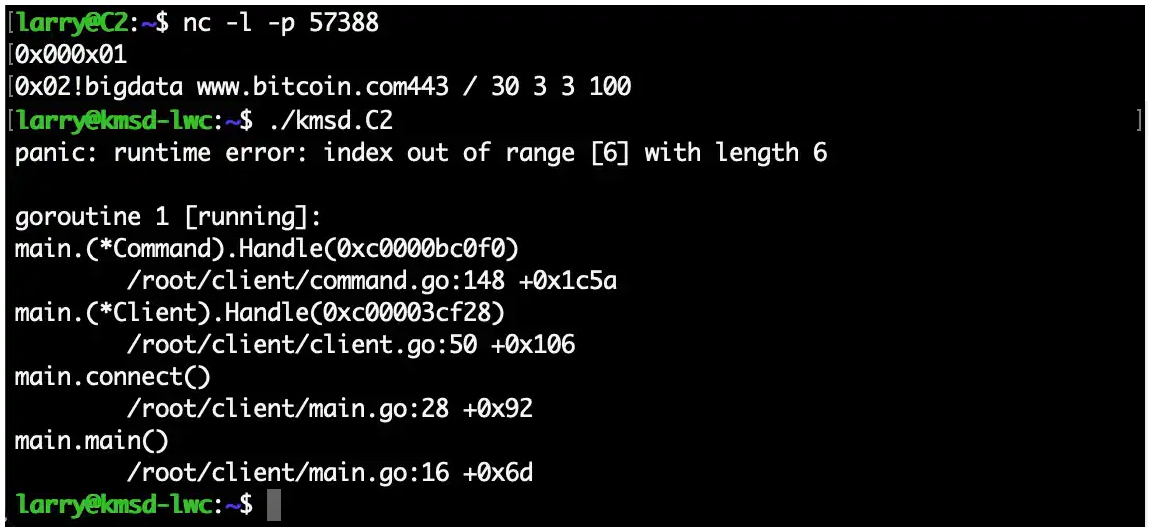
KmsdBot botnet crash (Akamai)
"This malformed command likely crashed all the botnet code that was running on infected machines and talking to the C2 — essentially, killing the botnet," Cashdollar added.
"Because the bot doesn’t have any functionality for persistence on an infected machine, the only way to recover is to re-infect and rebuild the botnet from scratch."
Organizations that could be the target of botnets using similar spreading tactics are advised to secure their systems against attacks by:
- Not using weak credentials and changing default ones for servers or deployed apps
- Ensuring all deployed software is up-to-date
- Using public key authentication for SSH connections to avoid compromise via credential brute-forcing
- Karlston
-

 1
1




Recommended Comments
There are no comments to display.
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.