A new dropper-as-a-service (DaaS) cybercrime operation named 'SecuriDropper' has emerged, using a method that bypasses the 'Restricted Settings' feature in Android to install malware on devices and obtain access to Accessibility Services.
Restricted Settings is a security feature introduced with Android 13 that prevents side-loaded applications (APK files) installed from outside Google Play to access powerful features like the Accessibility settings and Notification Listener.
The two permissions are commonly abused by malware, so the feature was intended to protect users by blocking the approval of requests by displaying a warning when these permissions are requested.
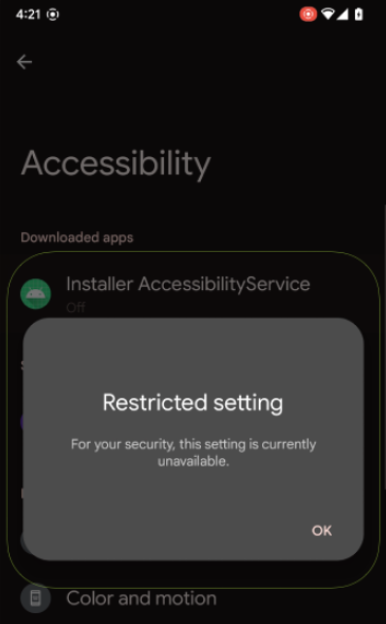
Restricted Settings warning pop-up(ThreatFabric)
Accessibility can be abused to capture on-screen text, granting additional permissions, and performing navigation actions remotely, while the Notification Listener can be used to steal one-time passwords.
In August 2022, ThreatFabric reported that malware developers were already adjusting their tactics to this new measure through a new dropper named 'BugDrop.'
Based on its observations, the firm created a proof-of-concept (PoC) dropper to showcase that the bypass was possible.
The trick is to use the session-based installation API for the malicious APK (Android package) files, which installs them in multiple steps, involving a "base" package and various "split" data files.
When the particular API is used instead of the non-session method, Restricted Settings is bypassed, and users are not shown the 'Restricted setting' dialog that prevents them from granting the malware access to dangerous permissions.
BleepingComputer has confirmed that the security issue is still present in Android 14, and, according to a new ThreatFabric report, SecuriDropper follows the same technique to side-load malware on target devices and give them access to risky sub-systems.
This is the first observed case of this method being used in cybercrime operations targeting Android users.
Android Dropper-as-a-Service operations
SecuriDropper infects Android devices posing as a legitimate app, most often impersonating a Google app, Android update, video player, security app, or a game, and then installing a second payload, which is some form of malware.
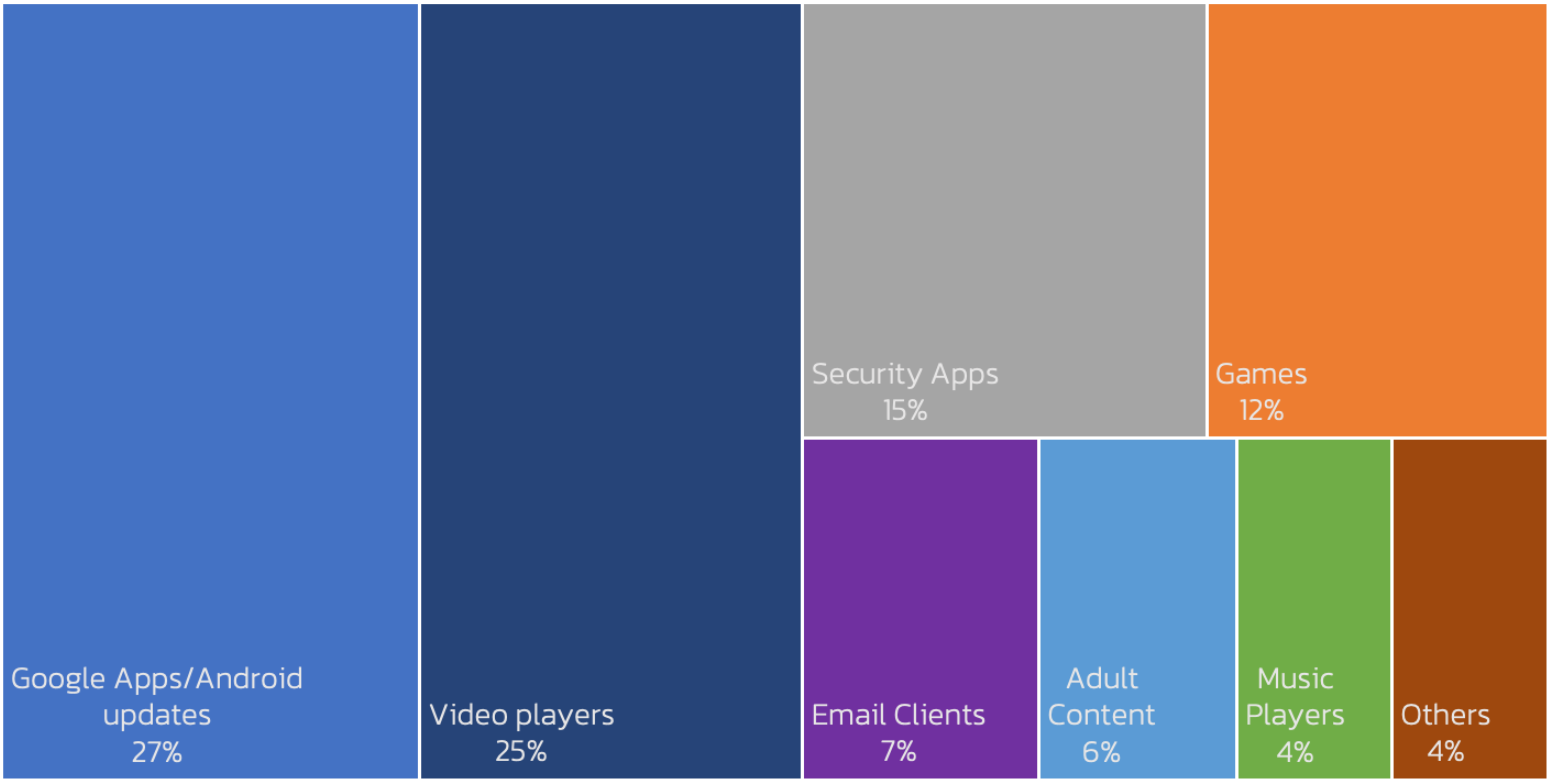
App types SecuriDropper impersonates (ThreatFabric)
The dropper achieves this by securing access to the "Read & Write External Storage" and "Install & Delete Packages" permissions upon installation.
The second-stage payload is installed through user deception and interface manipulation, prompting users to click a "Reinstall" button after displaying bogus error messages about the dropper app's installation.
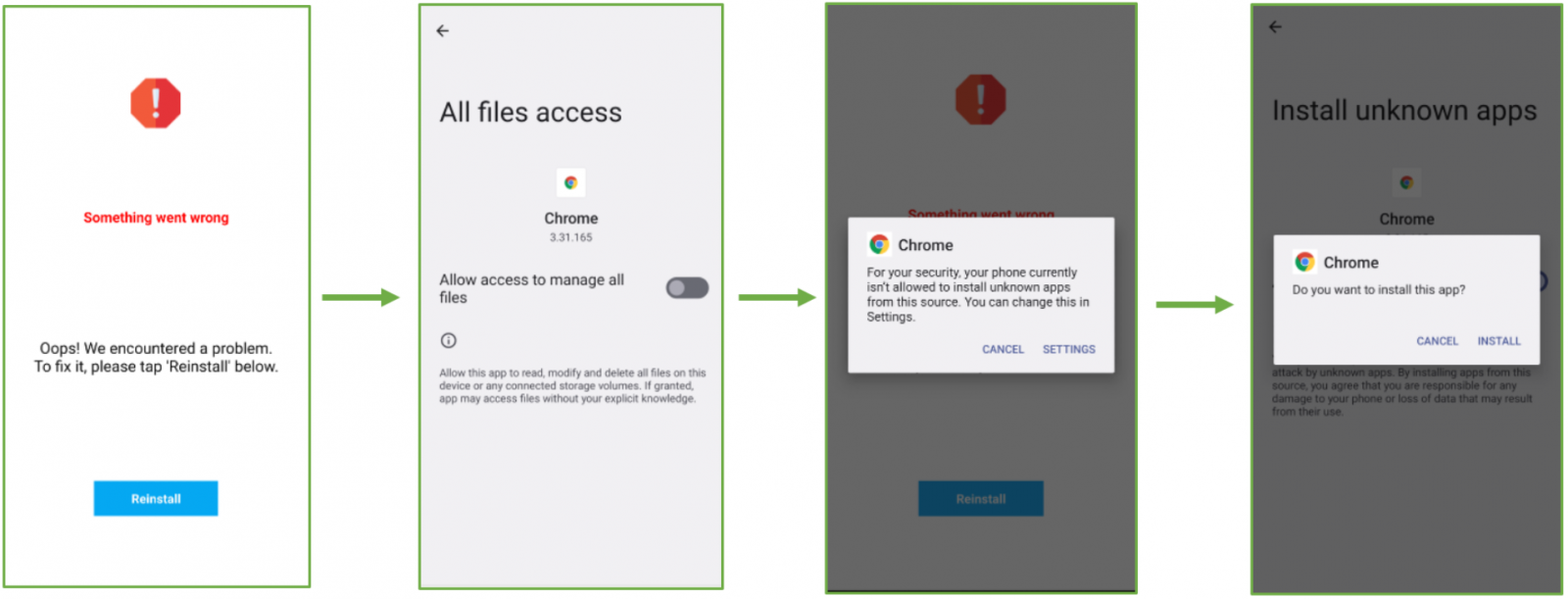
Payload dropping process (ThreatFabric)
ThreatFabric has seen SpyNote malware distributed through SecuriDropper disguised as a Google Translate app.
In other cases, SecuriDropper was seen distributing banking Ermac trojans disguised as the Chrome browser, targeting hundreds of cryptocurrency and e-banking applications.
ThreatFabric also reports on the re-surfacing of Zombinder, a DaaS operation first documented in December 2022. This service "glues" malicious payloads with legitimate apps to infect Android devices with info-stealers and banking trojans.
Worryingly, Zombinder's recent advertisements highlight the same Restricted Settings bypass strategy previously discussed, so the payloads are granted permission to use Accessibility settings upon installation.
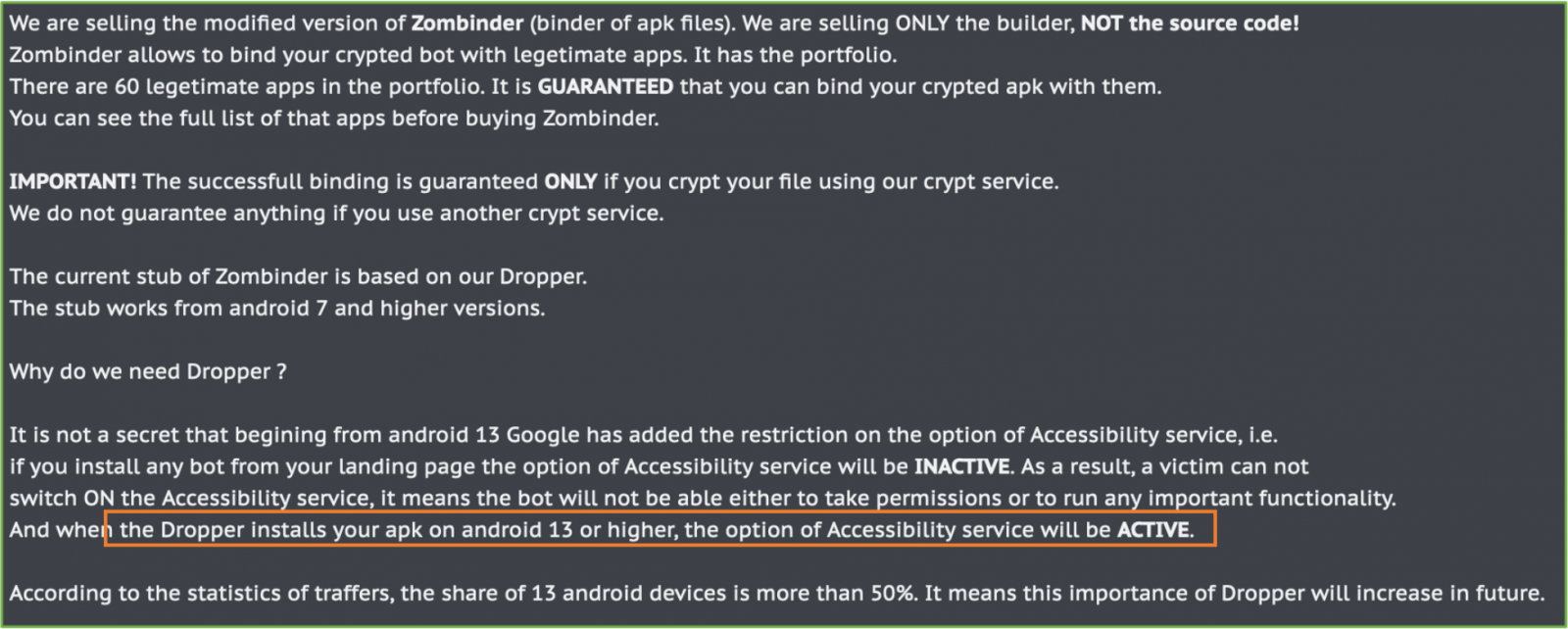
Zombinder's latest advertisement (ThreatFabric)
To protect against these attacks, Android users should avoid downloading APK files from obscure sources or publishers they don't know and trust.
Access to permissions for any installed app can be reviewed and revoked by going to Settings → Apps → [select an app] → Permissions.
Update 11/6: In response to a request for a comment by BleepingComputer, a Google spokesperson has sent us the following statement:
Restricted settings add an extra layer of protection on top of the user confirmation that is required for apps to access Android settings/permissions.
As a core protection, Android users are always in control of which permissions they grant to an app.
Users are also protected by Google Play Protect, which can warn users or block apps known to exhibit malicious behavior on Android devices with Google Play Services.
We are constantly reviewing attack methods and improving Android's defenses against malware to help keep users safe.
- thunderpants
-

 1
1



3175x175(CURRENT).thumb.jpg.b05acc060982b36f5891ba728e6d953c.jpg)
Recommended Comments
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.