Cyber espionage by Chinese hackers in neighbouring nations is on the rise
A string of cyber espionage campaigns dating all the way back to 2014 and focused on gathering military intelligence from neighbouring countries have been linked to a Chinese military-intelligence apparatus.
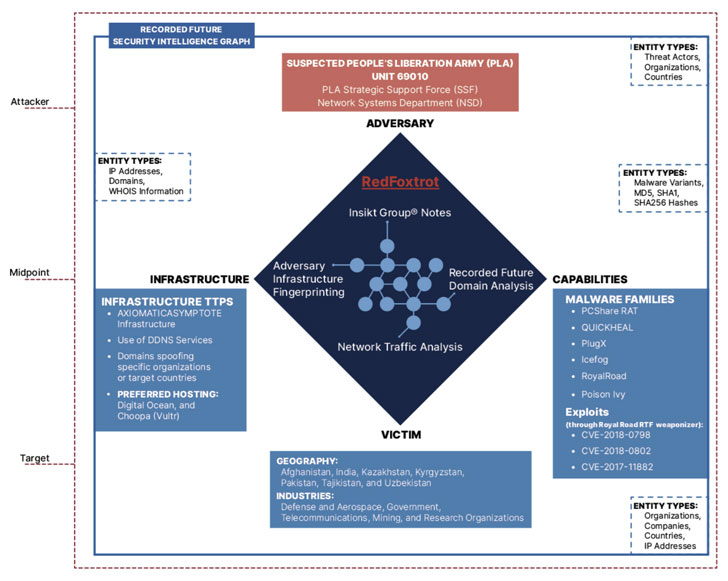
In a wide-ranging report published by Massachusetts-headquartered Recorded Future this week, the cybersecurity firm's Insikt Group said it identified ties between a group it tracks as "RedFoxtrot" to the People's Liberation Army (PLA) Unit 69010 operating out of Ürümqi, the capital of the Xinjiang Uyghur Autonomous Region in the country.
Previously called the Lanzhou Military Region's Second Technical Reconnaissance Bureau, Unit 69010 is a military cover for a Technical Reconnaissance Bureau (TRB) within China's Strategic Support Force (SSF) Network Systems Department (NSD).
The connection to PLA Unit 69010 stems from what the researchers said were "lax operational security measures" adopted by an unnamed suspected RedFoxtrot threat actor, whose online persona disclosed the physical address of the reconnaissance bureau and has had a history of affiliating with the PLA's former Communications Command Academy in Wuhan.
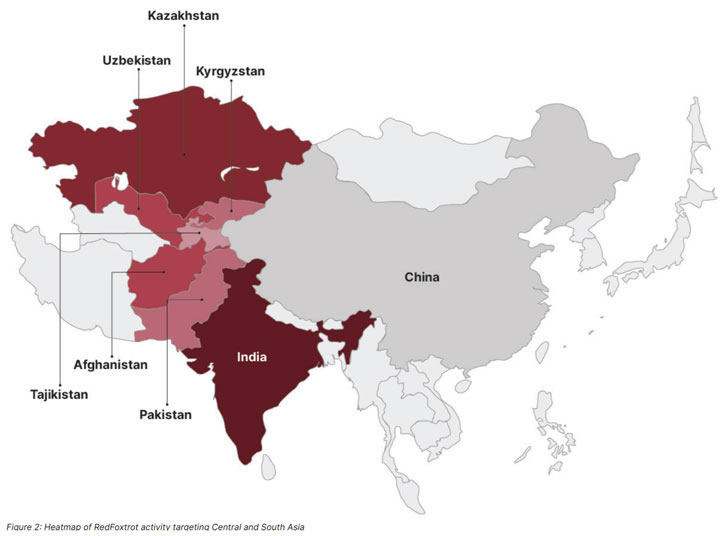
RedFoxtrot is noted to target government, defense, and telecommunications sectors across Central Asia, India, and Pakistan, with intrusions in the last six months directed against three Indian aerospace and defense contractors as well as major telecommunications providers and government agencies in Afghanistan, India, Kazakhstan, and Pakistan.
"Activity over this period showed a particular focus on Indian targets, which occurred at a time of heightened border tensions between India and the People's Republic of China," the researchers said.
Attacks staged by the adversary involved an assortment of open- and closed-source tools that have been shared across Chinese cyberespionage groups, including PlugX, Royal Road RTF weaponizer, QUICKHEAL, PCShare, IceFog, and Poison Ivy RAT.
Also observed is the use of AXIOMATICASYMPTOTE infrastructure, which encompasses a modular Windows backdoor called ShadowPad that has been previously attributed to APT41 and subsequently shared between other Chinese state-backed actors.
Furthermore, domains registered by RedFoxtrot — "inbsnl.ddns[.]info" and "adtl.mywire[.]org" — suggest that the threat actor may have set its sights on Indian telecom service provider Bharat Sanchar Nigam Limited (BSNL) and a Bengaluru-based company called Alpha Design Technologies Limited (ADTL) that specializes in research and development of missile, radar, and satellite systems.
The development comes more than three months after another China-linked threat group, dubbed RedEcho, was uncovered targeting India's power grid, including a power plant run by National Thermal Power Corporation (NTPC) Limited and New Delhi-based Power System Operation Corporation Limited.
- Karlston
-

 1
1




Recommended Comments
There are no comments to display.
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.