Cybersecurity researchers on Wednesday disclosed 14 vulnerabilities affecting a commonly-used TCP/IP stack used in millions of Operational Technology (OT) devices manufactured by no fewer than 200 vendors and deployed in manufacturing plants, power generation, water treatment, and critical infrastructure sectors.
The shortcomings, collectively dubbed "INFRA:HALT," target NicheStack, potentially enabling an attacker to achieve remote code execution, denial of service, information leak, TCP spoofing, and even DNS cache poisoning.
NicheStack (aka InterNiche stack) is a closed-source TCP/IP stack for embedded systems that is designed to provide internet connectivity industrial equipment, and is incorporated by major industrial automation vendors like Siemens, Emerson, Honeywell, Mitsubishi Electric, Rockwell Automation, and Schneider Electric in their programmable logic controllers (PLCs) and other products.
"Attackers could disrupt a building's HVAC system or take over the controllers used in manufacturing and other critical infrastructure," researchers from JFrog and Forescout said in a joint report published today. "Successful attacks can result in taking OT and ICS devices offline and having their logic hijacked. Hijacked devices can spread malware to where they communicate on the network."
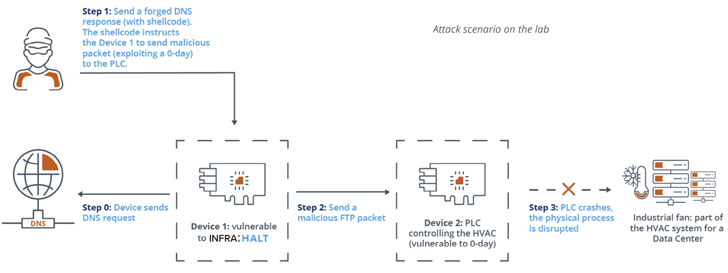
All versions of NicheStack before version 4.3 are vulnerable to INFRA:HALT, with approximately 6,400 OT devices exposed online and connected to the internet as of March 2021, most of which are located in Canada, the U.S., Spain, Sweden, and Italy.
The list of 14 flaws is as follows -
- CVE-2020-25928 (CVSS score: 9.8) - An out-of-bounds read/write when parsing DNS responses, leading to remote code execution
- CVE-2021-31226 (CVSS score: 9.1) - A heap buffer overflow flaw when parsing HTTP post requests, leading to remote code execution
- CVE-2020-25927 (CVSS score: 8.2) - An out-of-bounds read when parsing DNS responses, leading to denial-of-service
- CVE-2020-25767 (CVSS score: 7.5) - An out-of-bounds read when parsing DNS domain names, leading to denial-of-service and information disclosure
- CVE-2021-31227 (CVSS score: 7.5) - A heap buffer overflow flaw when parsing HTTP post requests, leading to denial-of-service
- CVE-2021-31400 (CVSS score: 7.5) - An infinite loop scenario in the TCP out of band urgent data processing function, causing a denial-of-service
- CVE-2021-31401 (CVSS score: 7.5) - An integer overflow flaw in the TCP header processing code
- CVE-2020-35683 (CVSS score: 7.5) - An out-of-bounds read when parsing ICMP packets, leading to denial-of-service
- CVE-2020-35684 (CVSS score: 7.5) - An out-of-bounds read when parsing TCP packets, leading to denial-of-service
- CVE-2020-35685 (CVSS score: 7.5) - Predictable initial sequence numbers (ISNs) in TCP connections, leading to TCP spoofing
- CVE-2021-27565 (CVSS score: 7.5) - A denial-of-service condition upon receiving an unknown HTTP request
- CVE-2021-36762 (CVSS score: 7.5) - An out-of-bounds read in the TFTP packet processing function, leading to denial-of-service
- CVE-2020-25926 (CVSS score: 4.0) - The DNS client does not set sufficiently random transaction IDs, causing cache poisoning
- CVE-2021-31228 (CVSS score: 4.0) - The source port of DNS queries can be predicted to send forged DNS response packets, causing cache poisoning
The disclosures mark the sixth time security weaknesses have been identified in the protocol stacks that underpin millions of internet-connected devices. It's also the fourth set of bugs to be uncovered as part of a systematic research initiative called Project Memoria to study the security of widely-used TCP/IP stacks that are incorporated by various vendors in their firmware to offer internet and network connectivity features -
- URGENT/11
- Ripple20
- AMNESIA:33
- NUMBER:JACK
- NAME:WRECK
While HCC Embedded, which maintains the C library, has released software patches to address the issues, it could take a considerable amount of time before device vendors using vulnerable versions of the stack ship an updated firmware to their customers. "Complete protection against INFRA:HALT requires patching vulnerable devices but is challenging due to supply chain logistics and the critical nature of OT devices," the researchers noted.
As mitigations, Forescout has released an open-source script that uses active fingerprinting to detect devices running NicheStack. It's also recommended to enforce segmentation controls, monitor all network traffic for malicious packets to mitigate the risk from vulnerable devices.
- Karlston
-

 1
1



Recommended Comments
There are no comments to display.
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.