A critical vulnerability in the Shim Linux bootloader enables attackers to execute code and take control of a target system before the kernel is loaded, bypassing existing security mechanisms.
Shim is a small open-source bootloader maintained by Red Hat that is designed to facilitate the Secure Boot process on computers using Unified Extensible Firmware Interface (UEFI).
The tool is signed with a Microsoft key accepted by default on most UEFI motherboards that is used to verify the next stage of the boot process, typically loading the GRUB2 bootloader.
Shim was created out of necessity to allow open-source projects such as Linux distributions to benefit from Secure Boot's advantages, such as preventing unauthorized or malicious code execution during boot, while still maintaining control over hardware.
The new Shim flaw, tracked as CVE-2023-40547, was discovered by Microsoft's security researcher Bill Demirkapi, who first disclosed it on January 24, 2024.
The bug resides in the httpboot.c source for Shim, which is used to boot a network image over HTTP.
"When retrieving files via HTTP or related protocols, shim attempts to allocate a buffer to store the received data," reads the commit to fix the bug in httpboot.c.
"Unfortunately, this means getting the size from an HTTP header, which can be manipulated to specify a size that's smaller than the received data."
"In this case, the code accidentally uses the header for the allocation but the protocol metadata to copy it from the rx buffer, resulting in an out-of-bounds write."
More details about the flaw became available on February 2, 2024, with Eclypsium publishing a report yesterday to draw attention to this security problem.
The vulnerability lies in Shim's parsing of HTTP responses, allowing an attacker to create specially crafted HTTP requests to cause an out-of-bounds write.
This could allow an attacker to compromise a system by executing privileged code before the operating system loads, effectively bypassing security mechanisms implemented by the kernel and the OS.
Eclypsium says multiple potential exploitation paths can leverage CVE-2023-40547, including local, network adjacent, and remote attack points. The firm's report highlights the following three methods:
A remote attacker can execute a man-in-the-middle (MiTM) attack, intercepting HTTP traffic for HTTP boot, potentially from any network position between the victim and the server.
A local attacker with sufficient privileges can modify EFI Variables or the EFI partition using a live Linux USB to alter the boot order and load a compromised shim, executing privileged code without disabling Secure Boot.
An attacker on the same network can use PXE to load a compromised shim bootloader, exploiting the vulnerability.
Impact and fixes
RedHat issued a code commit to fix CVE-2023-40547 on December 5, 2023, but Linux distributions supporting Secure Boot and using Shim need to push their own patches.
Linux distributions that utilize Shim, such as Red Hat, Debian, Ubuntu, and SUSE, have released advisories with information on the flaw.
Linux users are advised to update to the latest version of Shim, v15.8, which contains a fix for CVE-2023-40547 and five other important vulnerabilities.
Eclypsium explains that Linux users must also update the UEFI Secure Boot DBX (revocation list) to include the hashes of the vulnerable Shim software and sign the patched version with a valid Microsoft key.
To do that, first upgrade to Shim 15.8 and then apply the DBX update using the 'fwupdmgr update' command (needs fwupd).
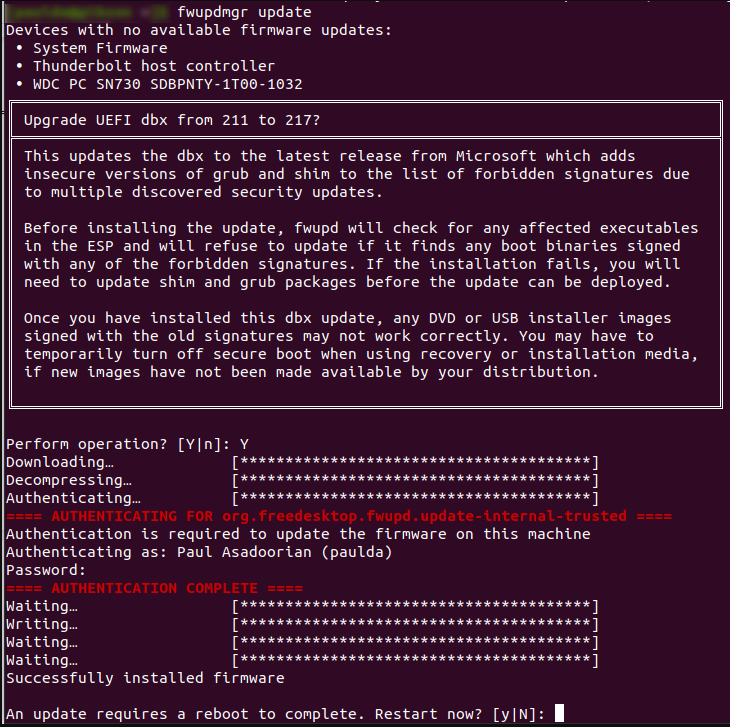
Some Linux distributions offer a GUI tool to perform this update, so make sure to check on your package manager before delving into the terminal.
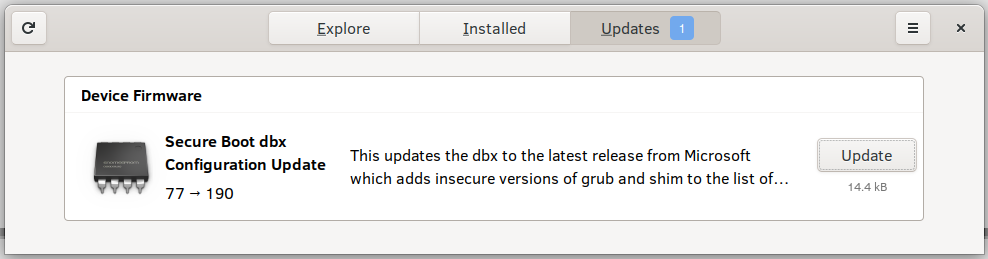
Although unlikely to be mass-exploited, CVE-2023-40547 is not a bug that should be ignored, as executing code before OS boot is one of the strongest and stealthiest forms of system compromise.



3175x175(CURRENT).thumb.jpg.b05acc060982b36f5891ba728e6d953c.jpg)
Recommended Comments
There are no comments to display.
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.