The authors of the Elementor Website Builder plugin for WordPress have just released version 3.6.3 to address a critical remote code execution flaw that may impact as many as 500,000 websites.
Although exploiting the flaw requires authentication, it's critical severity is given by the fact that anyone logged into the vulnerable website can exploit it, including regular subscribers.
A threat actor creating a normal user account on an affected website could change the name and theme of the affected site making it look entirely different.
Security researchers believe that a non-logged in user could also exploit the recently fixed flaw in Elementor plugin but they have not confirmed this scenario.
Vulnerability details
In a report released this week by researchers at the WordPress security service Plugin Vulnerabilities, who found the vulnerability, describe the technical details behind the issue in Elementor.
The problem lies in the absence of a crucial access check on one of the plugin's files, "module.php", which is loaded on every request during the admin_init action, even for users that are not logged in, the researchers explain.
"The RCE vulnerability we found involves the function upload_and_install_pro() accessible through the previous function. That function will install a WordPress plugin sent with the request" - Plugin Vulnerabilities
One of the functions triggered by the admin_init action allows file upload in the form of a WordPress plugin. A threat actor could place a malicious file there to achieve remote code execution.
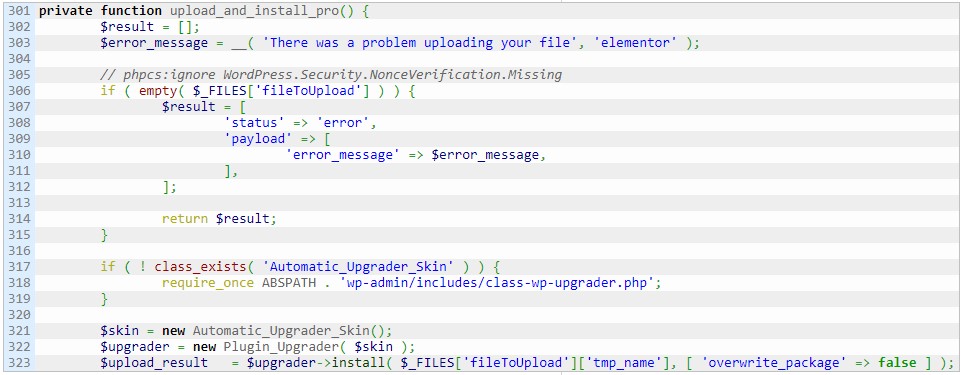
The file upload function (Plugin Vulnerabilities)
![]()
Activation of the injected malicious plugin (PV)
The researchers say that the only restriction in place is access to a valid nonce. However, they found that the relevant nonce is present in "source code of admin pages of WordPress that starts 'elementorCommonConfig', which is included when logged in as a user with the Subscriber role."
Impact and fixing
According Plugin Vulnerabilities, the issue was introduced with Elementor 3.6.0, released on March 22, 2022.
WordPress stats report that approximately 30.7% of Elementor's users have upgraded to version 3.6.x, which indicates that the maximum number of potentially affected sites is roughly 1,500,000.
The plugin has been downloaded a little over one million times today. Assuming that all of them were for 3.6.3, there must still be around 500,000 vulnerable websites out there.
The latest version includes a commit that implements an additional check on the nonce access, using the "current_user_can" WordPress function.
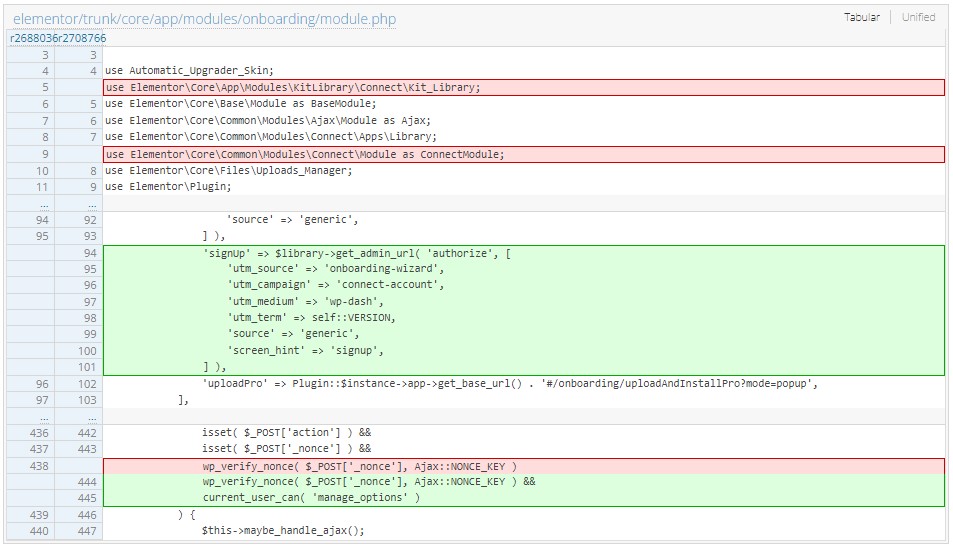
Commit in Elementor addressing the security flaw (WordPress)
While this should address the security gap, the researchers haven't validated the fix yet, and the Elementor team hasn't published any details about the patch.
BleepingComputer has reached out to Elementor's security team, and will update this article as soon as we receive a response.
Plugin Vulnerabilities has also published a proof of concept (PoC) to prove the exploitability, increasing the risk of vulnerable websites to be compromised.
Admins are advised to apply the latest update available for the Elementor WordPress plugin or remove the plugin from your website altogether.
Critical flaw in Elementor WordPress plugin may affect 500k sites
- aum
-

 1
1



3175x175(CURRENT).thumb.jpg.b05acc060982b36f5891ba728e6d953c.jpg)
Recommended Comments
There are no comments to display.
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.