A sophisticated threat actor named 'CashRewindo' has been using 'aged' domains in global malvertising campaigns that lead to investment scam sites.
Malvertising involves the injection of malicious JavaScript code in digital ads promoted by legitimate advertising networks, taking website visitors to pages that host phishing forms, drop malware, or operate scams.
The CashRewindo malvertising campaigns are spread across Europe, North and South America, Asia, and Africa, using customized language and currency to appear legitimate to the local audience.
Analysts at Confiant have been tracking 'CashRewindo' since 2018 and report the threat actor stands out for an unusually crafty approach in setting up malicious advertising operations with great attention to detail.
Domains get better with age
Domain aging is when threat actors register domains and wait years to use them, hoping to bypass security platforms.
This technique works as old domains that have not been involved in malicious activity for a long time earn trust on the Internet, making them unlikely to be flagged by security tools as suspicious.
Confiant says CashRewindo uses domains that have aged for at least two years before they are activated (have their certificates updated and a virtual server assigned).
The security firm was able to identify at least 487 domains used by the particular threat actor, some having been registered as far back as 2008 and used for the first time in 2022.
Victims end up on these landing sites by clicking on infected ads found on legitimate sites.
To evade "strong language" detection on legitimate sites, the threat actor flips between innocuous and call-to-action wording, usually starting the campaign carefully and switching to call-to-action ads later.
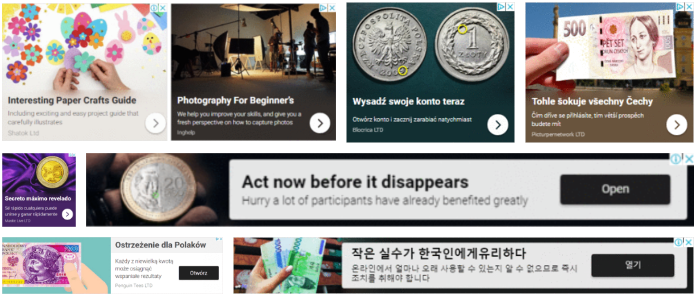
Mix of ads used by CashRewindo (Confiant)
The malicious ads also feature a tiny red circle that helps confuse computer vision detection modules so they cannot catch the fraud.
Global but highly targeted
Each CashRewindo campaign targets a particular audience, so the landing pages are configured to either show the scam or an innocuous or blank page for invalid targets.
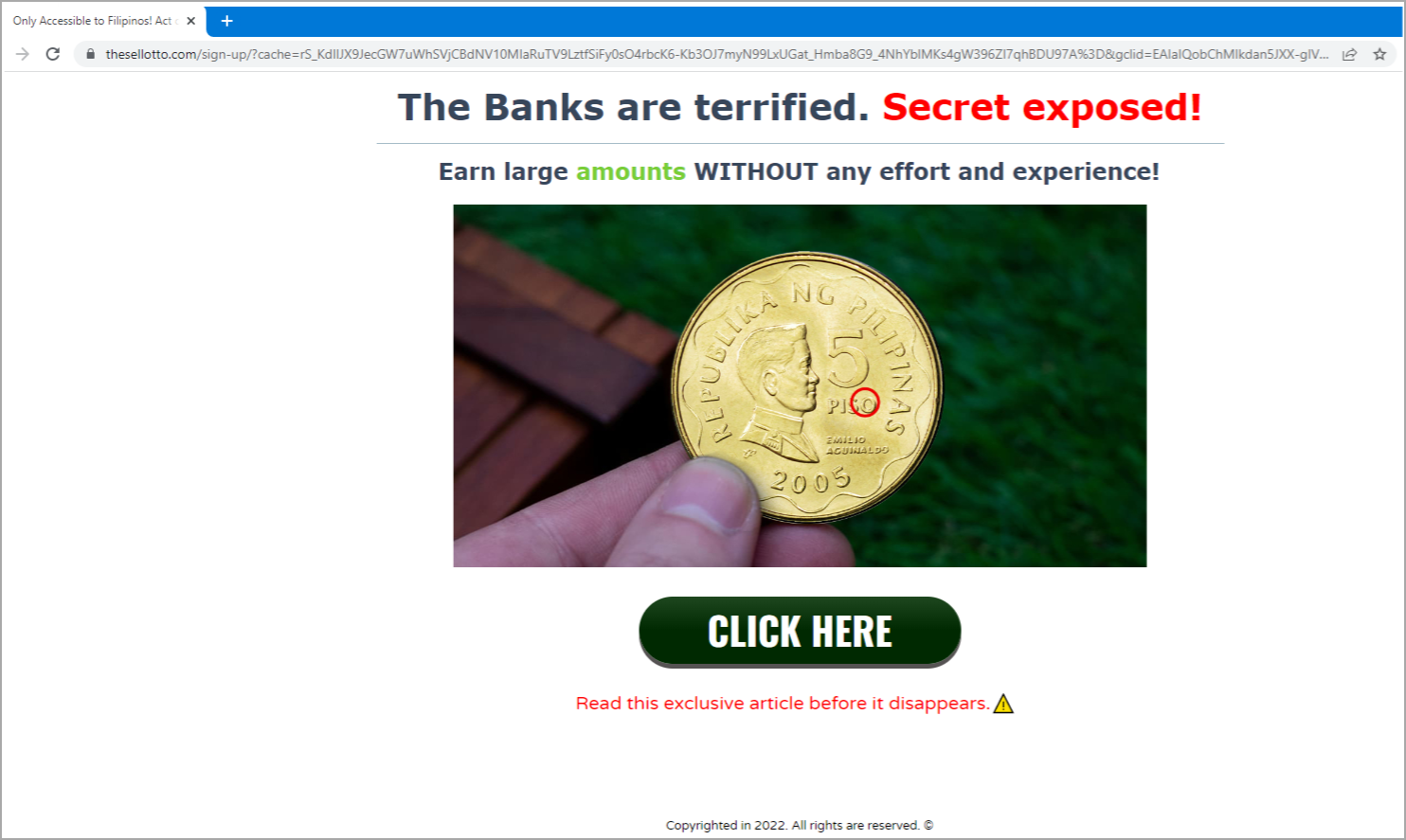
Landing page with 'click here' button (Confiant)
This is done by checking the timezone, device platform, and language used on the visitor's system.
Users and devices outside the target audience clicking the embedded "Click Here" button will be redirected to an innocuous site.
Valid targets, on the other hand, will execute JavaScript code with the malicious code hiding inside a common library to evade request inspection.
.png)
Malicious JS snippet running on valid targets (Confiant)
Those users are taken to a scam page and eventually redirected to a fake cryptocurrency investment platform promising unrealistic investment returns.
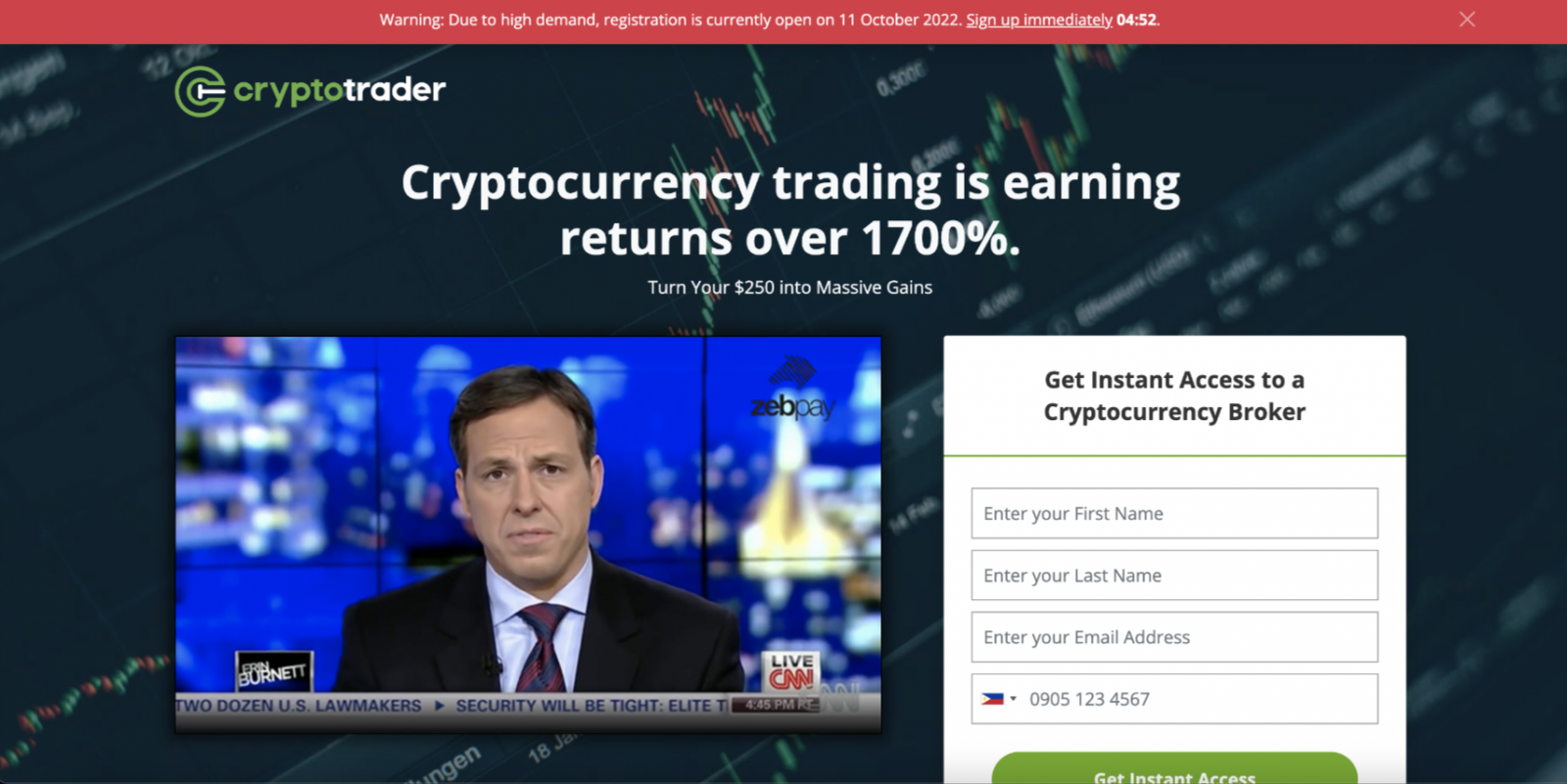
Fraudulent investment site (Confiant)
Confiant reports that over 12 months, it has recorded over 1.5 million CashRewindo impressions, primarily targeting Windows devices.
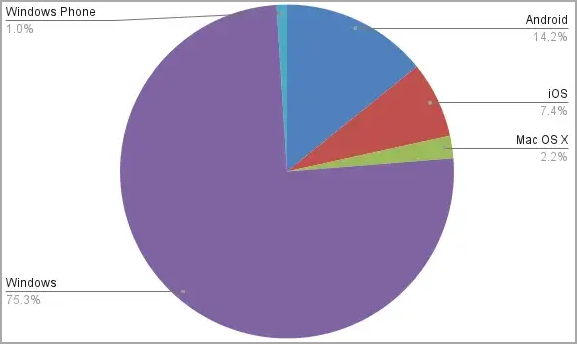
Targeted platforms (Confiant)
As for which countries bring most of these impressions, the top 20 most targeted locations are shown in the table below.
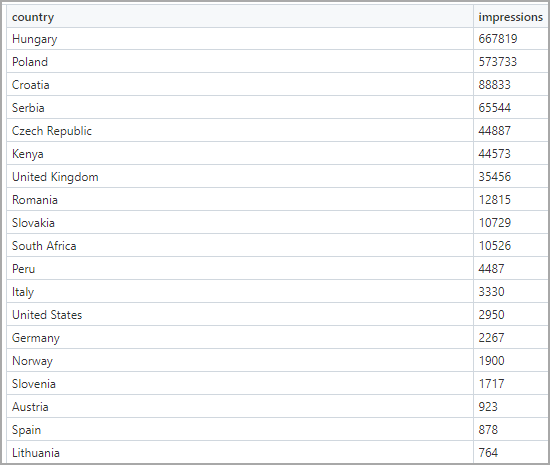
Top 20 most targeted countries (Confiant)
Investment scams are widespread, but usually, threat actors prefer quantity over quality, pushing their hastily crafted fake sites to large pools of users and hosting the scam platforms on recently registered domains doomed to go offline quickly.
CashRewindo follows a different approach that requires more work but significantly improves the chances of success for the threat actor.
Any investment opportunity that guarantees returns is most likely a scam, so treat this as a big red flag and run an extensive background check before depositing any funds.




Recommended Comments
There are no comments to display.
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.