Crackonosh virus mined $2 million of Monero from 222,000 hacked computers
A previously undocumented Windows malware has infected over 222,000 systems worldwide since at least June 2018, yielding its developer no less than 9,000 Moneros ($2 million) in illegal profits.
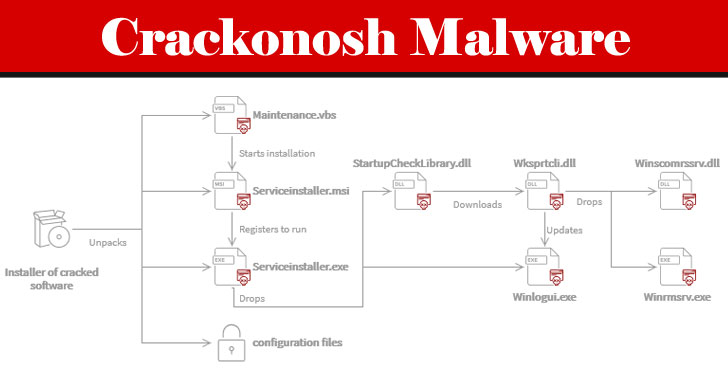
Dubbed "Crackonosh," the malware is distributed via illegal, cracked copies of popular software, only to disable antivirus programs installed in the machine and install a coin miner package called XMRig for stealthily exploiting the infected host's resources to mine Monero.
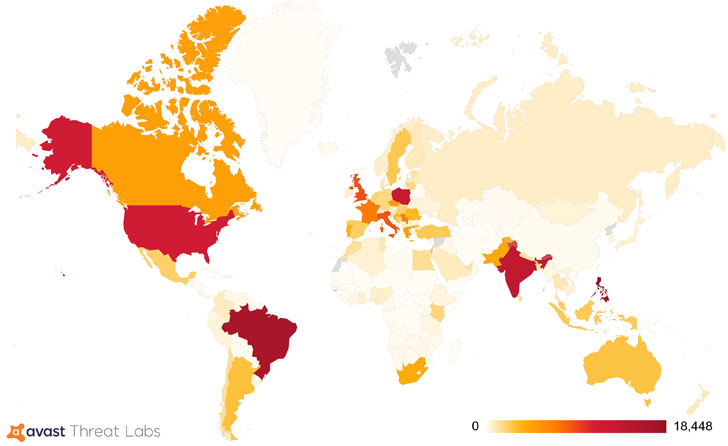
At least 30 different versions of the malware executable have been discovered between Jan. 1, 2018, and Nov. 23, 2020, Czech cybersecurity software company Avast said on Thursday, with a majority of the victims located in the U.S., Brazil, India, Poland, and the Philippines.
Crackonosh works by replacing critical Windows system files such as serviceinstaller.msi and maintenance.vbs to cover its tracks and abuses the safe mode, which prevents antivirus software from working, to delete Windows Defender (and other installed solutions) and turn off automatic updates.
As part of its anti-detection and anti-forensics tactics, the malware also installs its own version of "MSASCuiL.exe" (i.e., Windows Defender), which puts the icon of Windows Security with a green tick to the system tray and runs tests to determine if it's running in a virtual machine.
Last December, security researcher Roberto Franceschetti disclosed that antivirus applications could be disabled by booting into safe mode and renaming their application directories before their corresponding services are launched in Windows.
Microsoft, however, said the issue doesn't "meet the bar for security servicing," noting that the attack is predicated on having administrative/root privileges, adding a "malicious administrator can do much worse things."
The development also comes as a suspected Chinese threat actor behind DirtyMoe and Purple Fox malware were found to have compromised about 100,000 Windows machines as part of an evolving cryptojacking campaign dating all the way back to 2017.
"Crackonosh shows the risks in downloading cracked software," Avast security researcher Daniel Beneš said. "As long as people continue to download cracked software, attacks like these will continue and continue to be profitable for attackers. The key take-away from this is that you really can't get something for nothing and when you try to steal software, odds are someone is trying to steal from you."
- Karlston
-

 1
1



Recommended Comments
There are no comments to display.
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.