Chinese-speaking hackers have been using since at least 2016 malware that lies virtually undetected in the firmware images for some motherboards, one of the most persistent threats commonly known as a UEFI rootkit.
Researchers at cybersecurity company Kaspersky called it CosmicStrand but an earlier variant of the threat was discovered by malware analysts at Qihoo360, who named it Spy Shadow Trojan.
It is unclear how the threat actor managed to inject the rootkit into the firmware images of the target machines but researchers found the malware on machines with ASUS and Gigabyte motherboards.
Mystery UEFI rootkit
The Unified Extensible Firmware Interface (UEFI) software is what connects a computer’s operating system with the firmware of the underlying hardware.
UEFI code is the first to run during a computer’s booting sequence, ahead of the operating system and the security solutions available.
Malware planted in the UEFI firmware image is not only difficult to identify but is also extremely persistent as it cannot be removed by reinstalling the operating system or by replacing the storage drive.
A report from Kaspersky today provides technical details about CosmicStrand, from the infected UEFI component to deploying a kernel-level implant into a Windows system at every boot.
The entire process consists of setting up hooks to modify the operating system loader and take control of the entire execution flow to launch the shellcode that fetches the payload from the command and control server.
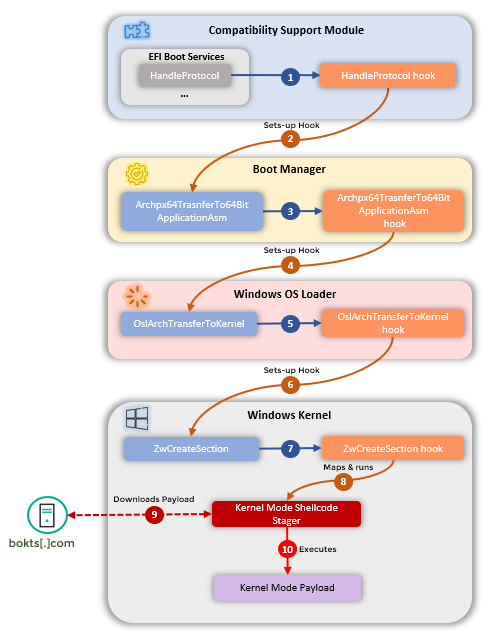
Mark Lechtik, a former Kaspersky reverse engineer, now at Mandiant, who was involved in the research, explains that the compromised firmware images came with a modified CSMCORE DXE driver, which enables a legacy boot process.
“This driver was modified so as to intercept the boot sequence and introduce malicious logic to it,” Lechtik notes in a tweet on Monday.
While the CosmicStrand variant Kaspersky discovered is more recent, researchers at Qihoo360 disclosed in 2017 the first details about an early version of the malware.
The Chinese researchers got to analyzing the implant after a victim reported that their computer had created a new account out of the blue and the antivirus software kept alerting of a malware infection.
According to their report, the compromised system ran on a second-hand ASUS motherboard that the owner had purchased from an online store.
Kaspersky was able to determine that the CosmicStrand UEFI rootkit was lodged in firmware images of Gigabyte or ASUS motherboards that have in common designs using the H81 chipset.
This refers to old hardware between 2013 to 2015 that is mostly discontinued today.
It is unclear how the implant was placed on the infected computers since the process would involve either physical access to the device or through a precursor malware capable of automatically patching the firmware image.
Victims identified by Kaspersky also provide few clues about the threat actor and their objective since the identified infected systems belong to private individuals in China, Iran, Vietnam, and Russia that could not be linked to an organization or industry.
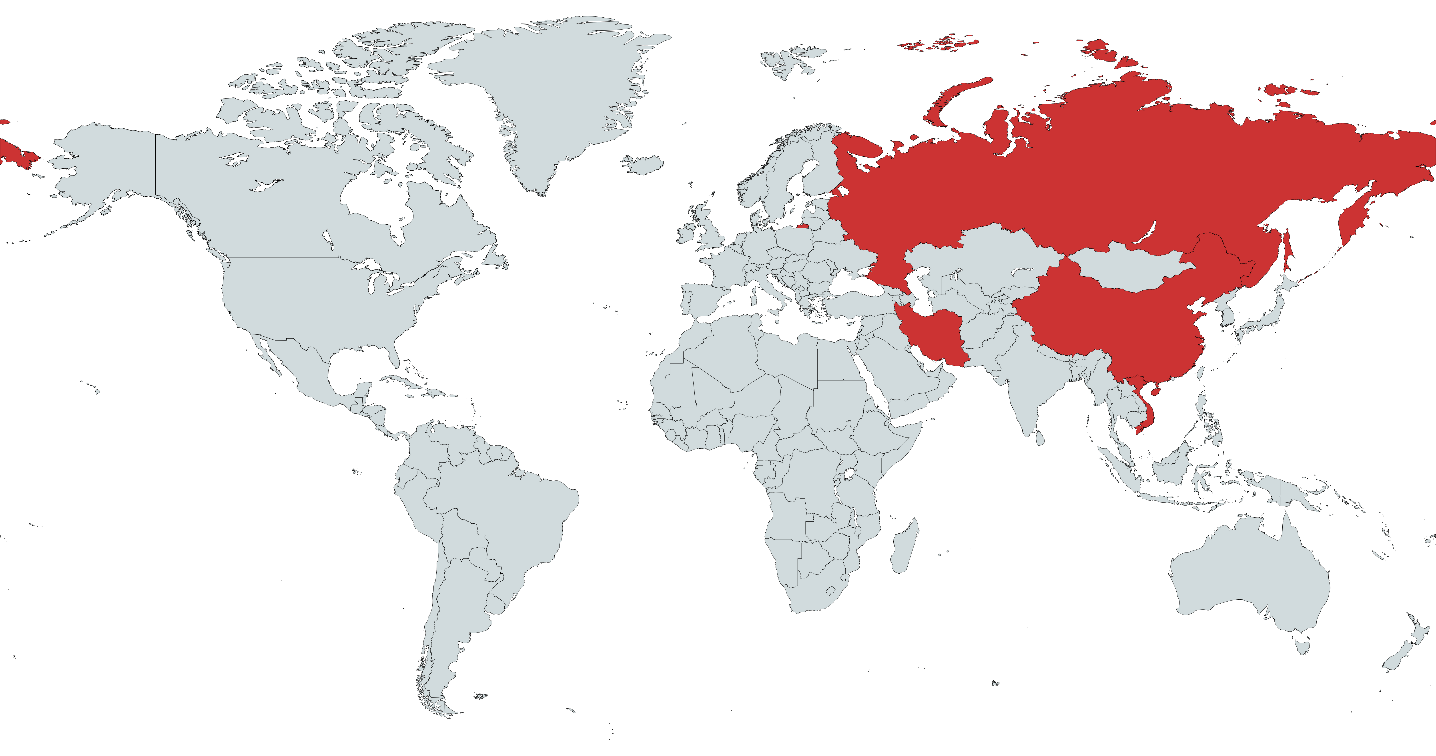
However, the researchers connected CosmicStrand to a Chinese-speaking actor based on code patterns that were also seen in the MyKings cryptomining botnet, where malware analysts at Sophos found Chinese-language artifacts.
Kaspersky says that the CosmicStrand UEFI firmware rootkit can persist on the system for the entire life of the computer and has been used in operations for years, since the end of 2016.
UEFI malware becoming more common
The first widespread report about a UEFI rootkit found in the wild, LoJax, came in 2018 from ESET and it was used in attacks by Russian hackers in the APT28 group (a.k.a. Sednit, Fancy Bear, Sofacy).
Almost four years later and accounts of UEFI malware attacks in the wild have grown more frequent, and it wasn’t just advanced hackers exploring this option:
We learned about MosaicRegressor from Kaspersky in 2020, although it was used in attacks in 2019 against non-governmental organizations.
At the end of 2020 came the news that TrickBot developers had created TrickBoot, a new module that checked compromised machines for UEFI vulnerabilities.
Another UEFI rootkit was revealed in late 2021 to be developed by the Gamma Group as part of their FinFisher surveillance solution.
The same year, details emerged from ESET about yet another bootkit called ESPecter, believed to be used mainly for espionage and with origins as far back as 2012.
MoonBounce, considered to be one of the most sophisticated UEFI firmware implants, was disclosed this year in January as being used by Winnti, a Chinese-speaking hacker group (also known as APT41).
CosmicStrand UEFI malware found in Gigabyte, ASUS motherboards
- flash48
-

 1
1



3175x175(CURRENT).thumb.jpg.b05acc060982b36f5891ba728e6d953c.jpg)
Recommended Comments
There are no comments to display.
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.