Internet infrastructure firm Cloudflare said today that it mitigated a 26 million request per second distributed denial-of-service (DDoS) attack, the largest HTTPS DDoS attack detected to date.
The record-breaking attack occurred last week and targeted one of Cloudflare's customers using the Free plan.
The threat actor behind it likely used hijacked servers and virtual machines seeing that the attack originated from Cloud Service Providers instead of weaker Internet of Things (IoT) devices from compromised Residential Internet Service Providers.
According to Cloudflare, the attacker also used a rather small yet very powerful botnet of 5,067 devices, each capable of generating roughly 5,200 rps when peaking.
"To contrast the size of this botnet, we've been tracking another much larger but less powerful botnet of over 730,000 devices," revealed Cloudflare Product Manager Omer Yoachimik.
"The latter, larger botnet wasn't able to generate more than one million requests per second, i.e., roughly 1.3 requests per second on average per device. Putting it plainly, this botnet was, on average, 4,000 times stronger due to its use of virtual machines and servers.
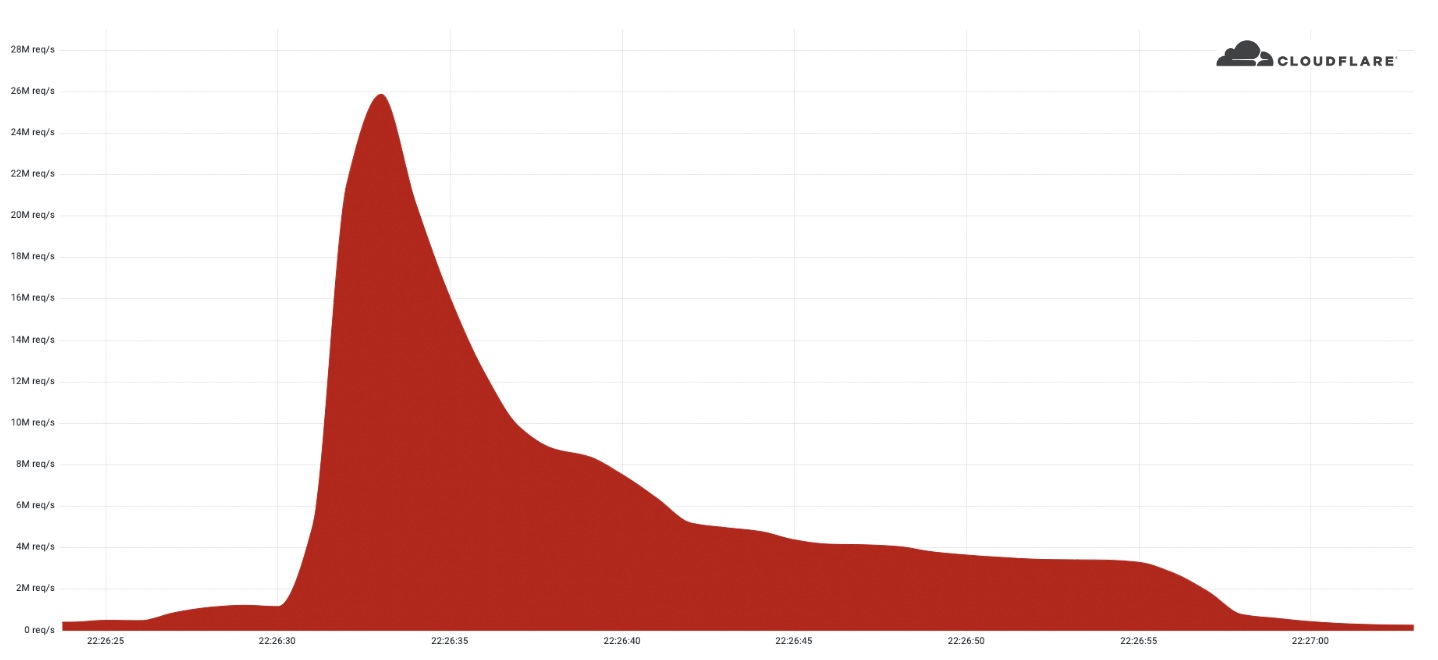
This is one of several massive volumetric attacks detected by Cloudflare throughout the last several years, with the company recording a short-lived HTTP DDoS attack that peaked at 17.2 million requests per second (rps) in August 2021.
The company also mitigated a 15.3 million rps attack in April 2022 that used approximately 6,000 bots to target a Cloudflare customer operating a crypto launchpad.
Also noteworthy is that the June and April attacks were volumetric attacks that used gigantic junk requests to exhaust the targeted server's resources (CPU and RAM) and were both carried out over HTTPS.
"HTTPS DDoS attacks are more expensive in terms of required computational resources because of the higher cost of establishing a secure TLS encrypted connection," Yoachimik explained.
"Therefore, it costs the attacker more to launch the attack, and for the victim to mitigate it. We've seen very large attacks in the past over (unencrypted) HTTP, but this attack stands out because of the resources it required at its scale."
The botnet used in this month's record-high 26 million rps DDoS attack generated over 212 million HTTPS requests within 30 seconds via requests from more than 1,500 networks in 121 countries worldwide.
Microsoft also disclosed that it mitigated in November another massive and record-breaking 3.47 terabits per second (Tbps) DDoS attack that flooded servers used by an Azure customer from Asia with malicious packets.
- aum
-

 1
1



3175x175(CURRENT).thumb.jpg.b05acc060982b36f5891ba728e6d953c.jpg)
Recommended Comments
There are no comments to display.
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.