CloudFlare CDNJS Bug Could Have Led to Widespread Supply-Chain Attacks
Web infrastructure and website security company Cloudflare last month fixed a critical vulnerability in its CDNJS library that's used by 12.7% of all websites on the internet.
CDNJS is a free and open-source content delivery network (CDN) that serves about 4,041 JavaScript and CSS libraries, making it the second most popular CDN for JavaScript after Google Hosted Libraries.
The weakness concerned an issue in the CDNJS library update server that could potentially allow an attacker to execute arbitrary commands, leading to a complete compromise.
The vulnerability was discovered and reported by security researcher RyotaK on April 6, 2021. There is no evidence of in-the-wild attacks abusing this flaw.
Specifically, the vulnerability works by publishing packages to Cloudflare's CDNJS using GitHub and npm, using it to trigger a path traversal vulnerability, and ultimately trick the server into executing arbitrary code, thus achieving remote code execution.
It's worth noting that the CDNJS infrastructure includes features to automate library updates by periodically running scripts on the server to download relevant files from the respective user-managed Git repository or npm package registry.
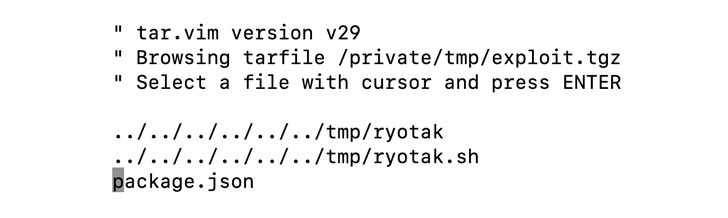
By uncovering an issue with how the mechanism sanitizes package paths, RyotaK found that "arbitrary code can be executed after performing path traversal from the .tgz file published to npm and overwriting the script that is executed regularly on the server."
In other words, the goal of the attack is to publish a new version of a specially-crafted package to the repository, which is then picked up the CDNJS library update server for publishing, in the process copying the contents of the malicious package into a regularly executed script file hosted on the server, thereby gaining arbitrary code execution.
"While this vulnerability could be exploited without any special skills, it could impact many websites," RyotaK said. "Given that there are many vulnerabilities in the supply chain, which are easy to exploit but have a large impact, I feel that it's very scary."
This is not the first time the security researcher has uncovered critical flaws in the way updates to software repositories are handled. In April 2021, RyotaK disclosed a critical vulnerability in the official Homebrew Cask repository could have been exploited by an attacker to execute arbitrary code on users' machines.
- Karlston
-

 1
1



Recommended Comments
There are no comments to display.
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.