The U.S. Cybersecurity and Infrastructure Security (CISA) agency has announced RedEye, an open-source analytic tool for operators to visualize and report command and control (C2) activity.
RedEye is for both red and blue teams, providing an easy way to gauge data that leads to practical decisions.
Assessing attack campaigns
A joint project from CISA and DOE’s Pacific Northwest National Laboratory, RedEye can parse logs from attack frameworks (e.g. Cobalt Strike) to present complex data in a more digestible format.
The tool allows users to upload campaign data to view relevant information such as beacons and commands.
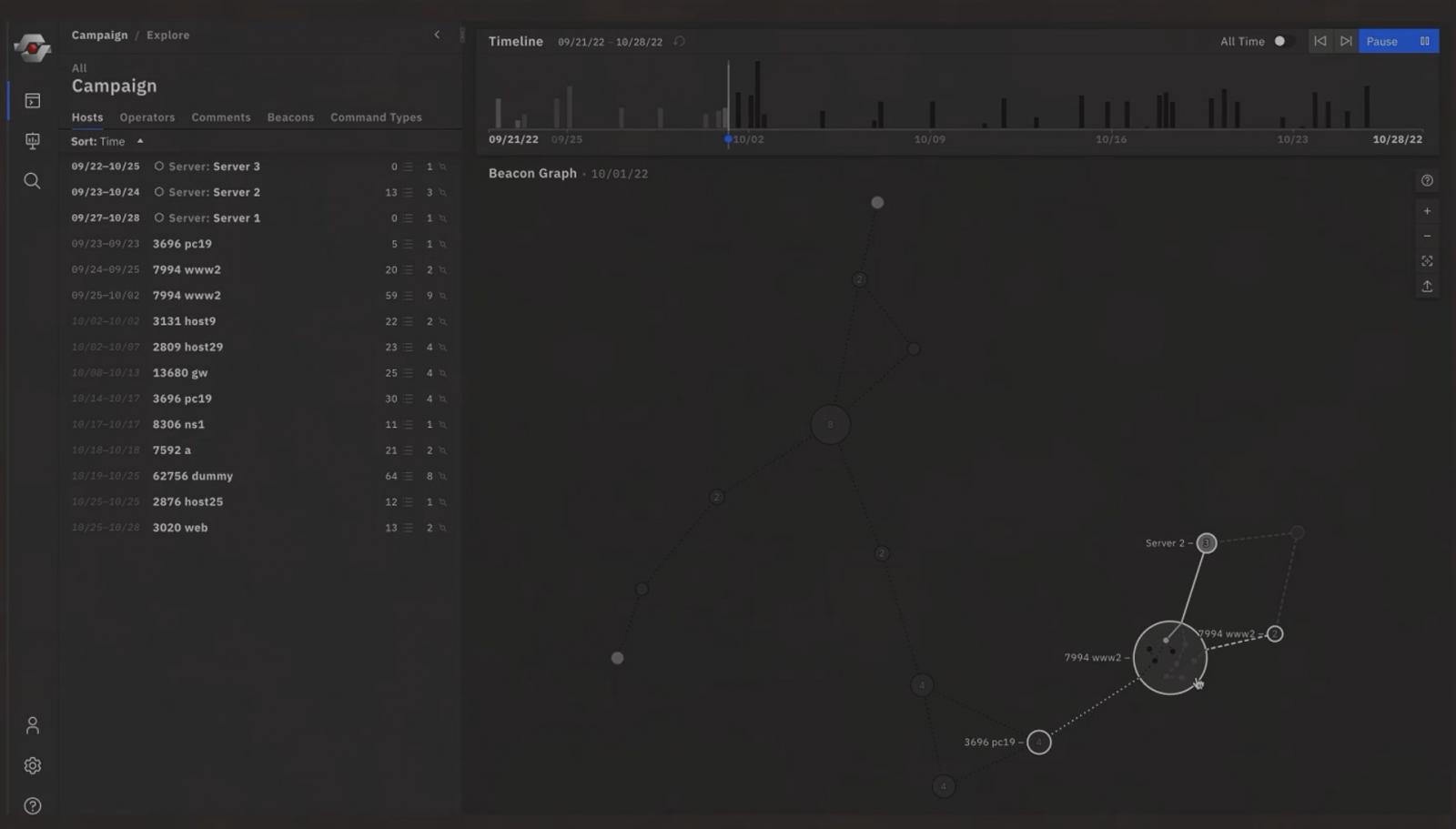
Historical records of each campaign logs loaded into RedEye can be viewed in a graphical representation that correlates servers and hosts involved.
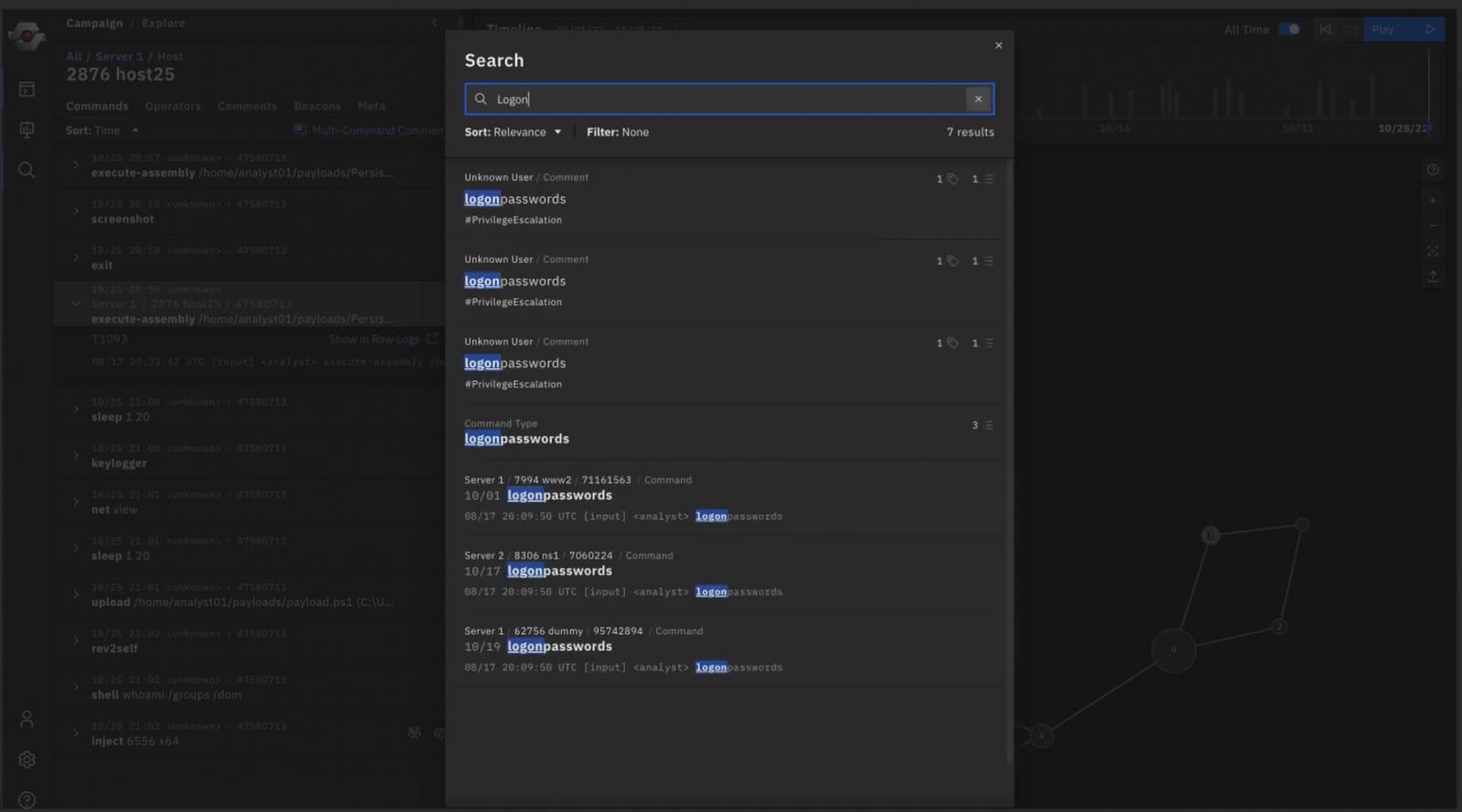
Analysts can also explore key events in a selected campaign to discover payload activity and follow an attacker’s penetration path, such as lateral movement activity or the use of credentials to increase privileges on a machine.
RedEye tool - campaign playback
The features available in RedEye allow analysts to comment on the attacker’s activity for better collaboration and understanding of the attack path.
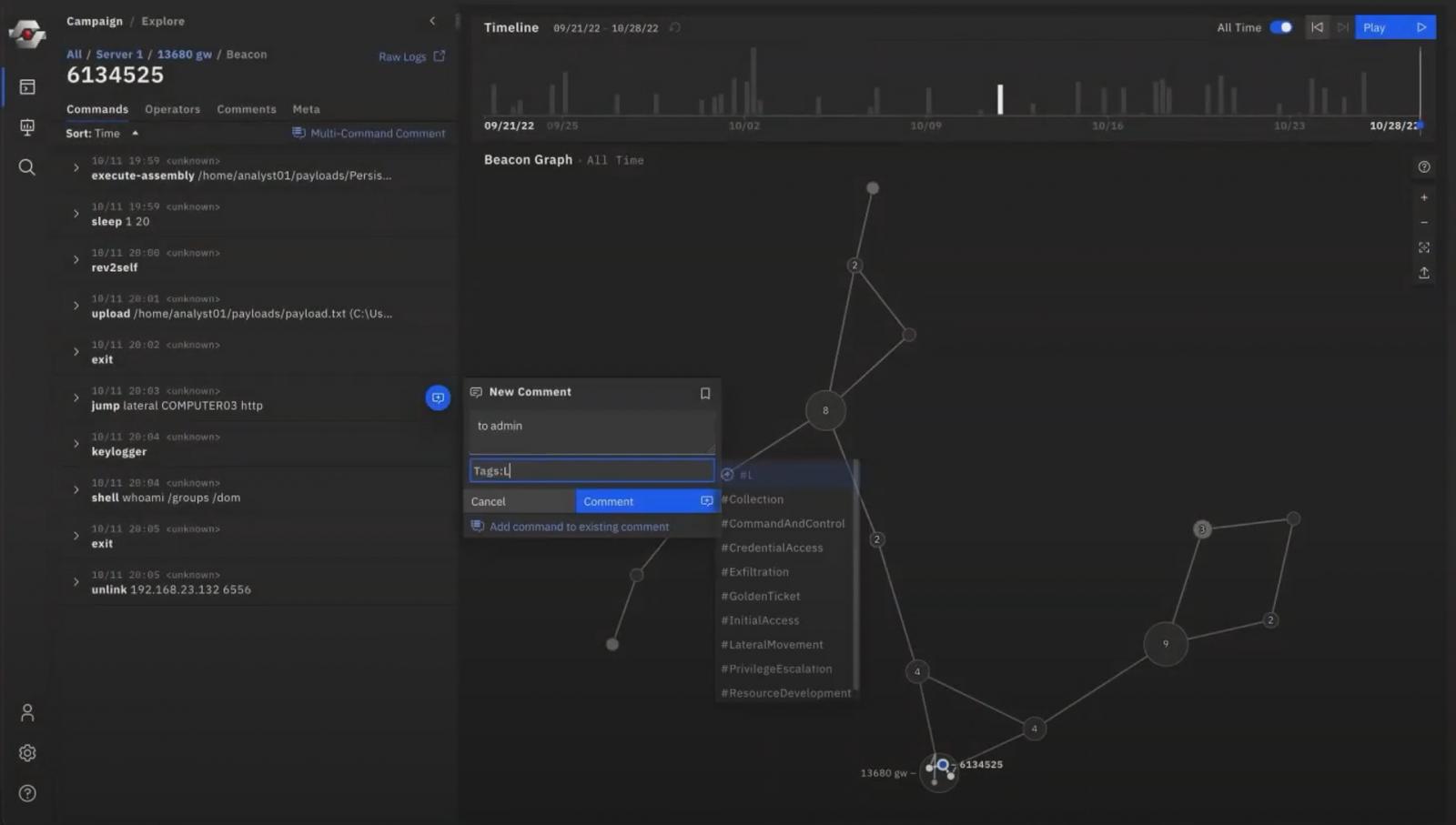
RedEye tool - comment and tags feature
Using the comments from analysts and the techniques used in the campaign, RedEye can also generate presentations that can be shared with stakeholders and clients.
All data collected from a campaign and the comments from analysts can be exported so clients can review
Blue teams can also use RedEye to understand easier the raw data received from an assessment, and view the attack path and the compromised hosts so they can take appropriate action.
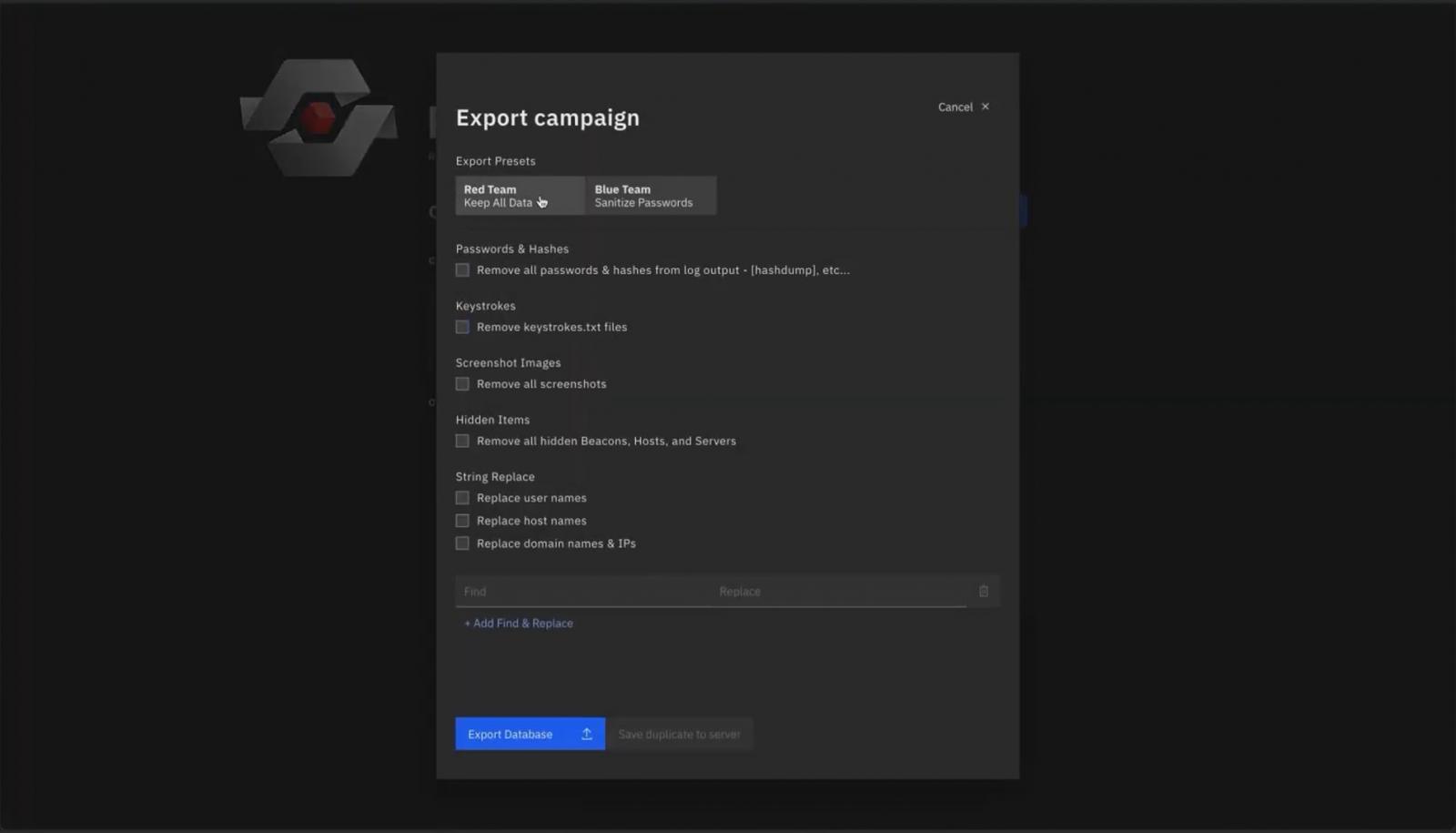
RedEye tool - generate presentations
At the moment, RedEye can parse logs from the Cobalt Strike framework.
It has been tested to work on Linux (Ubuntu 18 and above, Kali Linux 2020.1 or newer), macOS (El Capitan and above), and Windows 7 or newer.
The tool is available on GitHub, in CISA’s repository.
CISA has also released a video, available below, going through the main features avaialble in RedEye:
RedEye is the latest in a set of tools that CISA released as open-source projects over the past few years.
Among them are Malcom - a network traffic analysis tool, ICS NPP - a tool for parsing Industrial Control Systems Network Protocols, Sparrow - a PowerShell script for detecting possible compromised accounts and apps in Azure and Microsoft 365 environments.
- Karlston
-

 1
1




Recommended Comments
There are no comments to display.
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.