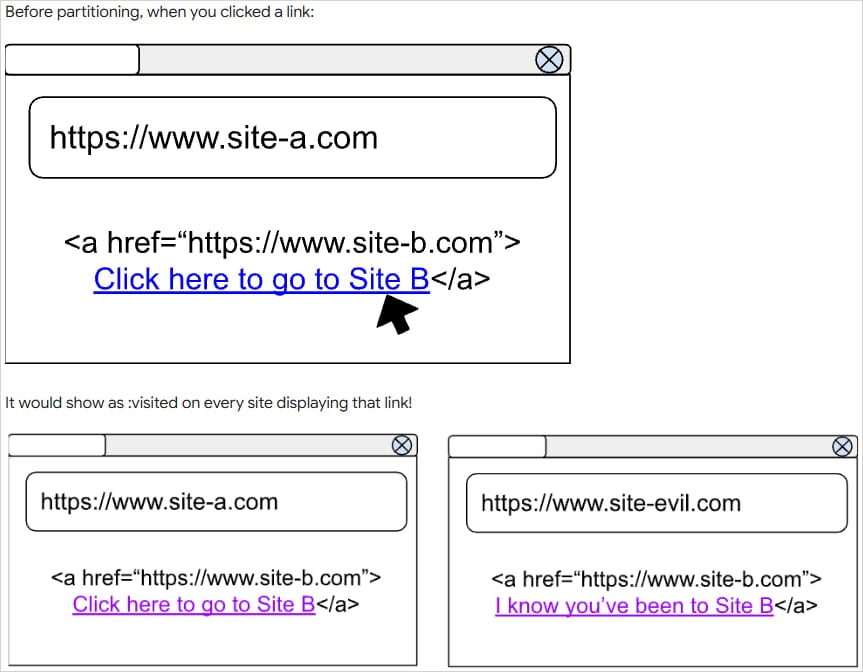
Google is fixing a long-standing privacy issue that, for years, enabled websites to determine users' browsing history through the previously visited links.
The problem arises from allowing sites to style links as ':visited,' meaning showing them as another color instead of the default blue if a user had previously clicked on them.
The system displays this color change regardless of which site they were on when they clicked the link, allowing other sites to potentially use creative scripts that leak the user's browsing history.
Source: Google
The issue isn't just a theoretical privacy concern for users but also introduces a series of real security liabilities that enable tracking, profiling, and phishing.
Researchers demonstrated multiple classes of attacks in the past linked to this privacy gap, including timing, pixel, user interaction, and process-level attacks.
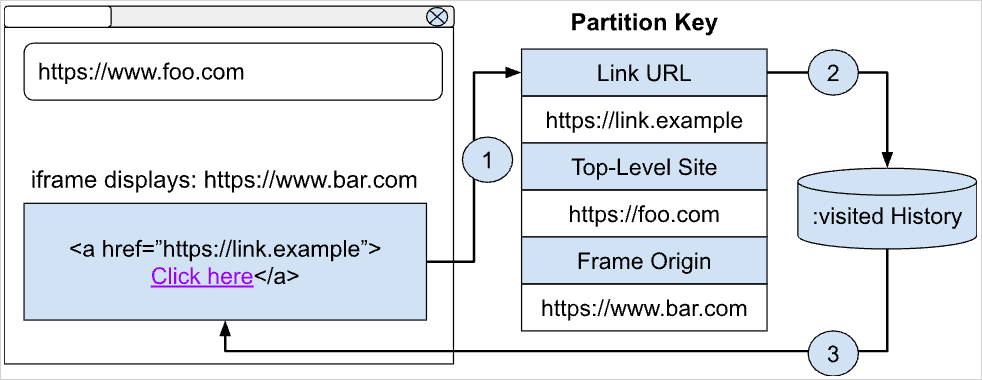
The upcoming release of Google Chrome, version number 136, will finally address the 20-year problem by implementing a triple-key partitioning of "visited" links.
Instead of storing link visits globally, Chrome now partitions each visited link using three keys, namely link URL (link target), top-level site (address bar domain), and frame origin (origin of the frame where the link is rendered).
This ensures that a link will only appear as :visited on the same site and in the same frame origin where the user previously clicked it, eliminating cross-site history leaks.
Source: Google
To preserve usability, Google added a "self-links" exception, so visited links of a site will still be marked as visited on that site even if the user clicked them from a different site.
A website already knows which pages the user has visited, so this exception does not introduce an unwanted history leak.
Google says completely deprecating the :visited selector would eliminate valuable UX cues, so that was ruled out from the proposal's goals. Another rejected solution was to use a permissions-based model, as that would be easy to bypass or even abuse by manipulative websites.
How to enable
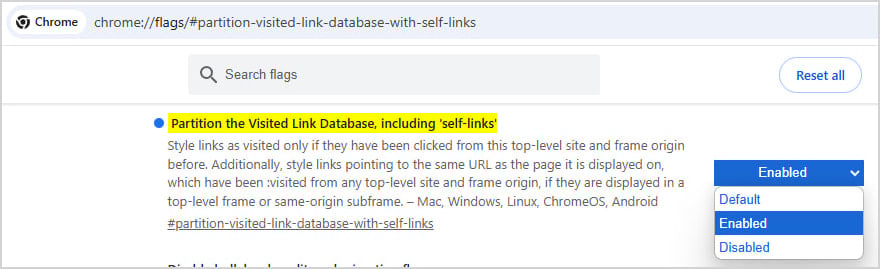
The new :visited isolation was introduced as an experimental feature on Chrome version 132 and is expected to be turned on by default on Chrome 136 (upcoming).
From Chrome 132 to 135 (latest), users can enable the feature by entering chrome://flags/#partition-visited-link-database-with-self-links in the address bar and setting the option to 'enabled.'
Source: BleepingComputer
The feature isn't stable yet, so it might not work as expected in all situations.
On other major browsers the :visited styles risk remains partially unaddressed.
Firefox limits what styles are applied to :visited and blocks JavaScript from reading them, but there's no partitioning to isolate them from sophisticated attack vectors.
Safari also applies restrictions and uses aggressive privacy protections like Intelligent Tracking Prevention, somewhat mitigating the leaks, but there's no partitioning to block all attacks.
Hope you enjoyed this news post.
Thank you for appreciating my time and effort posting news every day for many years.
News posts... 2023: 5,800+ | 2024: 5,700+ | 2025 (till end of March): 1,357
RIP Matrix | Farewell my friend ![]()



3175x175(CURRENT).thumb.jpg.b05acc060982b36f5891ba728e6d953c.jpg)
Recommended Comments
There are no comments to display.
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.