An "extremely sophisticated" Chinese-speaking advanced persistent threat (APT) actor dubbed LuoYu has been observed using a malicious Windows tool called WinDealer that's delivered by means of man-on-the-side attacks.
"This groundbreaking development allows the actor to modify network traffic in-transit to insert malicious payloads," Russian cybersecurity company Kaspersky said in a new report. "Such attacks are especially dangerous and devastating because they do not require any interaction with the target to lead to a successful infection."
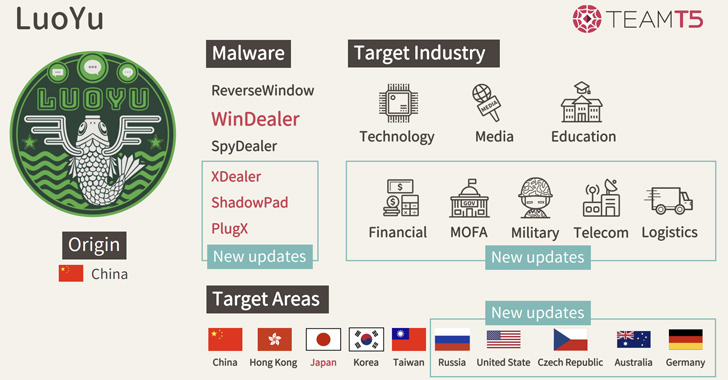
Known to be active since 2008, organizations targeted by LuoYu are predominantly foreign diplomatic organizations established in China and members of the academic community as well as financial, defense, logistics, and telecommunications companies.
LuoYu's use of WinDealer was first documented by Taiwanese cybersecurity firm TeamT5 at the Japan Security Analyst Conference (JSAC) in January 2021. Subsequent attack campaigns have used the malware to target Japanese entities, with isolated infections reported in Austria, Germany, India, Russia, and the U.S.
Other tools that are part of the adversary's malware arsenal include PlugX and its successor ShadowPad, both of which have been used by a variety of Chinese threat actors to enable their strategic objectives. Additionally, the actor is known to target Linux, macOS, and Android devices.
WinDealer, for its part, has been delivered in the past via websites that act as watering holes and in the form of trojanized applications masquerading as instant messaging and video hosting services like Tencent QQ and Youku.
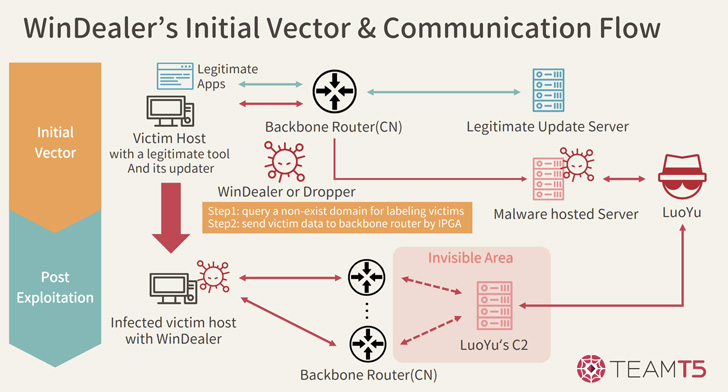
But the infection vector has since been traded for another distribution method that makes use of the automatic update mechanism of select legitimate applications to serve a compromised version of the executable on "rare occasions."
WinDealer, a modular malware platform at its core, comes with all the usual bells and whistles associated with a traditional backdoor, allowing it to hoover sensitive information, capture screenshots, and execute arbitrary commands.
But where it also stands apart is its use of a complex IP generation algorithm to select a command-and-control (C2) server to connect to at random from a pool of 48,000 IP addresses.
"The only way to explain these seemingly impossible network behaviors is by assuming the existence of a man-on-the-side attacker who is able to intercept all network traffic and even modify it if needed," the company said.
A man-on-the-side attack, similar to a man-in-the-middle attack, enables a rogue interloper to read and inject arbitrary messages into a communications channel, but not modify or delete messages sent by other parties.
Such intrusions typically bank on strategically timing their messages such that the malicious reply containing the attacker-supplied data is sent in response to a victim's request for a web resource before the actual response from the server.
The fact that the threat actor is able to control such a massive range of IP addresses could also explain the hijacking of the update mechanism associated with genuine apps to deliver the WinDealer payload, Kaspersky pointed out.
"Man-on-the-side-attacks are extremely destructive as the only condition needed to attack a device is for it to be connected to the internet," security researcher Suguru Ishimaru said.
"No matter how the attack has been carried out, the only way for potential victims to defend themselves is to remain extremely vigilant and have robust security procedures, such as regular antivirus scans, analysis of outbound network traffic, and extensive logging to detect anomalies."




Recommended Comments
There are no comments to display.
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.