A cyberespionage threat actor tracked as Billbug (a.k.a. Thrip, Lotus Blossom, Spring Dragon) has been running a campaign targeting a certificate authority, government agencies, and defense organizations in several countries in Asia.
The most recent attacks were observed since at least March but the actor has been operating stealthily for more than a decade and it is believed to be a state-sponsored group working for China.
Its operations have been documented by multiple cybersecurity companies over the past six years [1, 2, 3].
Security researchers at Symantec say in a report today that Billbug, who they've been tracking since 2018, also targeted a certificate authority company, which would have allowed them to deploy signed malware to make it more difficult to detect or to decrypt HTTPS traffic.
New campaign, old tools
Symantec hasn’t determined how Billbug gains initial access to the target networks but they have seen evidence of this happening by exploiting public-facing apps with known vulnerabilities.
Like in previous campaigns attributed to Billbug, the actor combines tools that are already present on the target system, publicly available utilities, and custom malware. Among them are:
- AdFind
- Winmail
- WinRAR
- Ping
- Tracert
- Route
- NBTscan
- Certutil
- Port Scanner
These tools help hackers blend with innocuous daily activity, avoid suspicious log traces or raising alarms on security tools, and generally make attribution efforts harder.
A more rarely deployed open-source tool seen in recent Billbug operations is Stowaway, a Go-based multi-level proxy tool that helps pentesters bypass network access restrictions.
Symantec was able to pin the recent attacks to Billbug because the threat actor used two custom backdoors seen in some of their previous operations: Hannotog and Sagerunex.
Some functionalities of the Hannotog backdoor include changing firewall settings to enable all traffic, establish persistence on the compromised machine, upload encrypted data, run CMD commands, and download files to the device.
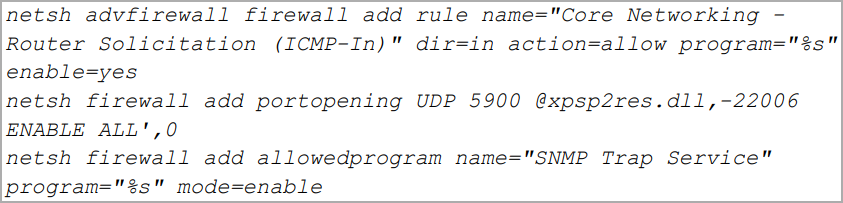
Hannotog changing firewall configuration (Symantec)
Sagerunex is dropped by Hannotog and injects itself in an “explorer.exe” process. It then writes logs on a local temp file encrypted using the AES algorithm (256-bit).
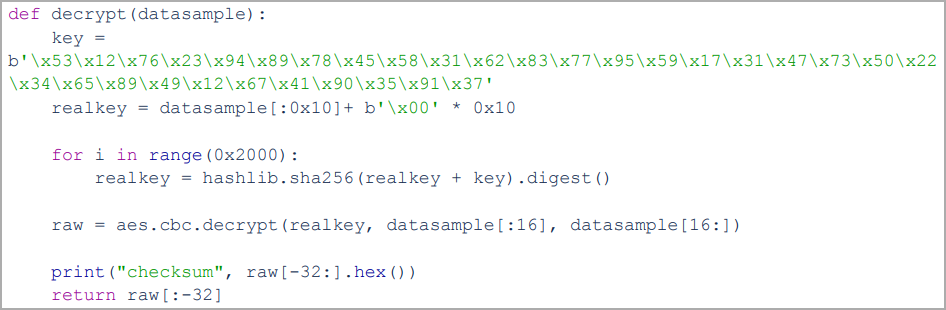
Sagerunex's encryption algorithm (Symantec)
The backdoor’s configuration and state are also stored locally and encrypted with RC4, with the keys for both being hardcoded into the malware.
Sagerunex connects to the command and command server via HTTPS to send a list of active proxies and files, and receives payloads and shell commands from the operators. Moreover, it can execute programs and DLLs using “runexe” and “rundll.”
Billbug continues to use the same custom backdoors with minimal changes over the past years.
- Karlston and aum
-

 2
2




Recommended Comments
There are no comments to display.
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.