China-based threat actors have been targeting Australian government agencies and wind turbine fleets in the South China Sea by directing select individuals to a fake impersonating an Australian news media outlet.
Victims landed on the fraudulent site after receiving phishing emails with enticing lures and received a malicious JavaScript payload from the ScanBox reconnaissance framework.
The campaign was active from April to June this year and targeted people at local and federal Australian Government agencies, Australian news media organizations, and at global heavy industry manufacturers that provide maintenance to wind turbines in the South China Sea.
Security researchers at Proofpoint and PwC (PricewaterhouseCoopers) observing the campaign assess that the objective was cyberespionage. They attribute the activity with moderate confidence to a China-based group tracked as from a threat group tracked as APT40 (a.k.a. TA423, Leviathan, Red Ladon).
ScanBox campaign
ScanBox has been seen in multiple attacks from at least six China-based threat actors in the past and there is sufficient evidence indicating that the toolkit has been used since at least 2014.
.png)
A report from Proofpoint today notes that the phishing emails were delivered to targets in several waves, using Gmail and Outlook email addresses.
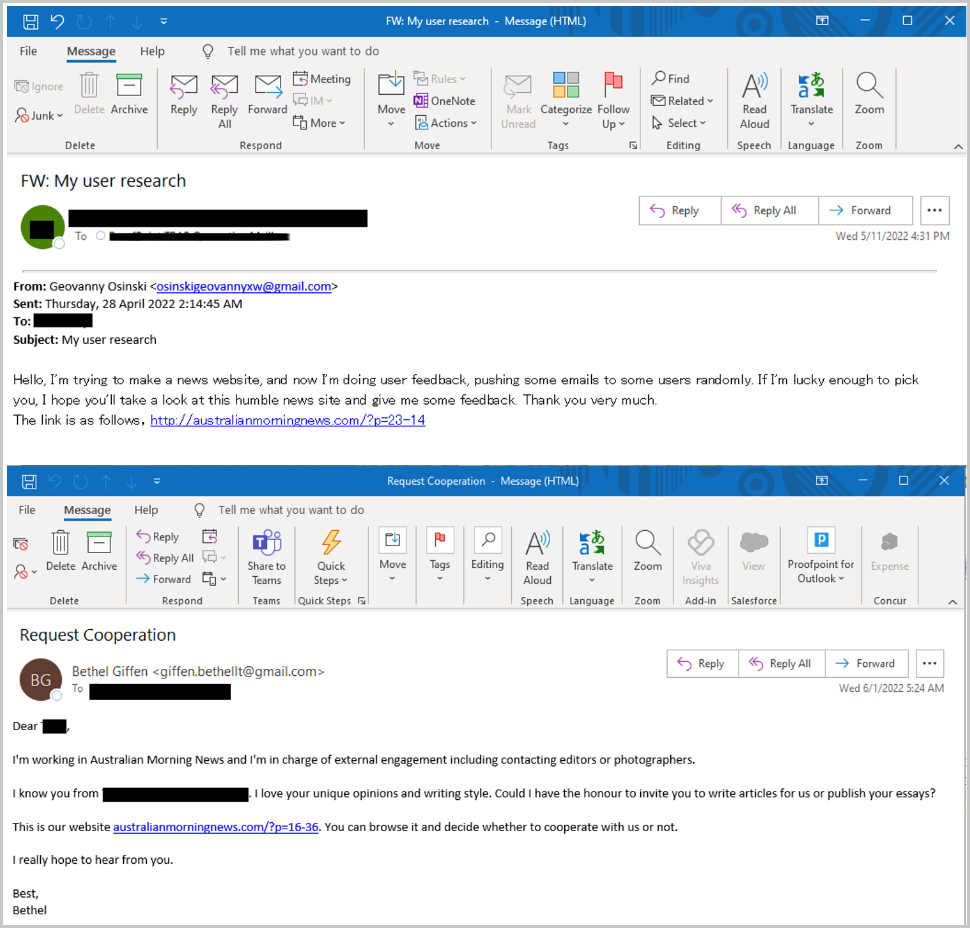
The sender posed as an employee of “Australian Morning News,” a fake media outlet, and added a URL to the malicious website. The site featured content copied from various legitimate news portals.
The URLs also included unique values for each target, the researchers say, although they led to the same page and malicious payload in every instance.
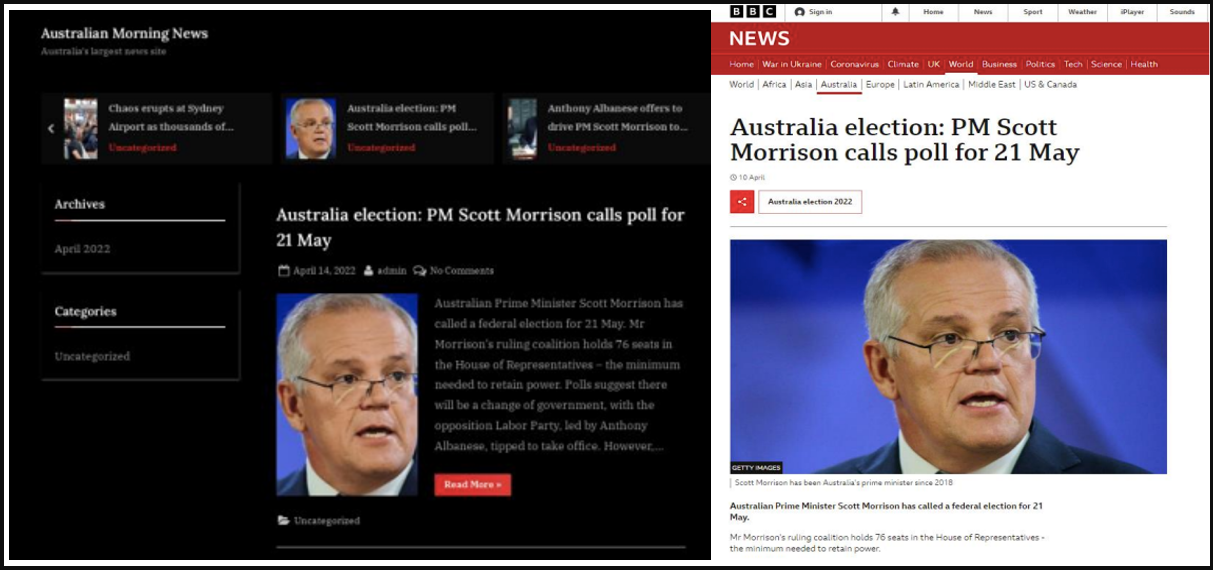
Fake website (left) featuring stolen content from the BCC (Proofpoint)
Visitors of the fake website were served with a copy of the ScanBox framework via JavaScript execution and staged module loading.
“ScanBox can deliver JavaScript code in one single block, or, as is the case in the April 2022 campaign, as a plugin-based, modular architecture,” explains Proofpoint.
.png)
The report further explains that delivering the entire code may be preferable to the threat actors. However, it would risk crashes and errors and it could draw the attention of researchers, so selective plugin loading was chosen.
Modules available in the ScanBox framework include:
- Keylogger: records key presses performed within a ScanBox iframe.
- Browser plugins: identifies installed browser plugins
- Browser fingerprinting: identifies and analyzes victim’s browser technical capabilities
- Peer connection: implements WebRTC to real-time communication over APIs
- Security check: checks if Kaspersky security tools are installed on the victim’s machine
Once the framework has been assembled on the victim’s machine and the selected plugins are loaded, it sets up command and control (C2) communications and begins sending victim profile data, technical details, and information useful for reconnaissance and basic espionage.
In some cases observed in June 2022, the threat actors targeted the Australian Naval Defense, oil and petroleum, and deep water drilling firms using COVID-19 passport services lures that downloaded a DLL stager for loading Meterpreter.
Links to past operations
Based on recent evidence from the targeting methods and tools, Proofpoint concludes that the 2022 campaign is the third phase of the same intelligence-gathering mission APT40 has been carrying out since March 2021.
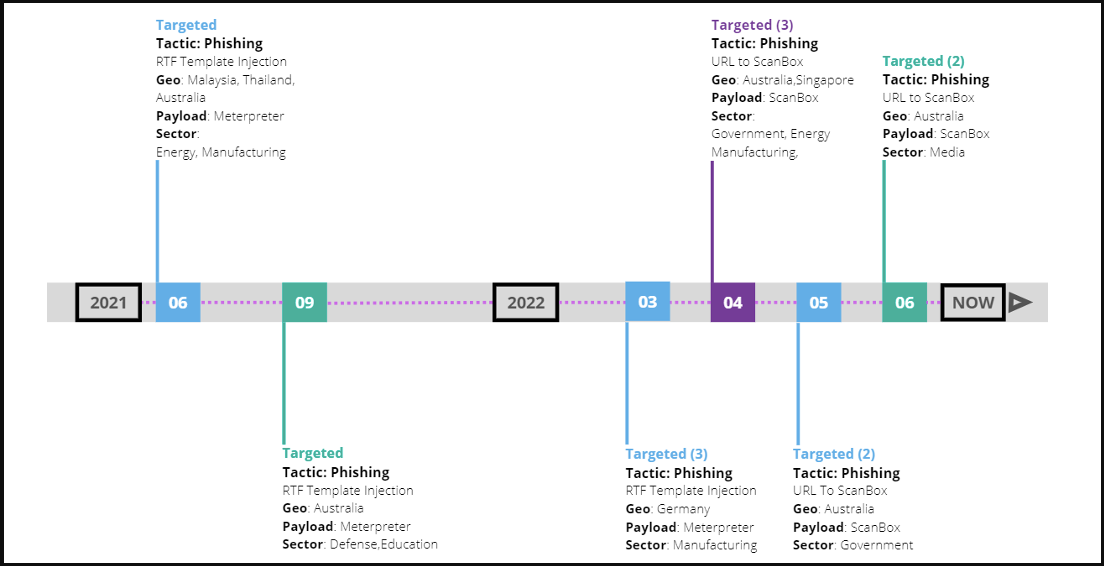
Back then, the threat actors impersonated news outlets like “The Australian” and “Herald Sun”, to perform RTF Template injection and load Meterpreter on the victims’ machines. The use of ScanBox in APT40 campaigns was seen in 2018 too.
The threat actor has an attack history long enough to prompt the U.S. Department of Justice in July 2021 to indict members of APT40.
Source: BleepingComputer
- Karlston and aum
-

 2
2




Recommended Comments
There are no comments to display.
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.