A credit card stealing service is growing in popularity, allowing any low-skilled threat actors an easy and automated way to get started in the world of financial fraud.
Credit card skimmers are malicious scripts that are injected into hacked e-commerce websites that quietly wait for customers to make a purchase on the site.
Once a purchase is made, these malicious scripts steal the credit card details and send them back to remote servers to be collected by threat actors.
Threat actors then use these cards to make their own online purchases or sell the credit card details on dark web marketplaces to other threat actors for as little as a few dollars.
The Caramel skimmer-as-a-service
The new service was discovered by Domain Tools, which states that the platform is operated by a Russian cybercrime organization named “CaramelCorp.”
This service supplies subscribers with a skimmer script, deployment instructions, and a campaign management panel, which is everything a threat actor needs to launch their own credit card stealing campaign.
The Caramel service only sells to Russian-speaking threat actors, using an initial vetting process that excludes those using machine translation or are inexperienced in this field.
A lifetime subscription costs $2,000, which is not cheap for budding threat actors, but promises Russian-speaking hackers full customer support, code upgrades, and evolving anti-detection measures.
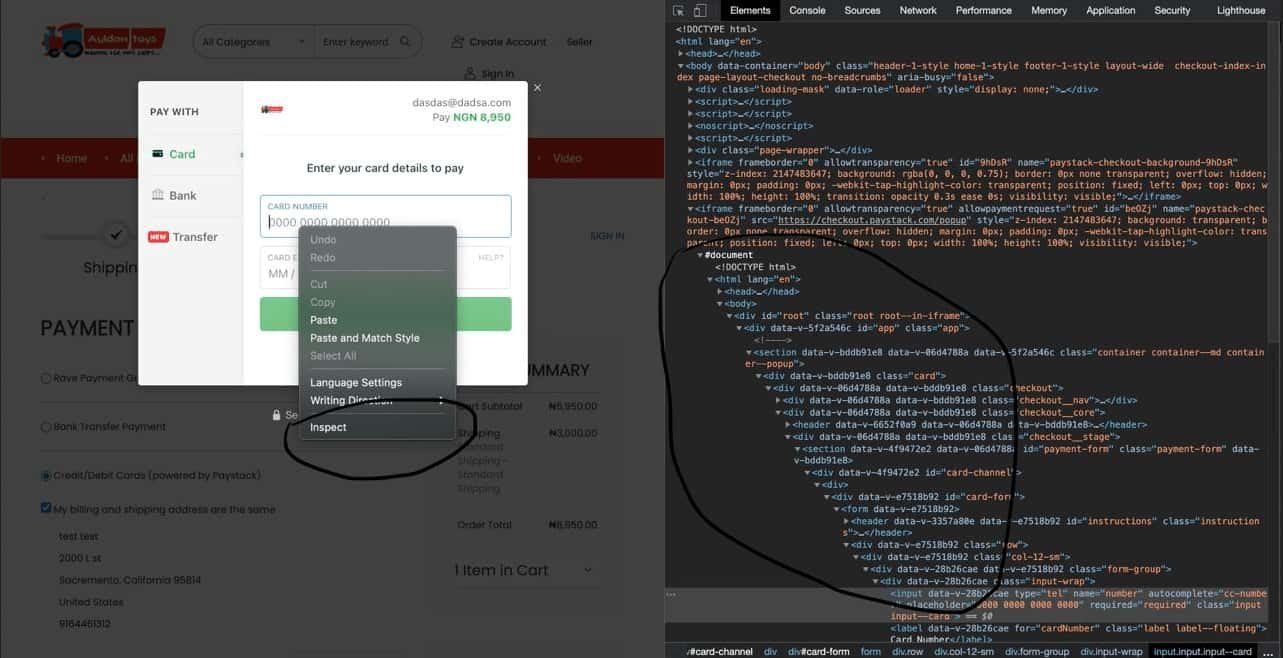
The sellers make unverified claims that Caramel can bypass protection services from Cloudflare, Akamai, Incapsula, and others.
The buyers are provided with a “quick start” guide on JavaScript methods that work particularly well in specific CMS (content management systems).
As the credit card skimming scripts are written in JavaScript, Caramel offers subscribers a variety of obfuscation techniques to prevent them from being easily detected.
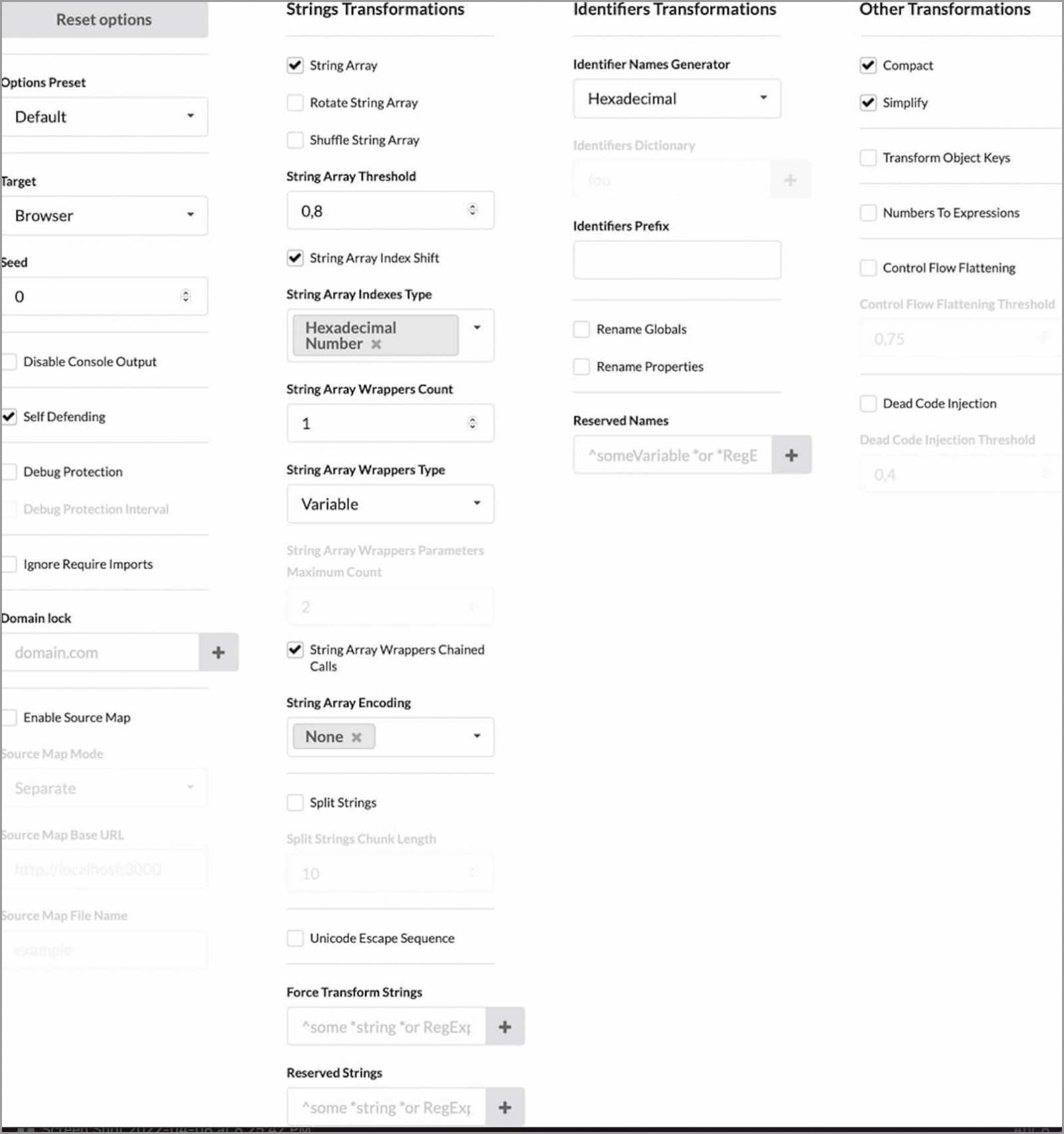
The credit card data collection is done through the “setInterval()” method, which exfiltrates data between fixed periods. While this doesn’t seem like an effective method, it can help steal details of even abandoned carts and incomplete purchases.
Finally, the administration of the campaigns is done through a panel where the subscriber can oversee the compromised e-shops, manage the gateways for the reception of the stolen data, and more.
Operating since 2020
Skimming campaigns aren’t new, and neither is Caramel. Bleeping Computer was able to find the first dark web posts offering the kit for purchase back in December 2020.
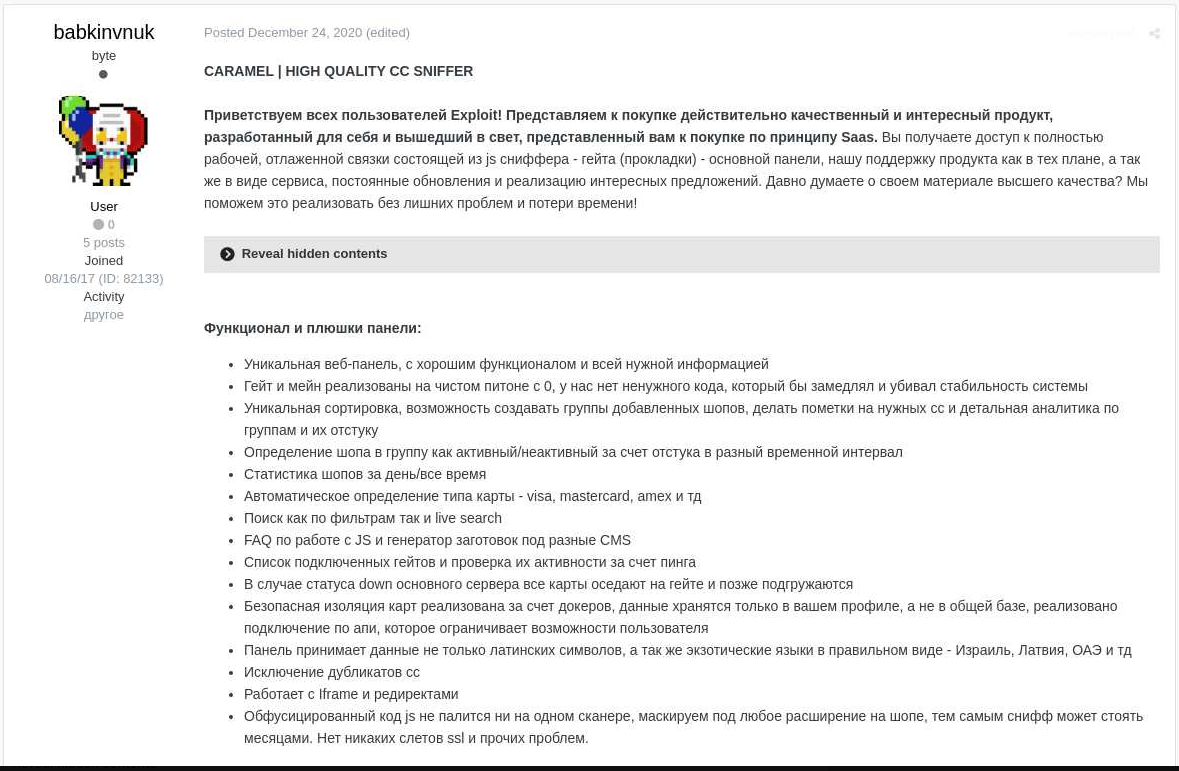
However, continuous development and promotion have helped Caramel grow more popular in the underground community.
The existence of Caramel and other skimming services of this kind removes the technical barrier to setting up and operating large-scale card skimming campaigns, potentially making skimmer campaigns even more common.
For customers of e-commerce platforms, you can protect yourself from credit card skimmers by using one-time private cards, setting up charging limits and restrictions, or just using online payment systems instead of cards.
Caramel credit card stealing service is growing in popularity
- aum, TrojanK and npo33770
-

 3
3



3175x175(CURRENT).thumb.jpg.b05acc060982b36f5891ba728e6d953c.jpg)
Recommended Comments
There are no comments to display.
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.