Last week, a video by security researcher StackSmashing demonstrated an exploit that could break Microsoft's BitLocker drive encryption in "less than 50 seconds" using a custom PCB and a Raspberry Pi Pico.
The exploit works by using the Pi to monitor communication between an external TPM chip and the rest of the laptop, a second-generation ThinkPad X1 Carbon from roughly 2014. The TPM stores the encryption key that unlocks your encrypted disk and makes it readable, and the TPM sends that key to unlock the disk once it has verified that the rest of the PC's hardware hasn't changed since the drive was encrypted. The issue is that the encryption key is sent in plaintext, allowing a sniffer like the one that StackSmashing developed to read the key and then use it to unlock the drive in another system, gaining access to all the data on it.
This is not a new exploit, and StackSmashing has repeatedly said as much. We reported on a similar TPM sniffing exploit in 2021, and there's another from 2019 that similarly used low-cost commodity hardware to pick up a plaintext encryption key over the same low-pin count (LPC) communication bus StackSmashing used. This type of exploit is well-known enough that Microsoft even includes some extra mitigation steps in its own BitLocker documentation; the main new innovation in StackSmashing's demo is the Raspberry Pi component, which is likely part of the reason why outlets like Hackaday and Tom's Hardware picked it up in the first place.
The original video is pretty responsible about how it explains the exploit, and that first wave of re-reporting at least mentioned important details, like the fact that the exploit only works on systems with discrete, standalone TPM chips or that it’s broadly similar to other well-documented, years-old attacks. But as the story has circulated and re-circulated, some reporting has excluded that kind of nuance, essentially concluding that the drive encryption in all Windows PCs can be broken trivially with $10 of hardware and a couple minutes of time. It's worth clarifying what this exploit is and isn't.
What PCs are affected?
BitLocker is a form of full-disk encryption that exists mostly to prevent someone who steals your laptop from taking the drive out, sticking it into another system, and accessing your data without requiring your account password. Many modern Windows 10 and 11 systems use BitLocker by default. When you sign into a Microsoft account in Windows 11 Home or Pro on a system with a TPM, your drive is typically encrypted automatically, and a recovery key is uploaded to your Microsoft account. In a Windows 11 Pro system, you can turn on BitLocker manually whether you use a Microsoft account or not, backing up the recovery key any way you see fit.
Regardless, a potential BitLocker exploit could affect the personal data on millions of machines. So how big of a deal is this new example of an old attack? For most individuals, the answer is probably "not very."
One barrier to entry for attackers is technical: Many modern systems use firmware TPM modules, or fTPMs, that are built directly into most processors. In cheaper machines, this can be a way to save on manufacturing—why buy a separate chip if you can just use a feature of the CPU you're already paying for? In other systems, including those that advertise compatibility with Microsoft's Pluton security processors, it's marketed as a security feature that specifically mitigates these kinds of so-called "sniffing" attacks.
That's because there is no external communication bus to sniff for an fTPM; it's integrated into the processor, so any communication between the TPM and the rest of the system also happens inside the processor. Virtually all self-built Windows 11-compatible desktops will use fTPMs, as will modern budget desktops and laptops. We checked four recent sub-$500 Intel and AMD laptops from Acer and Lenovo, and all used firmware TPMs; ditto for four self-built desktops with motherboards from Asus, Gigabyte, and ASRock.
Ironically, if you're using a high-end Windows laptop, your laptop is slightly more likely to be using a dedicated external TPM chip, which means you might be vulnerable.
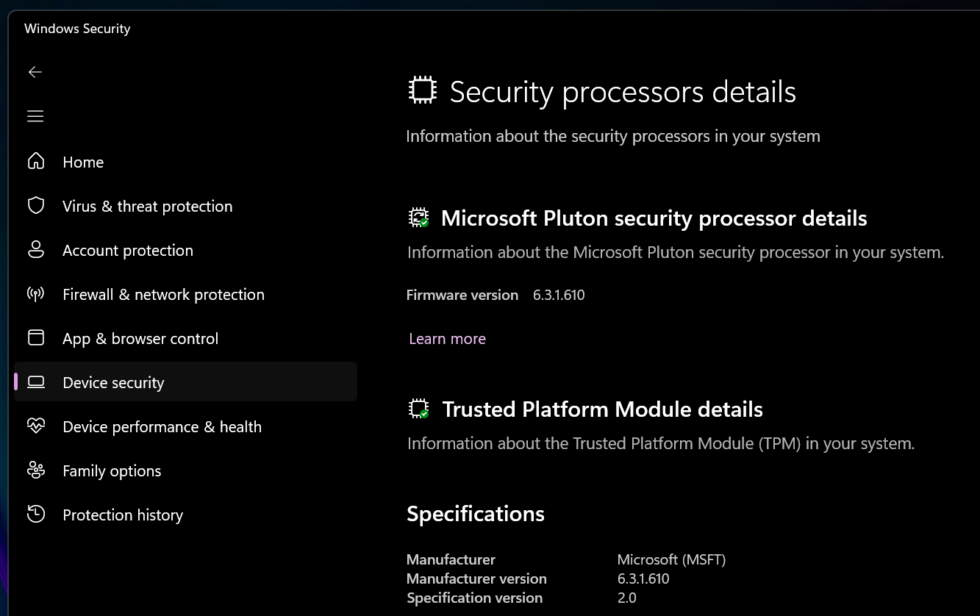
The easiest way to tell what type of TPM you have is to go into the Windows Security center, go to the Device Security screen, and click Security Processor Details. If your TPM's manufacturer is listed as Intel (for Intel systems) or AMD (for AMD systems), you're most likely using your system's fTPM, and this exploit won't work on your system. The same goes for anything with Microsoft listed as the TPM manufacturer, which generally means the computer uses Pluton.
But if you see another manufacturer listed, you're probably using a dedicated TPM. I saw STMicroelectronics TPMs in a recent high-end Asus Zenbook, Dell XPS 13, and midrange Lenovo ThinkPad. StackSmashing also posted photos of a ThinkPad X1 Carbon Gen 11 with a hardware TPM and all the pins someone would need to try to nab the encryption key, as evidence that not all modern systems have switched over to fTPMs—admittedly something I had initially assumed, too. Laptops made before 2015 or 2016 are all virtually guaranteed to be using hardware TPMs when they have them.
That's not to say fTPMs are completely infallible. Some security researchers have been able to defeat the fTPMs in some of AMD's processors with "2–3 hours of physical access to the target device." Firmware TPMs just aren't susceptible to the kind of physical, Raspberry Pi-based attack that StackSmashing demonstrated.



3175x175(CURRENT).thumb.jpg.b05acc060982b36f5891ba728e6d953c.jpg)

Recommended Comments
There are no comments to display.
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.