A new version of the Bumblebee malware loader has been spotted in the wild, featuring a new infection chain that uses the PowerSploit framework for stealthy reflective injection of a DLL payload into memory.
Bumblebee was discovered in April, involved in phishing campaigns believed to be orchestrated by the same actors behind BazarLoader and TrickBot, i.e., the Conti syndicate.
As Bumblebee is an evolved loader with advanced anti-analysis and anti-detection features, it was assumed that it would replace other loaders, such as BazarLoader, in initial compromise attacks followed by ransomware deployment.
Bumblebee's distribution rate reached notable levels in the ensuing months, yet the new loader never became dominant in the field.
According to a report by Cyble, based on a finding by threat researcher Max Malyutin, the authors of Bumblebee are preparing a comeback from the summer hiatus of spam operations, using a new execution flow.
Execution from memory
Previously, Bumblebee reached victims via emails carrying password-protected zipped ISO files that contained an LNK (for executing the payload) and a DLL file (the payload).
In the recent attack, Bumblebee replaced the ISO with a VHD (Virtual Hard Disk) file, which, again, contains an LNK shortcut file (Quote).
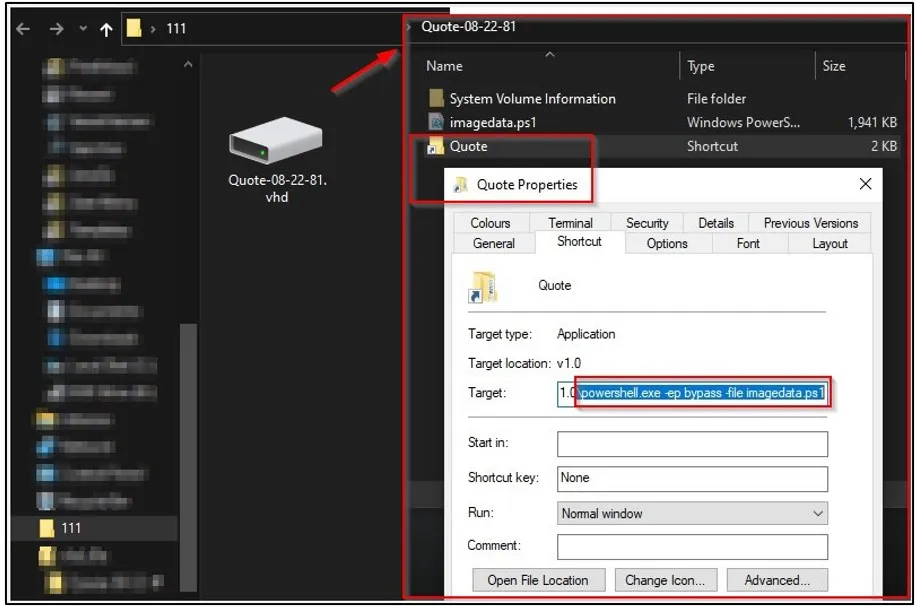
Instead of executing Bumblebee (DLL) directly, the LNK now executes "imagedata.ps1," which launches a PowerShell window and hides it from the user by abusing the 'ShowWindow' command.
The SP1 script is obfuscated using Base64 and string concatenation to evade AV detection while loading the second stage of the PowerShell loader.
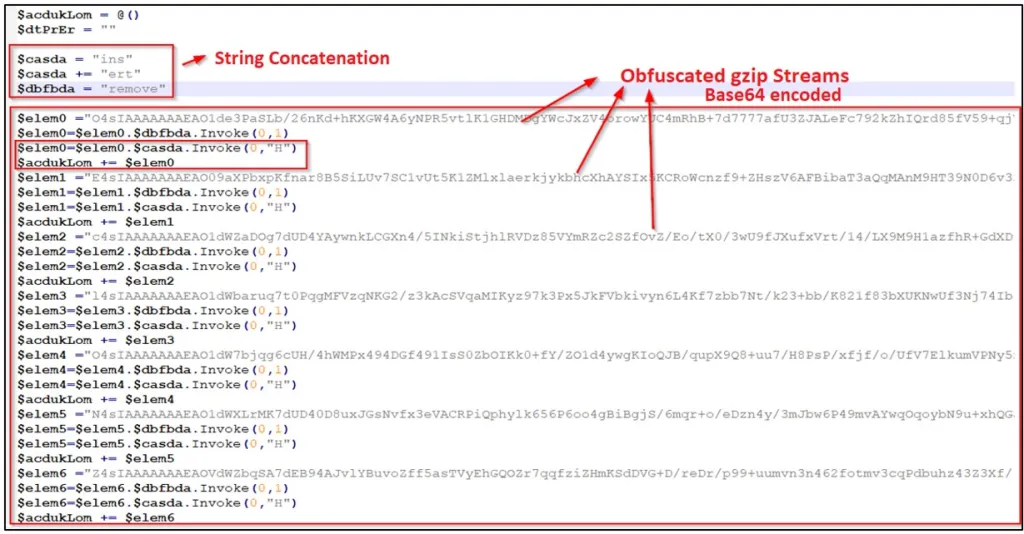
The second stage features the same obfuscation as the first and contains the PowerSploit module to load the 64-bit malware (LdrAddx64.dll) into the memory of the PowerShell process using reflective injection.
"PowerSploit is an open-source post-exploitation framework in which the malware uses a method, Invoke-ReflectivePEInjection, for reflectively loading the DLL into the PowerShell Process," explains Cyble in the report.
"This method validates the embedded file and performs multiple checks to ensure that the file is loaded properly on the executing system."
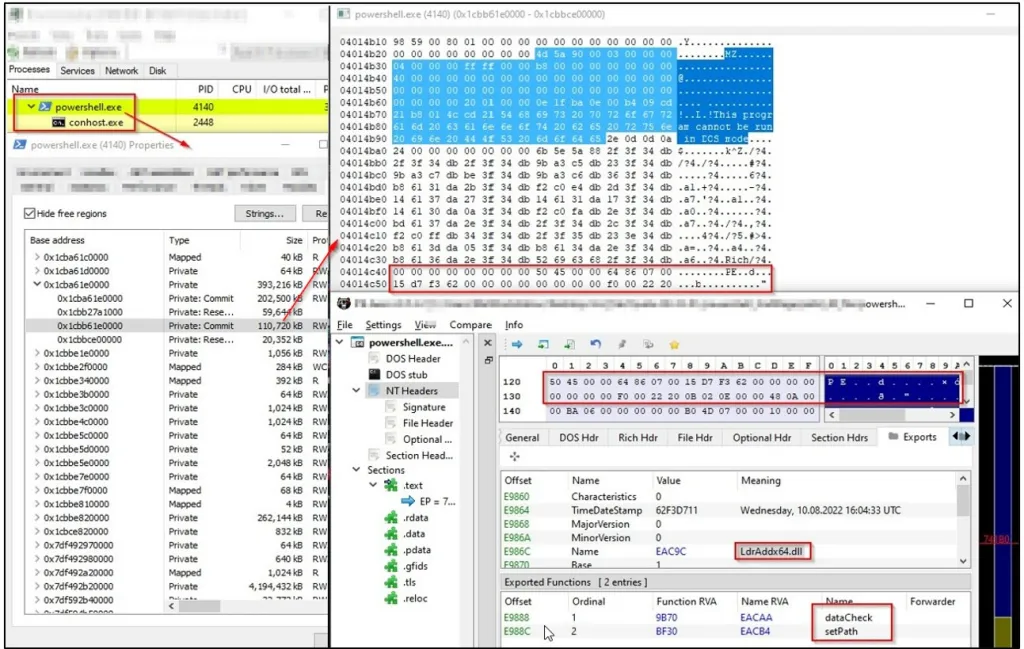
With the new loading flow, Bumblebee loads from memory and never touches the host's disk, thus minimizing the chances of being detected and stopped by anti-virus tools.
By increasing its stealthiness, Bumblebee becomes a more potent initial access threat and increases its chances of enticing ransomware and malware operators looking for ways to deploy their payloads.
Source: Bleeping Computer




Recommended Comments
There are no comments to display.
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.