Researchers have uncovered advanced, never-before-seen macOS malware that was installed using exploits that were almost impossible for most users to detect or stop once the users landed on a malicious website.
The malware was a full-featured backdoor that was written from scratch, an indication that the developers behind it have significant resources and expertise. DazzleSpy, as researchers from security firm Eset have named it, provides an array of advanced capabilities that give the attackers the ability to fully monitor and control infected Macs. Features include:
- victim device fingerprinting
- screen capture
- file download/upload
- execute terminal commands
- audio recording
- keylogging
Deep pockets, top-notch talent
Mac malware has become more common over the years, but the universe of advanced macOS backdoors remains considerably smaller than that of advanced backdoors for Windows. The sophistication of DazzleSpy—as well as the exploit chain used to install it—is impressive. It also doesn’t appear to have any corresponding counterpart for Windows. This has led Eset to say that the people who developed DazzleSpy are unusual.
“First, they seem to be targeting Macs only,” Eset researcher Marc-Etienne M.Léveillé wrote in an email. “We haven’t seen payloads for Windows nor clues that it would exist. Secondly, they have the resources to develop complex exploits and their own spying malware, which is quite significant.”
Indeed, researchers from Google’s threat analysis group who first uncovered the exploits said that, based on their analysis of the malware, they “believe this threat actor to be a well-resourced group, likely state-backed, with access to their own software engineering team based on the quality of the payload code.”
As the Google researchers first noted, the malware was spread in watering-hole attacks that used both fake and hacked sites appealing to pro-democracy activists in Hong Kong. The attacks exploited vulnerabilities that, when combined, gave the attackers the ability to remotely execute code of their choice within seconds of a victim visiting the booby-trapped webpage. All that was required for the exploit to work was for someone to visit the malicious site. No other user action was required, making this a one-click attack.
“That’s kind of the scary part: on an unpatched system the malware would start to run with administrative privileges without the victim noticing,” M.Léveillé said. “Traffic to the C&C server is also encrypted using TLS.”
Apple has since patched the vulnerabilities exploited in this attack.
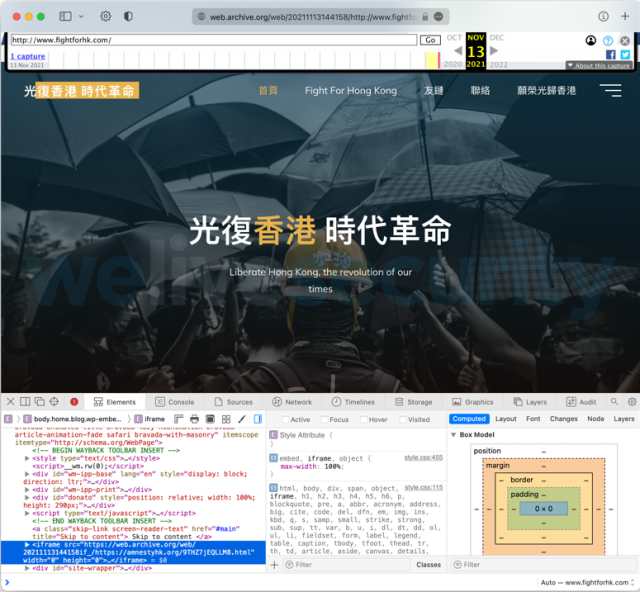
The exploit chain consisted of a code-execution vulnerability in Webkit, the browser engine for Apple Safari. Eset researchers analyzed one of the watering-hole sites, which was taken down but remains cached in the Internet Archives. The site contained a simple iframe tag that connected to a page at amnestyhk[.]org.



3175x175(CURRENT).thumb.jpg.b05acc060982b36f5891ba728e6d953c.jpg)

Recommended Comments
There are no comments to display.
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.