The BlackByte ransomware gang is using a new technique that researchers are calling "Bring Your Own Driver," which enables bypassing protections by disabling more than 1,000 drivers used by various security solutions.
Recent attacks attributed to this group involved a version of the MSI Afterburner RTCore64.sys driver, which is vulnerable to a privilege escalation and code execution flaw tracked as CVE-2019-16098.
Exploiting the security issue allowed BlackByte to disable drivers that prevent multiple endpoint detection and response (EDR) and antivirus products from operating normally.
The “Bring Your Own Vulnerable Driver” (BYOVD) method is effective because the vulnerable drivers are signed with a valid certificate and run with high privileges on the system.
Two notable recent examples of BYOVD attacks include Lazarus abusing a buggy Dell driver and unknown hackers abusing an anti-cheat driver/module for the Genshin Impact game.
Attack details
Security researchers at cybersecurity company Sophos explain that the abused MSI graphics driver offers I/O control codes directly accessible by user-mode processes, which violates Microsoft’s security guidelines on kernel memory access.
This makes it possible for attackers to read, write, or execute code in kernel memory without using shellcode or an exploit.
In the first stage of the attack, BlackByte identifies the kernel version to select the correct offsets that match the kernel ID.
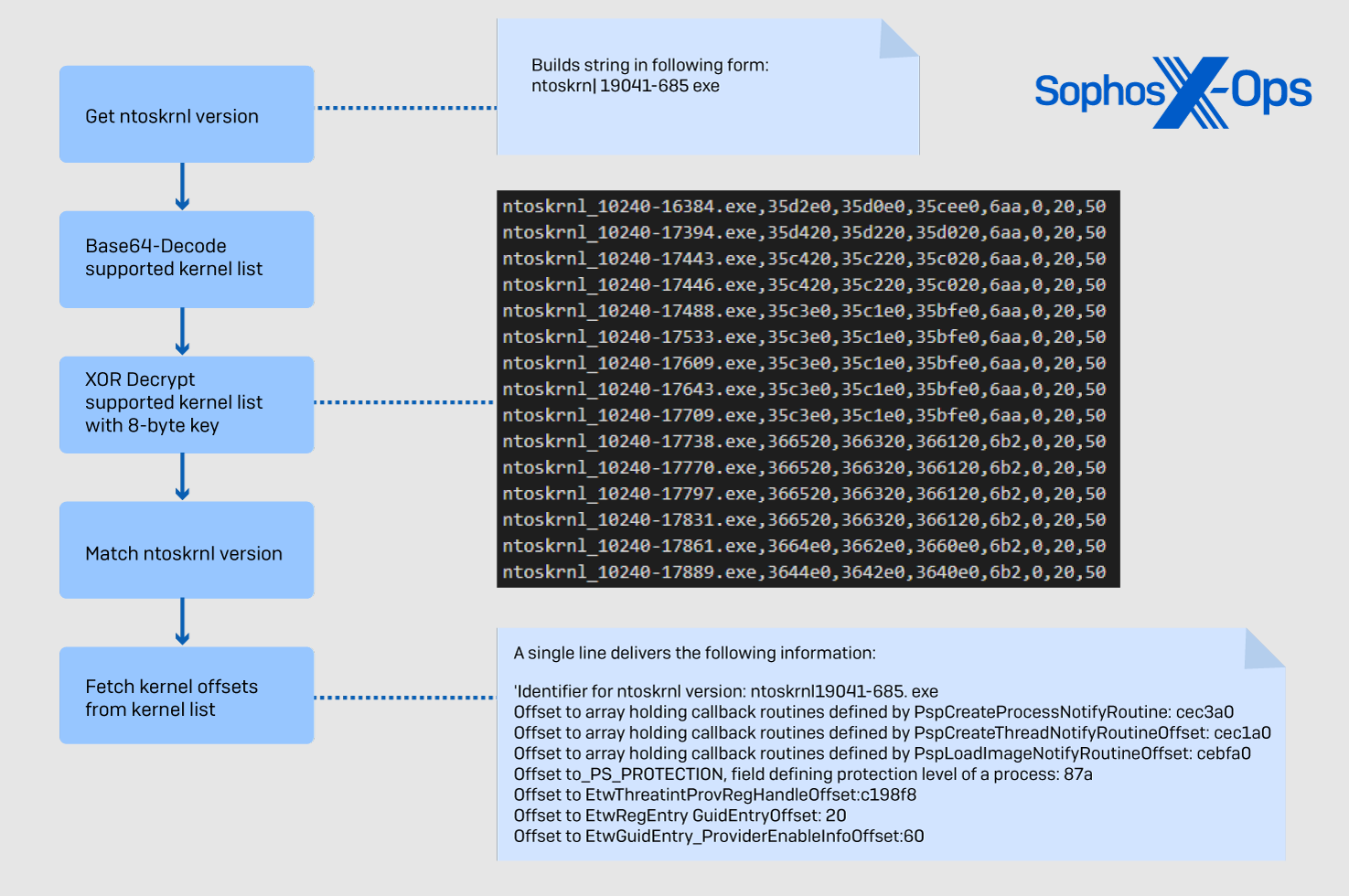
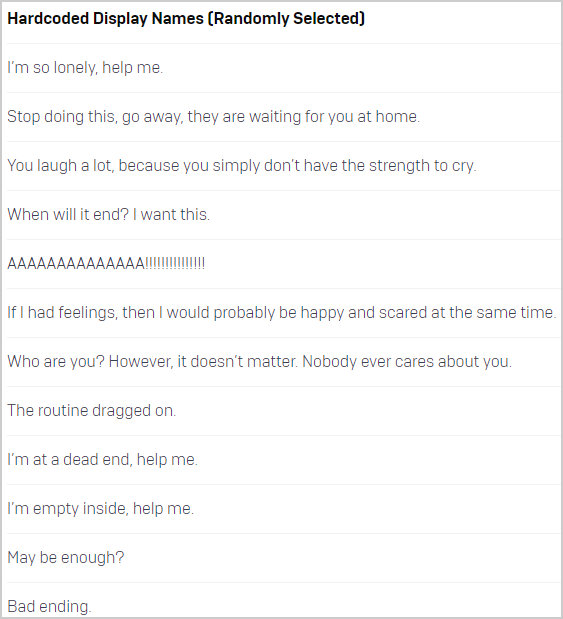
Next, RTCore64.sys is dropped in “AppData\Roaming” and creates a service using a hardcoded name and a randomly selected, not-so-subtle display name.
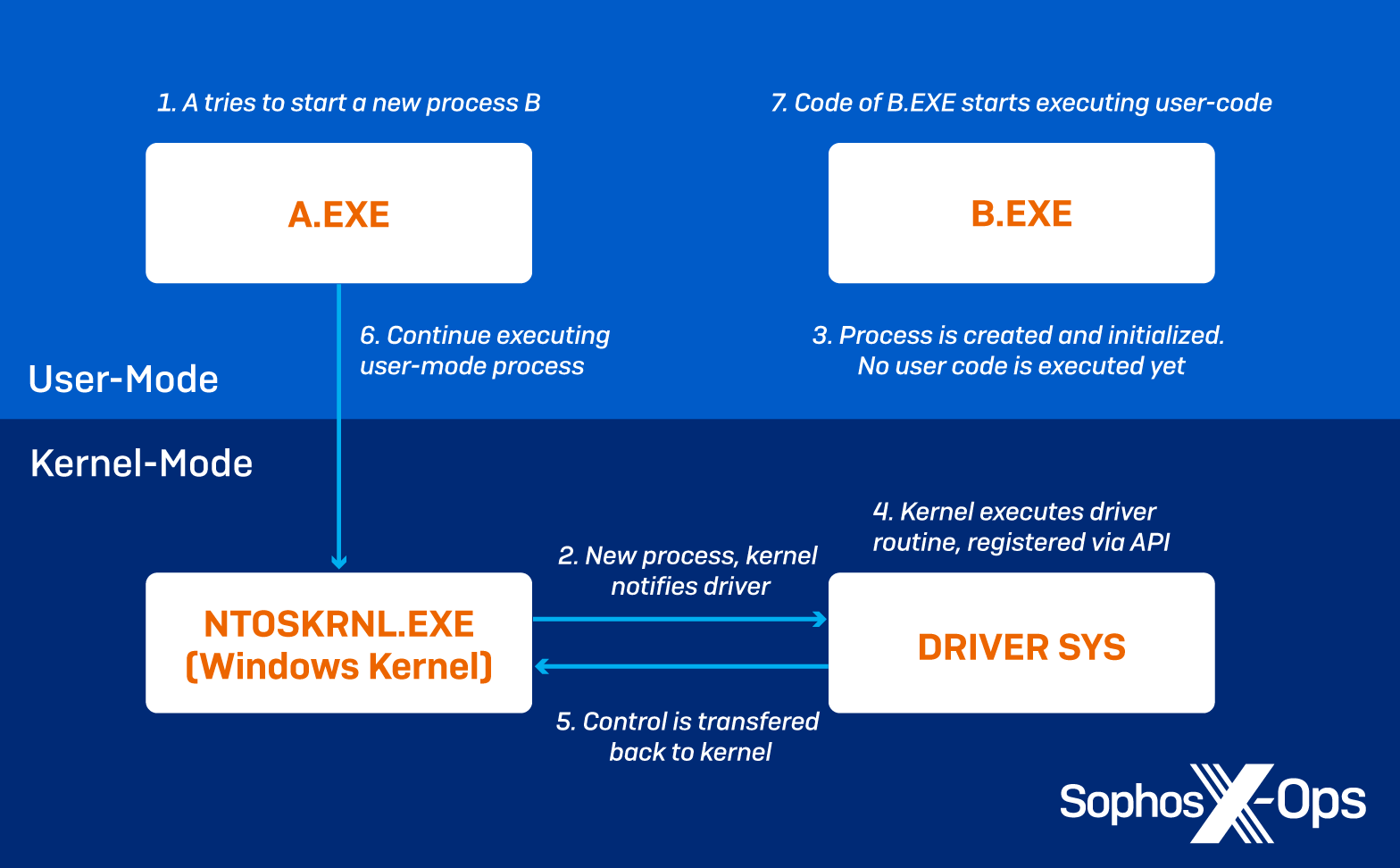
The attackers then exploit the driver’s vulnerability to remove Kernel Notify Routines that correspond to security tool processes.
The retrieved callback addresses are used to derive the corresponding driver name and compared to a list of 1,000 targeted drivers that support the function of AV/EDR tools.
Any matches found in this stage are removed by overwriting the element that holds the address of the callback function with zeros, so the targeted driver is nullified.
Sophos also highlights several methods that BlackByte employs in these attacks to evade analysis from security researchers, like seeking for signs of a debugger running on the target system and quitting.
The BlackByte malware also checks for a list of hooking DLLs used by Avast, Sandboxie, Windows DbgHelp Library, and Comodo Internet Security, and terminates its execution if found.
System administrators can protect against BlackByte’s new security bypassing trick by adding the particular MSI driver to an active blocklist.
Additionally, admins should monitor all driver installation events and scrutinize them frequently to find any rogue injections that don’t have a hardware match.
- aum and Karlston
-

 2
2




Recommended Comments
There are no comments to display.
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.