BIOS Disconnect: New High-Severity Bugs Affect 128 Dell PC and Tablet Models
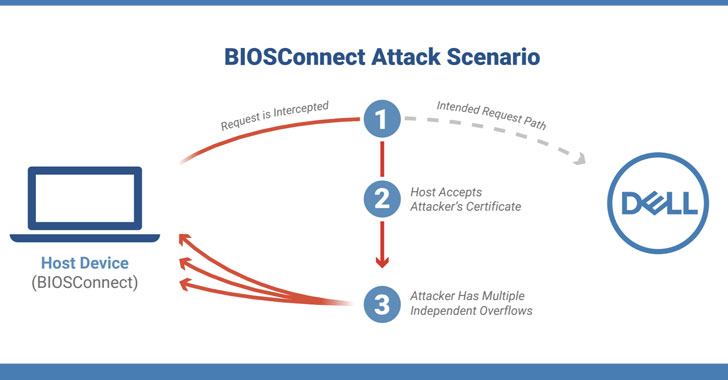
Cybersecurity researchers on Thursday disclosed a chain of vulnerabilities affecting the BIOSConnect feature within Dell Client BIOS that could be abused by a privileged network adversary to gain arbitrary code execution at the BIOS/UEFI level of the affected device.
"As the attacker has the ability to remotely execute code in the pre-boot environment, this can be used to subvert the operating system and undermine fundamental trust in the device," researchers from enterprise device security firm Eclypsium said. "The virtually unlimited control over a device that this attack can provide makes the fruit of the labor well worth it for the attacker."
In all, the flaws affect 128 Dell models spanning across consumer and business laptops, desktops, and tablets, totalling an estimated 30 million individual devices. Worse, the weaknesses also impact computers that have Secure Boot enabled, a security feature designed to prevent rootkits from being installed at boot time in memory.
BIOSConnect offers network-based boot recovery, allowing the BIOS to connect to Dell's backend servers via HTTPS to download an operating system image, thereby enabling users to recover their systems when the local disk image is corrupted, replaced, or absent.
Successful exploitation of the flaws could mean loss of device integrity, what with the attacker capable of remotely executing malicious code in the pre-boot environment that could alter the initial state of the operating system and break OS-level security protections.
The list of four flaws uncovered by Eclypsium is as follows —
- CVE-2021-21571 - Insecure TLS connection from BIOS to Dell, allowing a bad actor to stage a impersonate Dell.com and delivery malicious code back to the victim's device
- CVE-2021-21572, CVE-2021-21573, and CVE-2021-21574 - Overflow vulnerabilities enabling arbitrary code execution
The combination of remote exploitation as well the ability to gain control over the most privileged code on the device could make such vulnerabilities a lucrative target for attackers, the researchers said.
The issues were reported to Dell by the Oregon-based company on March 3, following which server-side updates were rolled out on May 28 to remediate CVE-2021-21573 and CVE-2021-21574. Dell has also released client-side BIOS firmware updates to address the remaining two flaws.
Additionally, the PC maker has released workarounds to disable both the BIOSConnect and HTTPS Boot features for customers who are unable to apply the patches immediately.
"Successfully compromising the BIOS of a device would give an attacker a high degree of control over a device," Eclypsium researchers said. "The attacker could control the process of loading the host operating system and disable protections in order to remain undetected. This would allow an attacker to establish ongoing persistence while controlling the highest privileges on the device."
- Karlston
-

 1
1



Recommended Comments
There are no comments to display.
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.