Avast has released a decryptor for variants of the Hades ransomware known as 'MafiaWare666', 'Jcrypt', 'RIP Lmao', and 'BrutusptCrypt,' allowing victims to recover their files for free.
The security company says it discovered a flaw in the encryption scheme of the Hades strain, allowing some of the variants to be unlocked. However, this may not apply to newer or unknown samples that use a different encryption system.
Utilizing Avast's tool, victims of the supported ransomware variants can decrypt and access their files again without paying a ransom to the attackers, which ranges between $50 and $300. However, ransom demands reached tens of thousands in some cases.
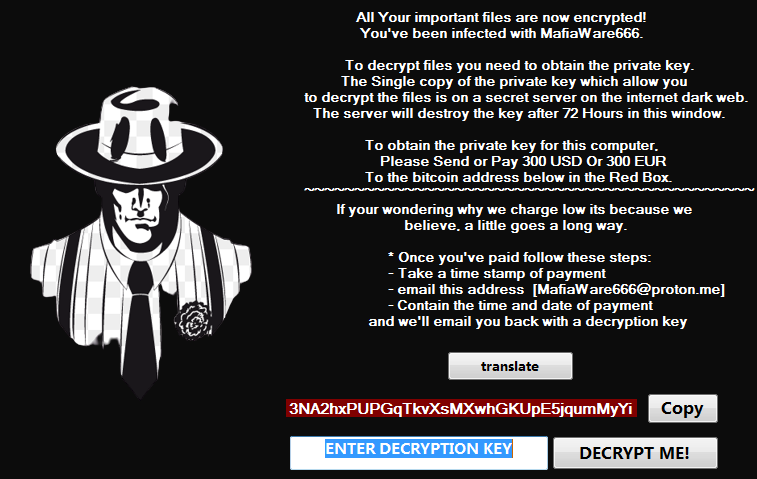
It should be noted that this Hades ransomware family is different than the Hades ransomware used by Evil Corp in an attack on ForwardAir.
The Hades ransomware targeted by this encryptor is a lower-level operation that did not perform data theft and double-extortion attacks.
Using the Hades decryptor
The Avast decryptor only supports files encrypted by specific variants of the Hades ransomware family. These variants include the following extensions and strings appended/prepended to an encrypted file's name:
- .MafiaWare666
- .jcrypt
- .brutusptCrypt
- .bmcrypt
- .cyberone
- .l33ch
If you were affected by one of these variants, you can download the free decryptor from here, run the executable, select the drive that holds the encrypted files, and point the tool to a sample pair of encrypted and original files.
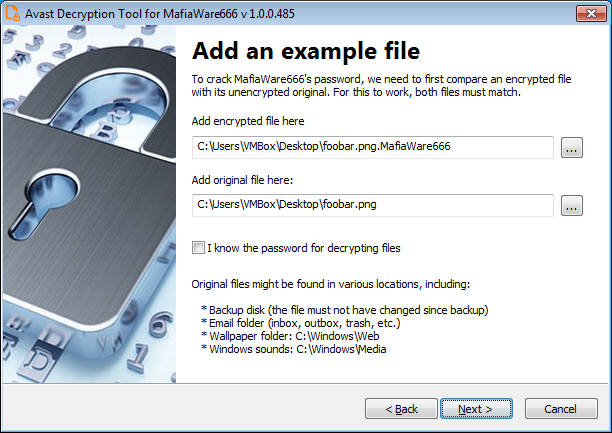
Those who possess a valid password for decrypting the files but couldn't get the decryptor supplied by Hades to work can tick the box and provide it onto Avast's tool.
Most victims don't have a password, so they will have to wait for Avast's tool to crack it manually, which may take some time.
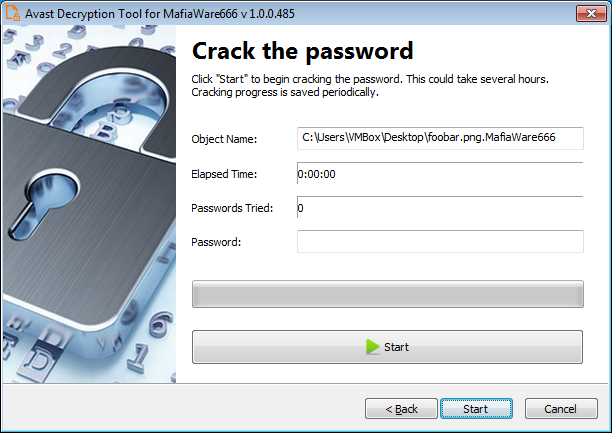
After the password is found, the users can initiate the decryption process. At this stage, it is highly recommended to tick the boxes to back up the encrypted files and run the tool as an administrator.
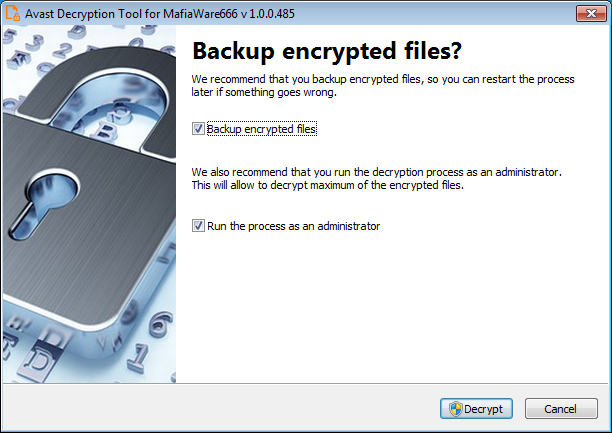
It is important to stress that you should enable the option to back up encrypted files, as if there is a problem with the decryptor, the encrypted files can become further corrupted.
For a step-by-step guide on using the decryptor, you can read Avast's blog post.
- aum and Karlston
-

 2
2




Recommended Comments
There are no comments to display.
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.