The Australian Federal Police arrested a woman in Werrington, Sydney, for allegedly email bombing the office of a Federal Member of Parliament.
Email bombing is an online attack where attackers bombard an email address with thousands of emails to overwhelm a recipient's inbox or mail server.
The AFP says the women sent over 32,000 emails to the MP's office over 24 hours, preventing employees from using the IT systems and the public from contacting the office.
"Police will allege the woman used multiple domains to send 32,397 emails over a 24-hour period until her arrest, which resulted in continued disruption and harassment," explains the Australian Federal Police.
The alleged email bomber is to be charged with one count of committing unauthorized impairment of electronic communications, which violates section 477.3 of the Criminal Code Act 1995 (Cth).
The maximum imprisonment penalty for this particular offense is ten years.
Although the AFP does not elaborate on the exact means by which the arrested woman sent a large volume of emails to the MP office within such a short time, they state that the attack used multiple domains when sending the emails.
This likely means that the arrested woman used an "email bombing" service that allows customers to send many emails to a target from different addresses, thus making it challenging for the recipient to contain and manage the atypical denial of service attack.
Many of these services can bypass spam filters in use today, filling employee inboxes and overwhelming the targeted organization's email server.
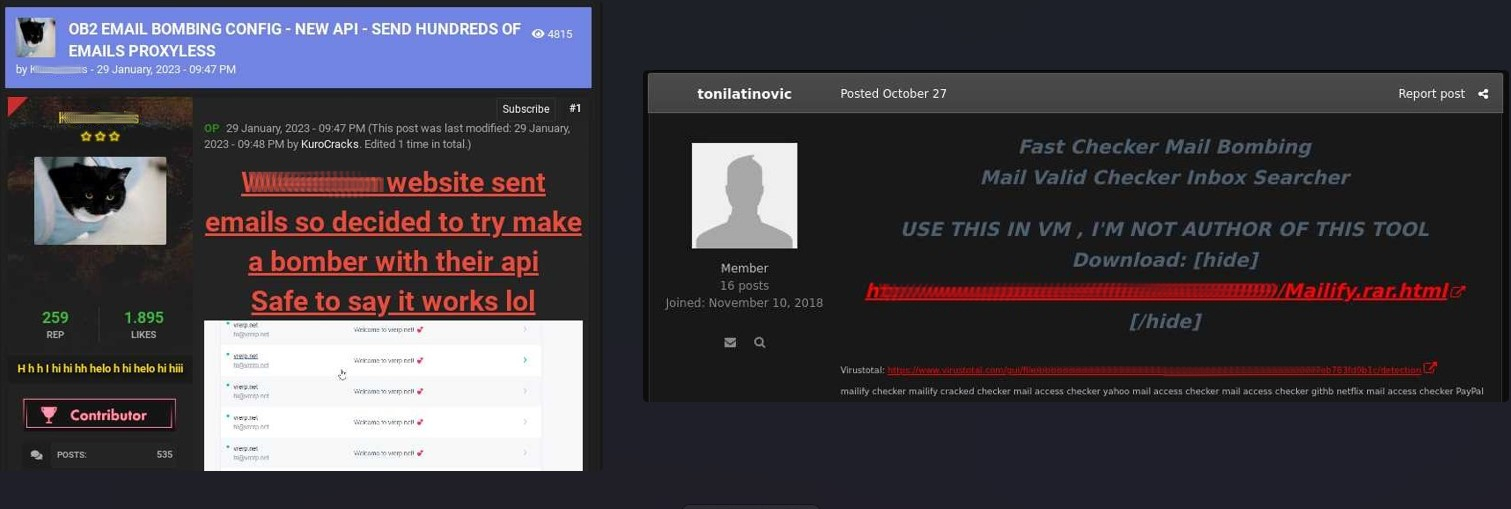
These email bombing services are typically offered on the dark web or underground hacking forums and marketplaces, such as the promoted ones shown below.
Alternatively, the attacker might have used scripts that automate registering the target's email address to many websites, which then sent registration confirmations to the MP office. Since these sites are legitimate, their messages bypass spam filters.
Unfortunately, due to these attacks involving a large number of senders, blocking the email addresses or marking their messages as spam isn’t a very effective defense method.
The only way to deal with this type of threat is to set up an advanced filtering tool that will block messages based on specific criteria, such as keywords in the content.




Recommended Comments
There are no comments to display.
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.