An Australian man was charged for developing and selling the Imminent Monitor remote access trojan, used to spy on victims' devices remotely.
A remote access trojan is a type of malware that allows full remote access to an infected device, including the ability to execute commands, log keystrokes, steal files and data, install additional software, take screenshots, and even record video from the device's webcam.
These types of malware are very popular among hackers due to its cheap price and the unfettered access it provided to infected devices. However, they are also popular with domestic abusers who use them to spy on their victims.
Yesterday, the Australian Federal Police (AFP) announced that they had charged an Australian man, age 24, for developing and selling the Imminent Monitor (IM5) software.
The AFP alleges that the man sold the software to more than 14,500 people across 128 countries.
"A statistically high percentage of Australia-based PayPal purchasers of IM RAT (14.2%) are named as respondents on domestic violence orders. Additionally, one of these purchasers is also registered on the Child Sex Offender Register," reads a press release by the AFP.
"Of the 14 individuals, 11 bought the RAT during the active period of their domestic violence order (DVO) or within two years a DVO was issued."
Since the operation started in 2013, law enforcement states that the developer made 300,000 to 400,000, which was predominantly used to pay for food deliveries and purchase "other consumable and disposable items."
The Australian man faces six charges with a maximum penalty of 20 years.
Almost 3 years in the making
The Imminent Monitor operation started in 2013 when the developer (then 15) began promoting the product on hacking forums and a dedicated website.
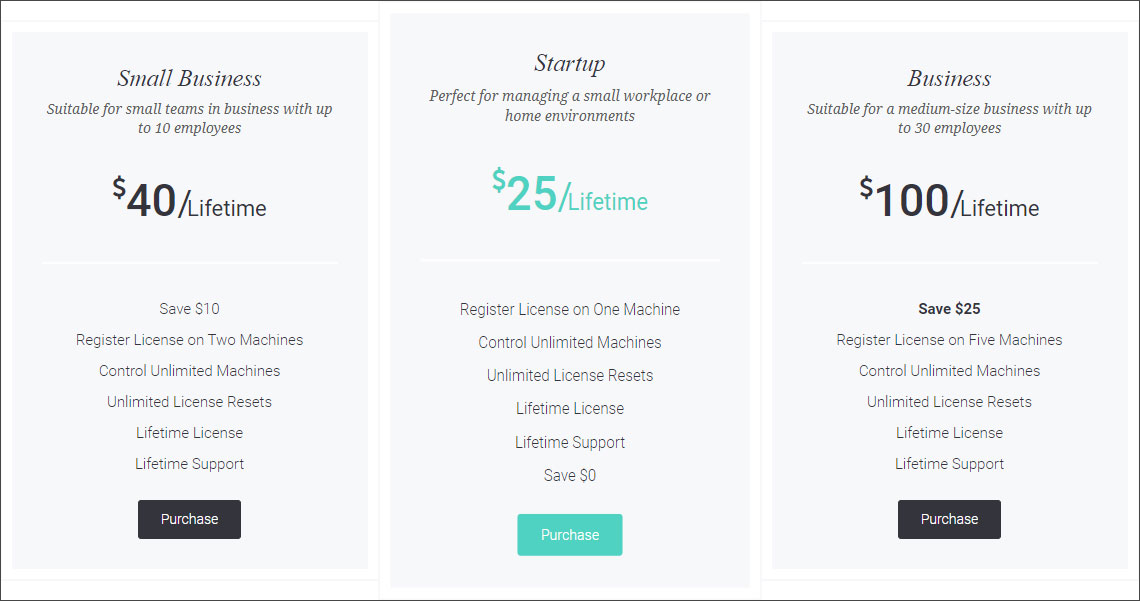
The program was marketed as a remote administrator tool that could be purchased for as little as $25 for a lifetime license, which included customer support.
While the website promoted the product as a legitimate tool, the developer provided customer support and promoted the software under the alias 'ShockWave.'
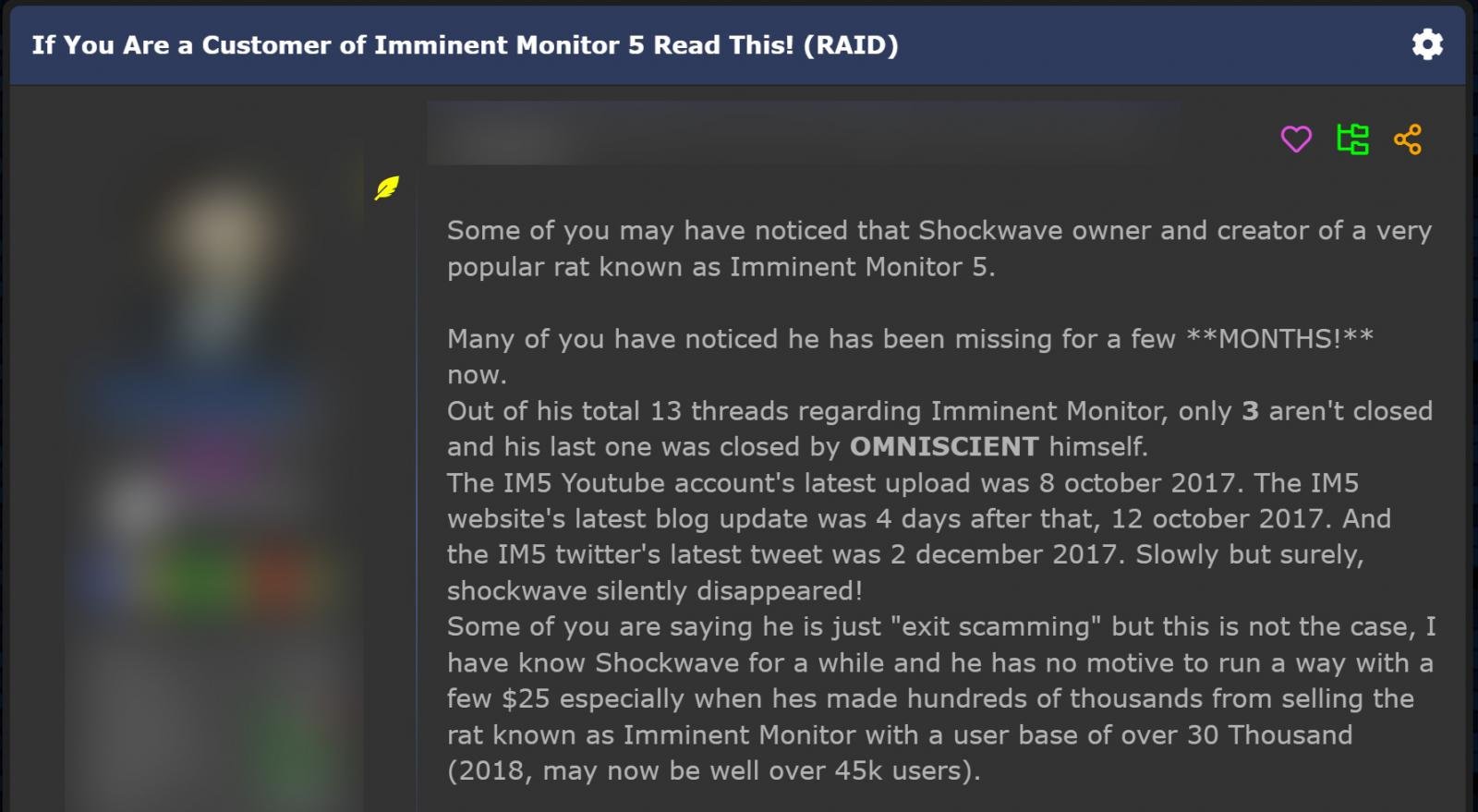
In April 2019, a member of a hacking forum warned that ShockWave had gone missing and that he was likely arrested, warning Imminent Monitor customers that they would probably be facing legal action due to their use of the software.
Seven months later, in November, Europol announced a global law enforcement operation that led to the seizure of over 430 devices involved in the Imminent Monitor operation and the imminentmethods.net website used to promote the software.
As part of this operation, law enforcement shut down the Imminent Monitor platform and arrested 13 of its most prolific users. Search warrants were also executed against the developer and an employee located in Belgium.
The Australian Police also received intelligence from Palo Alto Unit 42 that same year, allowing them to arrest the developer.
Australia charges dev of Imminent Monitor RAT used by domestic abusers



3175x175(CURRENT).thumb.jpg.b05acc060982b36f5891ba728e6d953c.jpg)


Recommended Comments
There are no comments to display.
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.