Security researchers have detected a massive campaign that scanned close to 1.6 million WordPress sites for the presence of a vulnerable plugin that allows uploading files without authentication.
The attackers are targeting the Kaswara Modern WPBakery Page Builder, which has been abandoned by its author before receiving a patch for a critical severity flaw tracked as CVE-2021-24284.
The vulnerability would allow an unauthenticated attacker to inject malicious Javascript to sites using any version of the plugin and perform actions like uploading and deleting files, which could lead to complete takeover of the site.
While the size of the campaign is impressive, with 1,599,852 unique sites being targeted, only a small portion of them are running the vulnerable plugin.
Researchers at Defiant, the maker of the Wordfence security solution for WordPress, observed an average of almost half a million attack attempts per day against customer sites they protect.
Indistinct large-scale attacks
Based on Wordfence telemetry data, the attacks started on July 4 and continue to this day. and are still ongoing today at an average of 443,868 attempts every day.
.png)
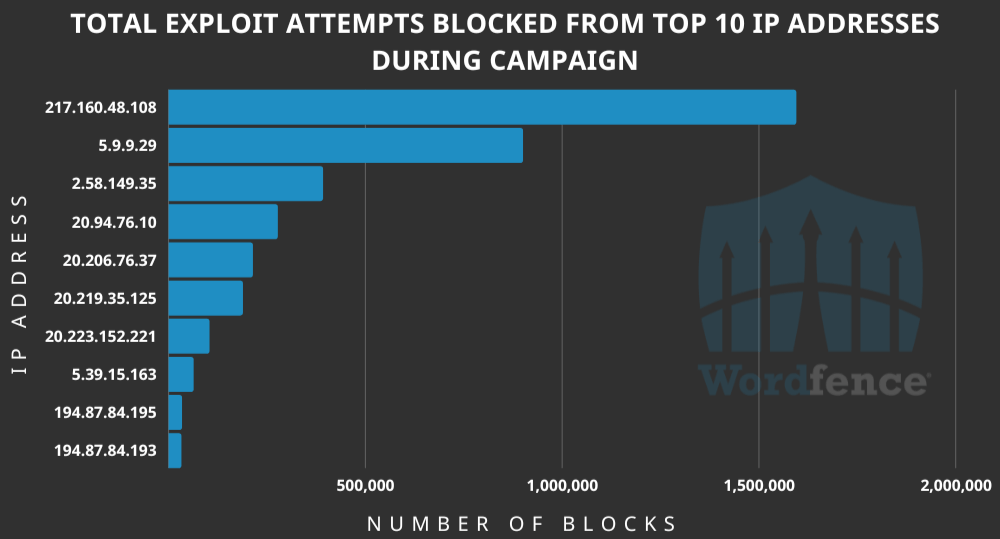
The attacks originate from 10,215 distinct IP addresses, with some having generated millions of requests while others are limited to lower numbers, the reearchers say.
The attackers send a POST request to ‘wp-admin/admin-ajax/php’, attempting to use the plugin’s ‘uploadFontIcon’ AJAX function to upload a malicious ZIP payload that contains a PHP file.
This file, in turn, fetches the NDSW trojan, which injects code in legitimate Javascript files present on the target sites to redirect visitors to malicious destinations like phishing and malware-dropping sites.
Some filenames the attackers use for the ZIP payloads are ‘inject.zip’, ‘king_zip.zip’, ‘null.zip’, ‘plugin.zip’, and ‘***_young.zip’.
These files or the presence of the “; if(ndsw==” string in any of your JavaScript files indicates that you have been infected.
If you’re still using the Kaswara Modern WPBakery Page Builder Addons plugin, you should remove it immediately from your WordPress site.
If you’re not using the plugin, you are still recommended to block the IP addresses of the attackers. For more details on the indicators and the most prolific sources of requests, check out Wordfence’s blog.
Attackers scan 1.6 million WordPress sites for vulnerable plugin
- aum
-

 1
1



3175x175(CURRENT).thumb.jpg.b05acc060982b36f5891ba728e6d953c.jpg)
Recommended Comments
There are no comments to display.
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.