Weaknesses in the implementation of TCP protocol in middleboxes and censorship infrastructure could be weaponized as a vector to stage reflected denial of service (DoS) amplification attacks, surpassing many of the existing UDP-based amplification factors to date.
Detailed by a group of academics from the University of Maryland and the University of Colorado Boulder at the USENIX Security Symposium, the volumetric attacks take advantage of TCP-non-compliance in-network middleboxes — such as firewalls, intrusion prevention systems, and deep packet inspection (DPI) boxes — to amplify network traffic, with hundreds of thousands of IP addresses offering amplification factors exceeding those from DNS, NTP, and Memcached.
Reflected amplification attacks are a type of DoS attacks in which an adversary leverages the connectionless nature of UDP protocol with spoofed requests to misconfigured open servers in order to overwhelm a target server or network with a flood of packets, causing disruption or rendering the server and its surrounding infrastructure inaccessible. This typically occurs when the response from the vulnerable service is larger than the spoofed request, which can then be leveraged to send thousands of these requests, thereby significantly amplifying the size and bandwidth issued to the target.
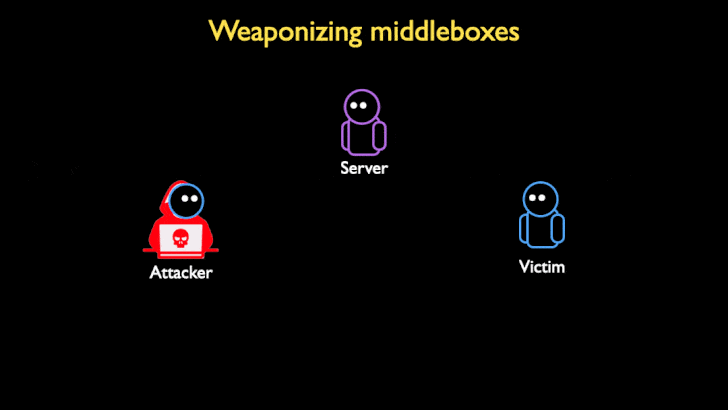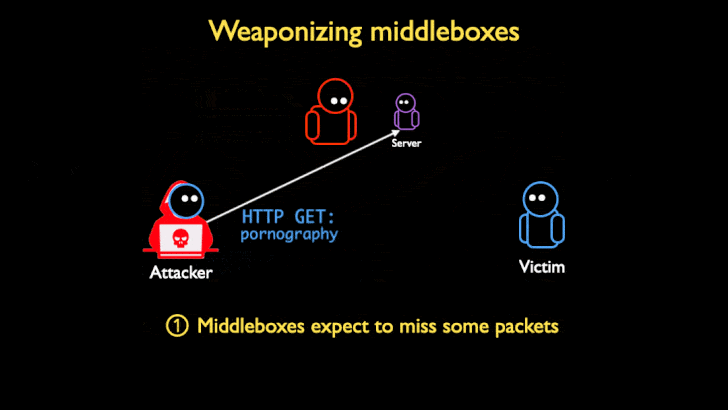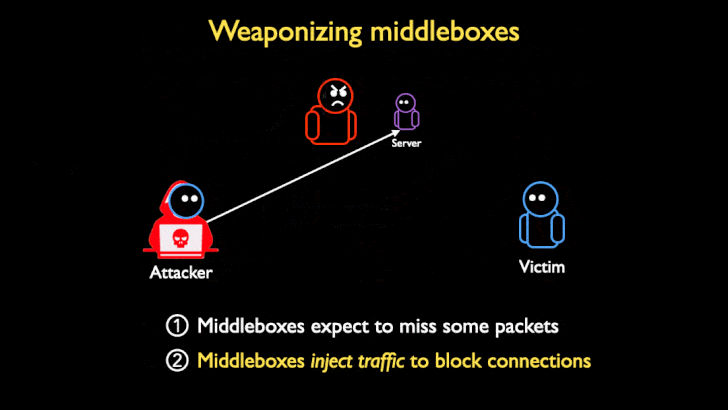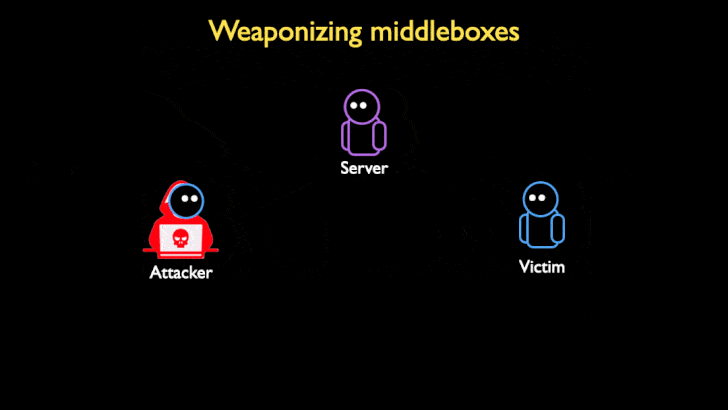
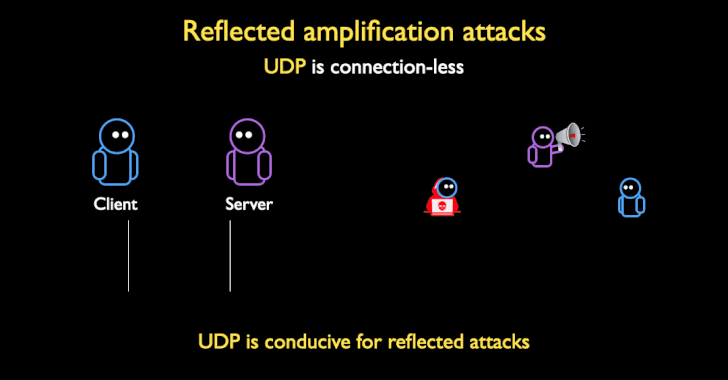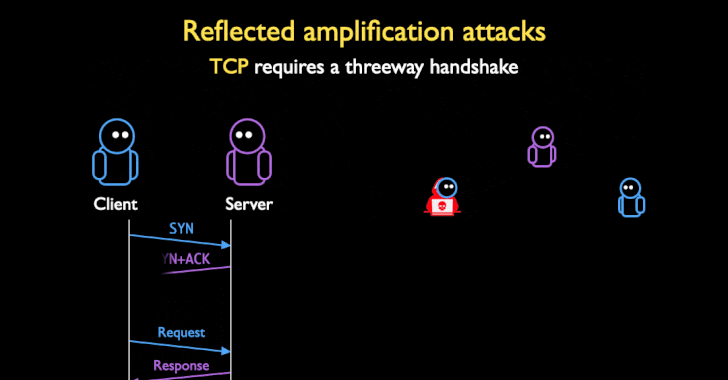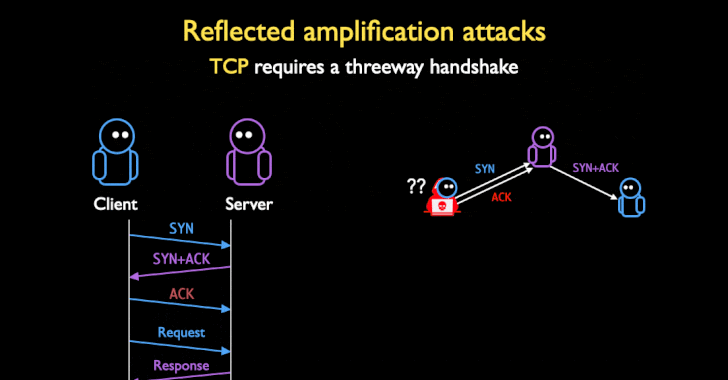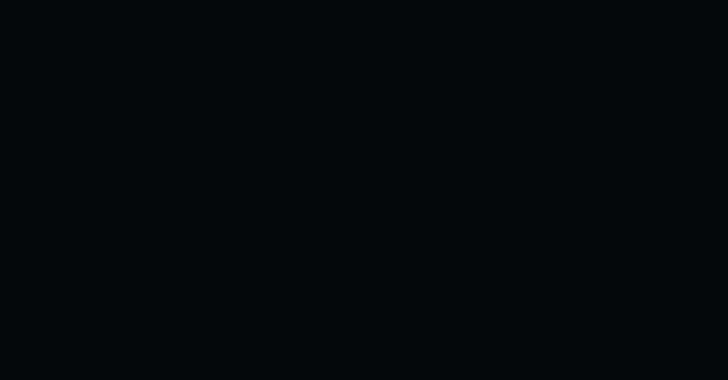
While DoS amplifications are traditionally UDP-based owing to complications arising out TCP's three-way handshake to set up a TCP/IP connection over an IP based network (SYN, SYN+ACK, and ACK), the researchers found that a large number of network middleboxes do not conform to the TCP standard, and that they can "respond to spoofed censored requests with large block pages, even if there is no valid TCP connection or handshake," turning the devices into attractive targets for DoS amplification attacks.
"Middleboxes are often not TCP-compliant by design: many middleboxes attempt [to] handle asymmetric routing, where the middlebox can only see one direction of packets in a connection (e.g., client to server)," the researchers said. "But this feature opens them to attack: if middleboxes inject content based only on one side of the connection, an attacker can spoof one side of a TCP three-way handshake, and convince the middlebox there is a valid connection."
What's more, a series of experiments found that these amplified responses come predominantly from middleboxes, including nation-state censorship devices and corporate firewalls, highlighting the role played by such infrastructure in enabling governments to suppress access to the information within their borders, and worse, allow adversaries to weaponize the networking devices to attack anyone.
"Nation-state censorship infrastructure is located at high-speed ISPs, and is capable of sending and injecting data at incredibly high bandwidths," the researchers said. "This allows an attacker to amplify larger amounts of traffic without worry of amplifier saturation. Second, the enormous pool of source IP addresses that can be used to trigger amplification attacks makes it difficult for victims to simply block a handful of reflectors. Nation-state censors effectively turn every routable IP addresses (sic) within their country into a potential amplifier."
"Middleboxes introduce an unexpected, as-yet untapped threat that attackers could leverage to launch powerful DoS attacks," the researchers added. "Protecting the Internet from these threats will require concerted effort from many middlebox manufacturers and operators."
- Karlston
-

 1
1


Recommended Comments
There are no comments to display.
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.