Researchers have demonstrated what they call the "first active contactless attack against capacitive touchscreens."
GhostTouch, as it's called, "uses electromagnetic interference (EMI) to inject fake touch points into a touchscreen without the need to physically touch it," a group of academics from Zhejiang University and Technical University of Darmstadt said in a new research paper.
The core idea is to take advantage of the electromagnetic signals to inject fake touch events such as taps and swipes into targeted locations of the touchscreen with the goal of taking over remote control and manipulating the underlying device.
The attack, which works from a distance of up to 40mm, hinges on the fact that capacitive touchscreens are sensitive to EMI, leveraging it to inject electromagnetic signals into transparent electrodes that are built into the touchscreen so as to register them as touch events.
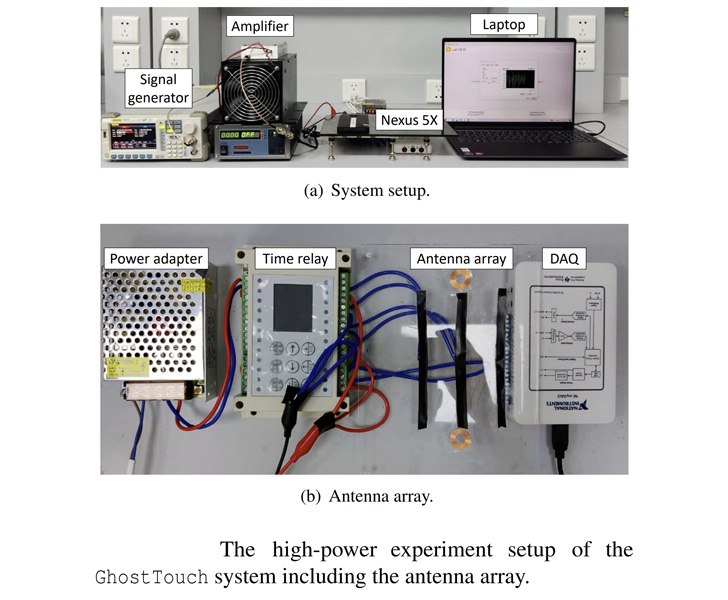
The experimental setup involves an electrostatic gun to generate a strong pulse signal that's then sent to an antenna to transmit an electromagnetic field to the phone's touchscreen, thereby causing the electrodes — which act as antennas themselves — to pick up the EMI.

This can be further fine-tuned by tweaking the signal and the antenna to induce a variety of touch behaviors, such as press and hold and swipe to select, depending on the device model targeted.
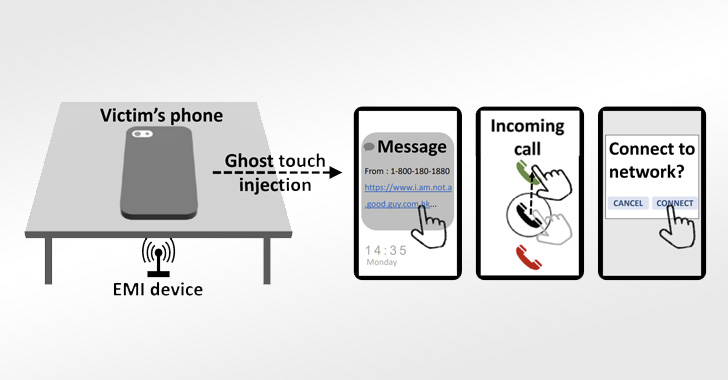
In a real-world scenario, this could play out in different ways, including swiping up to unlock a phone, connecting to a rogue Wi-Fi network, stealthily clicking on a malicious link containing malware, and even answering a phone call on the victim's behalf.
"In places like a cafe, library, meeting room, or conference lobbies, people might place their smartphone face-down on the table," the researchers said. "An attacker may embed the attack equipment under the table and launch attacks remotely."
As many as nine different smartphone models have been found vulnerable to GhostTouch, including Galaxy A10s, Huawei P30 Lite, Honor View 10, Galaxy S20 FE 5G, Nexus 5X, Redmi Note 9S, Nokia 7.2, Redmi 8, and an iPhone SE (2020), the latter of which was used to establish a malicious Bluetooth connection.
To counteract the threat, the researchers recommend adding electromagnetic shielding to block EMI, improving the detection algorithm of the touchscreen, and prompting users to enter the phone's PIN or verify their faces or fingerprints prior to executing high-risk actions.
"GhostTouch controls and shapes the near-field electromagnetic signal, and injects touch events into the targeted area on the touchscreen, without the need for physical touch or access to the victim's device," the researchers said.
- Karlston
-

 1
1



Recommended Comments
There are no comments to display.
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.