A crypto-stealing phishing campaign is underway to bypass multi-factor authentication and gain access to accounts on Coinbase, MetaMask, Crypto.com, and KuCoin and steal cryptocurrency.
The threat actors abuse the Microsoft Azure Web Apps service to host a network of phishing sites and lure victims to them via phishing messages impersonating bogus transaction confirmation requests or suspicious activity detection.
For example, one of the phishing emails seen in the attacks pretended to be from Coinbase, which says they locked the account due to suspicious activity.
.png)
Phishing email impersonating Coinbase - Source: PIXM
When the targets visit the phishing site, they are presented with a chat window supposedly for 'customer support,' controlled by a scammer who directs visitors through a multi-step defrauding process.
PIXM has been tracking this campaign since 2021 when the threat group targeted only Coinbase. Recently, PIXM's analysts noticed an expansion in the campaign's targeting scope to include MetaMask, Crypto.com, and KuCoin.
Bypassing 2FA
The first phase of the attack in the fake crypto exchange phishing sites involves a bogus login form followed by a two-factor authentication prompt.
Regardless of the credentials entered during this stage, they will still be stolen by the threat actors. The page then proceeds to a prompt asking for the 2FA code needed to access the account.
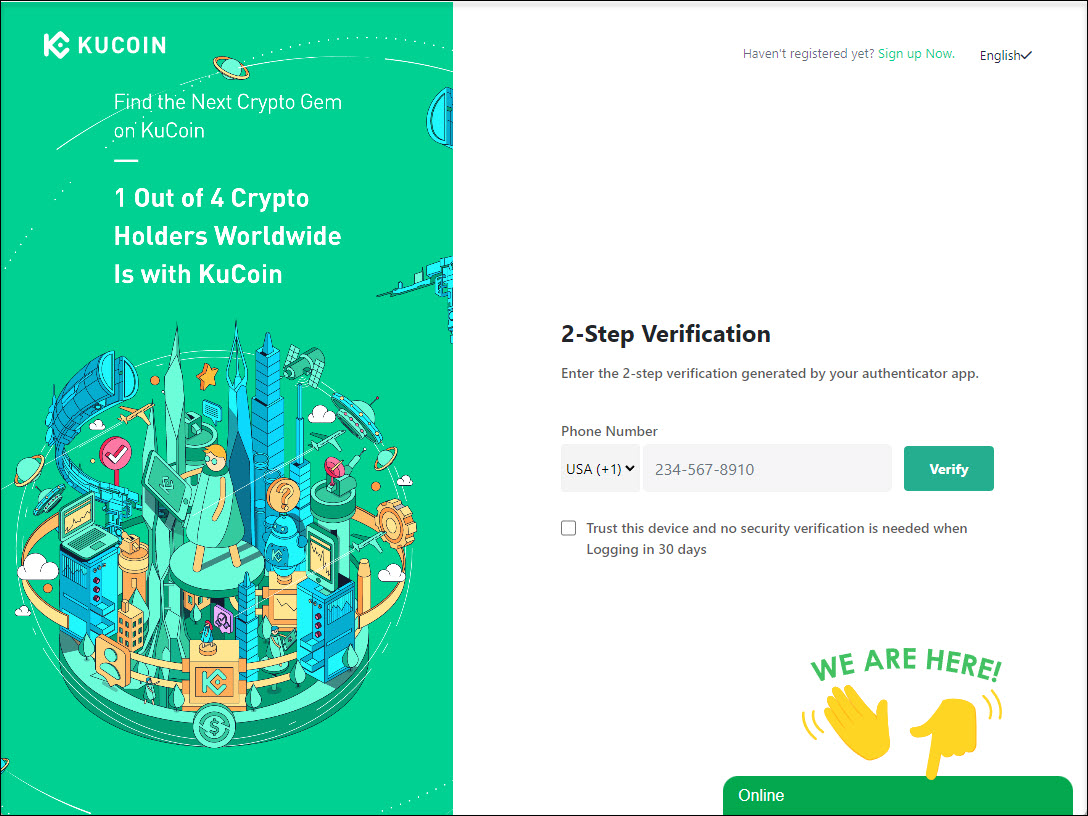
2FA step of the phishing site - Source: PIXM
The attackers try out the entered credentials on the legitimate website, triggering the sending of a 2FA code to the victim, who then enters a valid 2FA on the phishing site.
The threat actors then attempt to use the entered 2FA code to log in to the victim's account as long as they act before the timer runs out.
It should be noted that the MetaMask phishing attacks are targeting recovery phrases, rather than credentials or 2FA codes.
Chatting with scammers
Regardless of whether a 2FA code works, the researchers say that the scammers trigger the next attack stage, which is to launch on-screen chat support.
This is done by displaying a fake error message stating the account has been suspended due to suspicious activity and asking the visitor to contact support to resolve the matter.
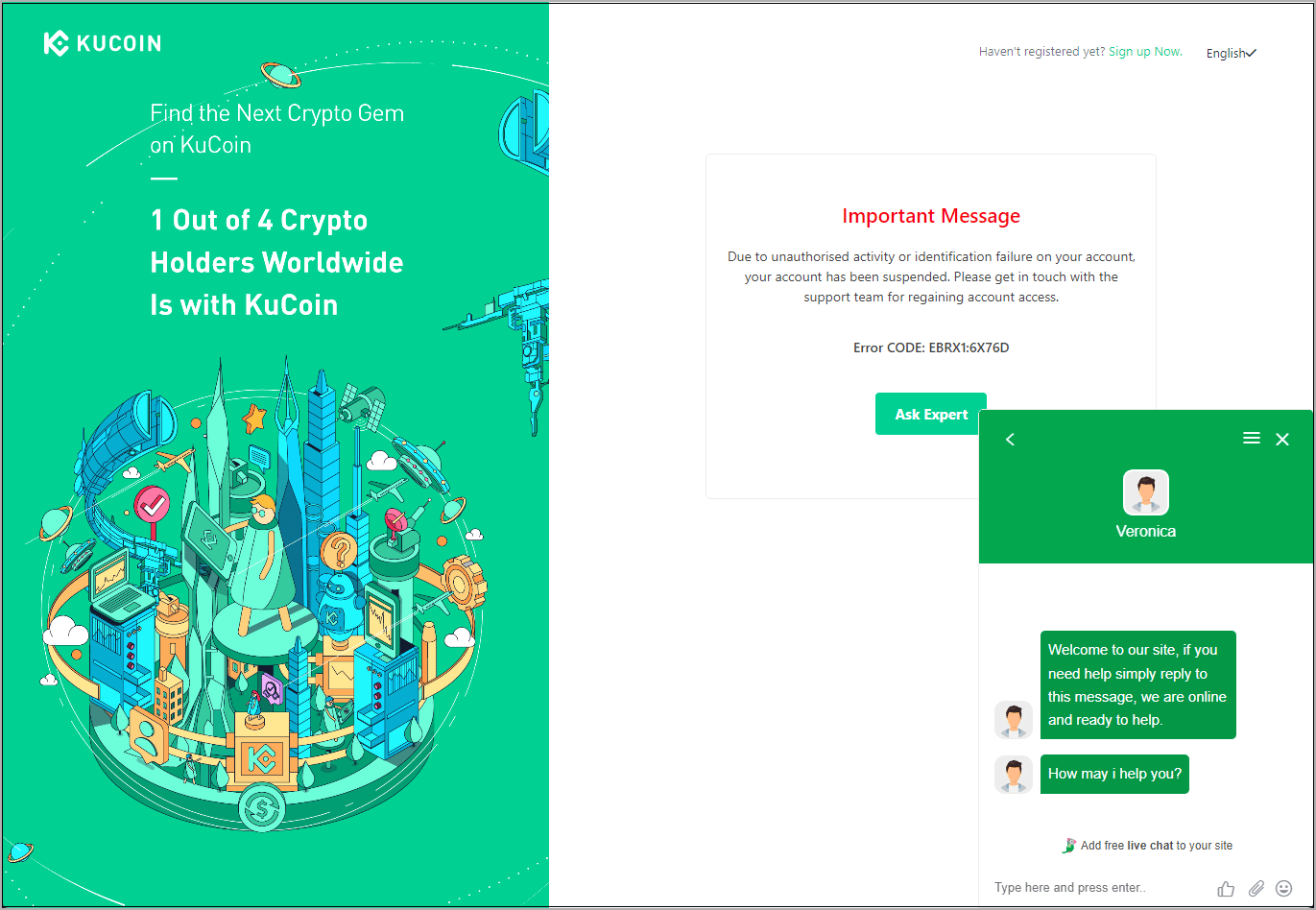
Generating a fake login error - Source: PIXM
In this support chat, the threat actors start a conversation with the targeted victim to keep them around in case different credentials, recovery phrases, or 2FA codes are needed for the threat actors to log in to the account.
"They will prompt the user for their username, password, and 2-Factor authentication code directly in the chat," explains the new PIXM report.
"The criminal will then take this directly to a browser on their machine and again try to access the users account."
For successfully breached accounts, the victim is still engaged with customer support in case they need to confirm fund transfers while the crooks empty their wallets.
However, for accounts they cannot breach through the support chat, the threat actors switch to an alternative method to authenticate their device as "trustworthy" for the cryptocurrency platform.
Remote trickery
To overcome the authenticated device obstacle, the attackers convince the victim to download and install the 'TeamViewer' remote access app.
Next, the scammers ask the victims to log in to their cryptocurrency wallet or exchange accounts, and while they do so, the threat actors add a random character in the password field to cause a login failure.
The attacker then asks the victim to paste the password on the TeamViewer chat, uses the password (minus the random character) to login on to their device, and then snatches the device confirmation link sent to the victim to authenticate their device as trusted.
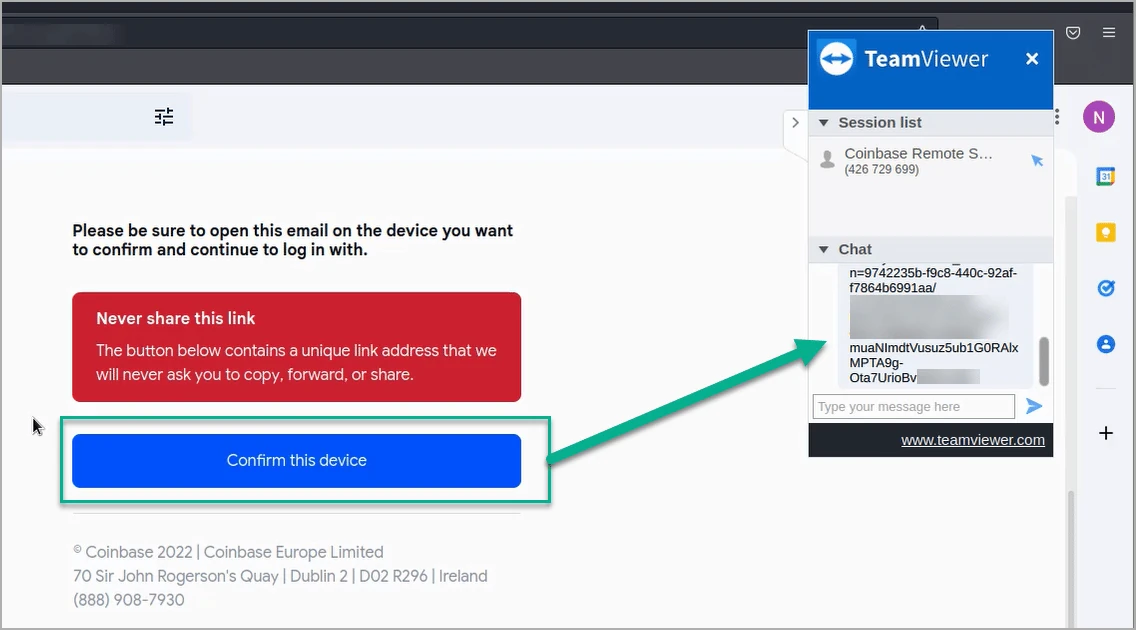
Stealing the device authentication link - Source: PIXM
Once they gain access to the account or wallet, the threat actors drain it of all funds while still keeping the victim engaged in the support chat.
To avoid getting scammed in attacks like these, it is essential to always pay attention to the sender's email address and any sent URLs.
If these URLs do not match the cryptocurrency platform, you should immediately treat the email as suspicious and delete it.
Unfortunately, if you fall for one of these scams, there is nothing that a crypto exchange can due to recover your funds once they are transmitted from your wallet.
- Dark Monkey
-

 1
1




Recommended Comments
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.