Atomic Stealer is a malware that has been plaguing Mac users for a while now. This time, attackers are tricking users in a more sophisticated manner, by pretending to offer browser updates.
Atomic Stealer, aka AMOS, is a stealer, which can harvest passwords from your Apple iCloud Keychain, crypto assets, files, and other personal data. It was first discovered by security researchers in April 2023, though it has since evolved. Criminals who have access to AMOS have been using it to phish victims using various techniques, including via cracked software.
AMOS is being delivered to users through a fake browser update chain that is being called Clearfake campaign, which was discovered by Security Researcher Randy McEoin in August 2023. On November 17, security researcher Ankit Anubhav discovered that the Clearfake campaign was being used to target Mac users.
An article that has been published by Malwarebytes (spotted by 9to5Mac) reveals the details about how the Atomic Stealer targets users. The attackers are using malicious ads to deliver the stealer to users, they do so by purchasing legitimate ad space on Google and other services. It infects compromised website servers, which are then used to serve as a means to distribute the malware.
When a user looks up an app that they want to download, they may see the fake ad, and click on it. This initiates the download of the file ( a DMG file) with the malware in it. The unsuspecting user may run the file to update their browser. But this is when things take a turn, it begins executing some commands after prompting for the administrative password. Once the user gives the password, AMOS steals their iCloud data and files, and sends them to a remote server. This form of attack is referred to as malvertising, which is actually quite commonly used to trick Windows users.
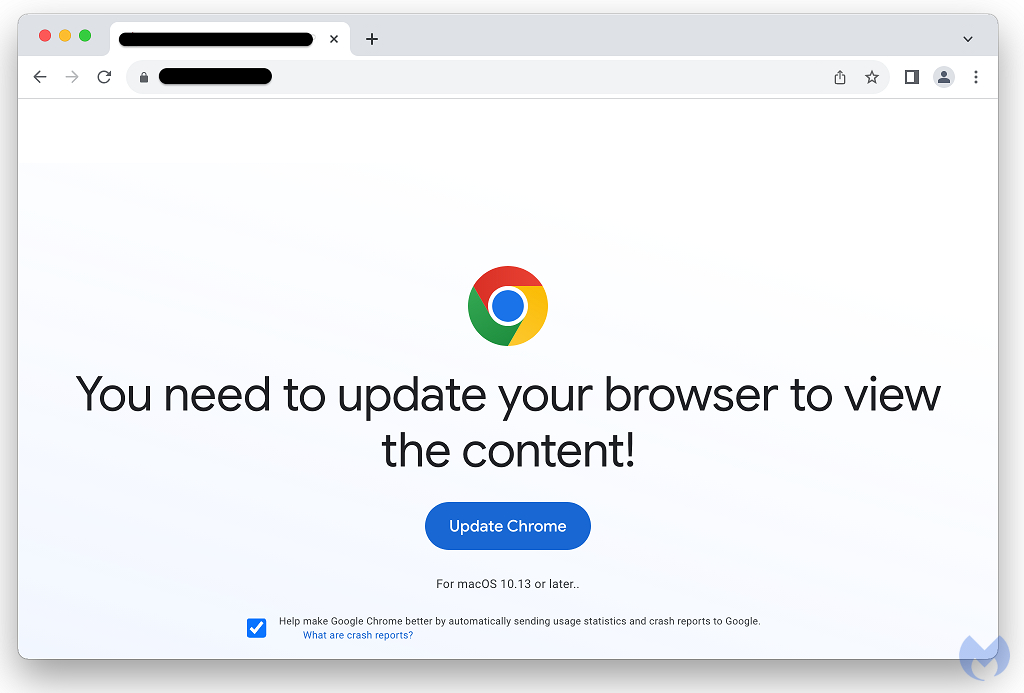
The Clearfake campaign is smart, it detects the user's browser (user agent) and offers an update specific to it. So Chrome users will see a fake update that looks like an update prompt from Chrome, refer to the screenshot below.
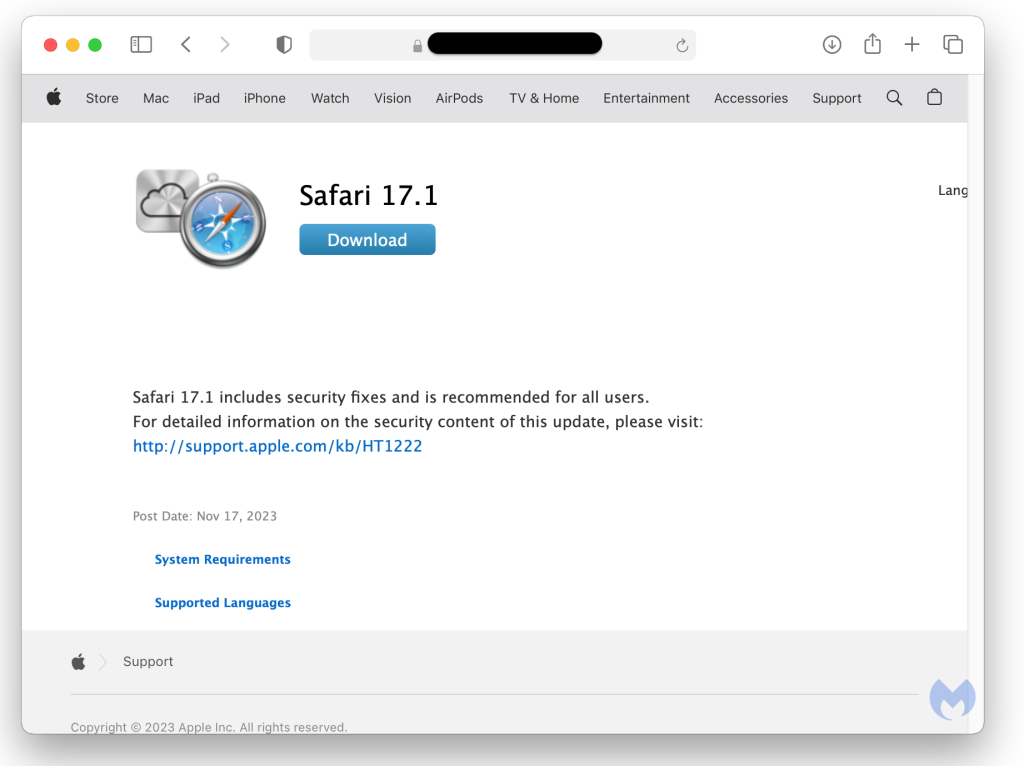
Here is what the fake update for Apple Safari looks like. It has an outdated icon for Safari and iCloud, which is pretty easy to spot if you're familiar with the modern ones.
Malwarebytes says that AMOS could be the first instance of a socially engineered attack, similar to those that affect Windows, to target macOS. The fact that attackers are viewing Mac users as potential victims is also a sign that Apple's computers are getting popular. This way they can breach more victims to phish them, or to use the data for future attacks.
We recommend paying close attention to where you download files from. Avoid sketchy sites, don't download pirated software. If you want to update your apps, go to the official website to get the latest update. Or, you can update your browser directly from its menu. Apple Safari is an exception to this, as updates are delivered via a macOS Update from the System Settings (System Preferences). And as always, use an ad blocker such as uBlock Origin for Firefox / Chrome, or AdGuard to protect your computer from ads and malware.
If you are worried that you might have a malware on your machine, you could download the free version of Malwarebytes to run a scan and remove the malware. Remember, most apps will not ask for your administrator password to install an update, so treat this as a red flag, as it may use it to bypass macOS Gatekeeper, the built-in security tool in the operating system.



3175x175(CURRENT).thumb.jpg.b05acc060982b36f5891ba728e6d953c.jpg)
Recommended Comments
There are no comments to display.
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.