Details of an eight-year-old security vulnerability in the Linux kernel have emerged that the researchers say is "as nasty as Dirty Pipe."
Dubbed DirtyCred by a group of academics from Northwestern University, the security weakness exploits a previously unknown flaw (CVE-2022-2588) to escalate privileges to the maximum level.
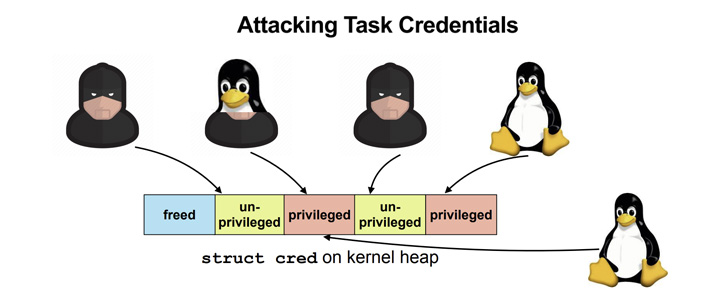
"DirtyCred is a kernel exploitation concept that swaps unprivileged kernel credentials with privileged ones to escalate privilege," researchers Zhenpeng Lin, Yuhang Wu, and Xinyu Xing noted. "Instead of overwriting any critical data fields on kernel heap, DirtyCred abuses the heap memory reuse mechanism to get privileged."
This entails three steps -
- Free an in-use unprivileged credential with the vulnerability
- Allocate privileged credentials in the freed memory slot by triggering a privileged userspace process such as su, mount, or sshd
- Operate as a privileged user
The novel exploitation method, according to the researchers, pushes the dirty pipe to the next level, making it more general as well as potent in a manner that could work on any version of the affected kernel.
"First, rather than tying to a specific vulnerability, this exploitation method allows any vulnerabilities with double-free ability to demonstrate dirty-pipe-like ability," the researchers said.
"Second, while it is like the dirty pipe that could bypass all the kernel protections, our exploitation method could even demonstrate the ability to escape the container actively that Dirty Pipe is not capable of."
Dirty Pipe, tracked as CVE-2022-0847 (CVSS score: 7.8) and affecting Linux kernel versions starting from 5.8, refers to a security vulnerability in the pipe subsystem that allows underprivileged processes to write to arbitrary readable files, leading to privilege escalation.
The exploitable vulnerability was so called after the Dirty Cow vulnerability discovered in 2016 based on their similarities.
Given that objects are isolated based on their type and not privileges, the researchers recommend isolating privileged credentials from unprivileged ones using virtual memory to prevent cross-cache attacks.
- Karlston
-

 1
1



Recommended Comments
There are no comments to display.
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.