A set of three critical zero-day vulnerabilities now tracked as TLStorm could let hackers take control of uninterruptible power supply (UPS) devices from APC, a subsidiary of Schneider Electric.
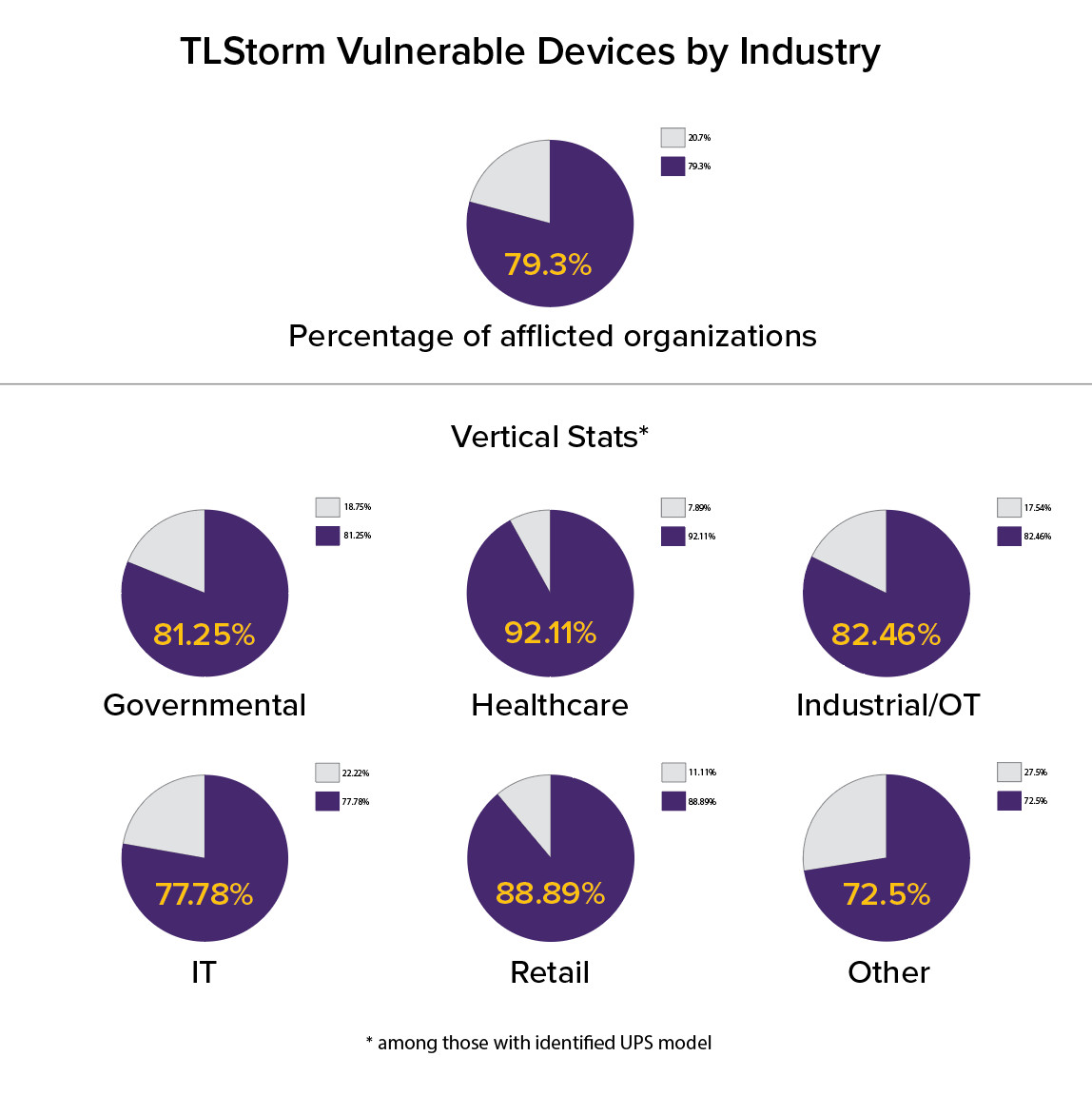
The flaws affect APC Smart-UPS systems that are popular in a variety of activity sectors, including governmental, healthcare, industrial, IT, and retail.
UPS devices act as emergency power backup solutions and are present in mission-critical environments such as data centers, industrial facilities, hospitals.
Risk of physical impact
Researchers at Armis, a company providing security solutions for connected devices in enterprises, found the three issues in APC’s SmartConnect and Smart-UPS family of products.
Two of the vulnerabilities, CVE-2022-22805 and CVE-2022-22806 are in the implementation of the TLS (Transport Layer Security) protocol that connects the Smart-UPS devices with the “SmartConnect” feature to the Schneider Electric management cloud.
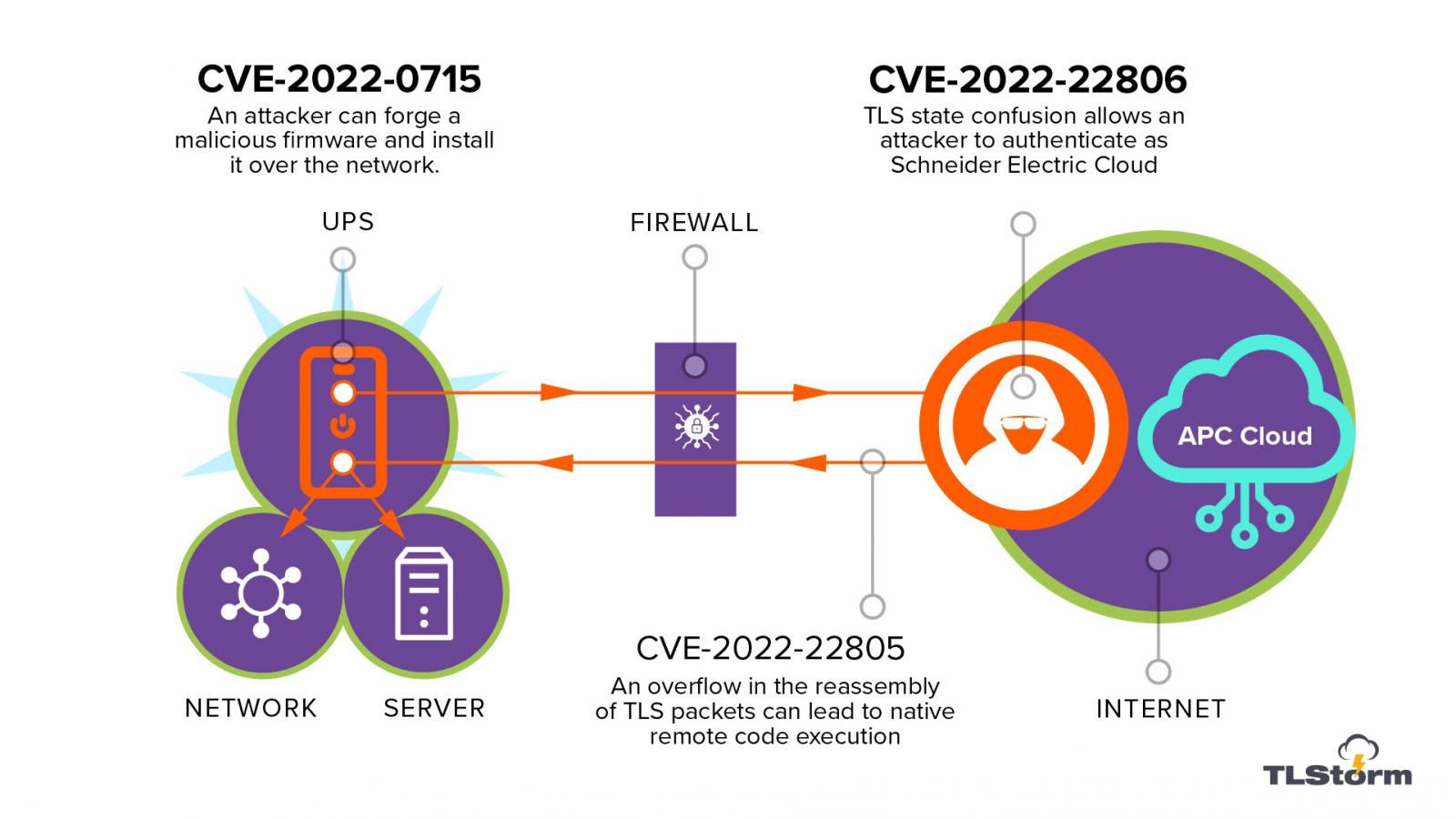
The third one, identified as CVE-2022-0715, relates to the firmware of “almost all APC Smart-UPS devices,” which is not cryptographically signed and its authenticity cannot be verified when installed on the system.
While the firmware is encrypted (symmetric), it lacks a cryptographic signature, allowing threat actors to create a malicious version of it and deliver it as an update to target UPS devices to achieve remote code execution (RCE).
Armis researchers were able to exploit the flaw and build a malicious APC firmware version that was accepted by Smart-UPS devices as an official update, a process that is performed differently depending on the target:
- The latest Smart-UPS devices featuring the SmartConnect cloud connection functionality can be upgraded from the cloud management console over the Internet
- Older Smart-UPS devices which use the Network Management Card (NMC) can be updated over the local network
- Most Smart-UPS devices can also be upgraded using a USB drive
Considering that vulnerable APC UPS units are used in about eight out of 10 companies - as per data from Armis - and the sensitive environments they serve (medical facilities, ICS network, server rooms), the implications can have significant physical consequences.
The TLS-related vulnerabilities that Armis discovered appear to be more severe as they can be exploited by an unauthenticated attacker without user interaction, in what is known as a zero-click attack.
“[CVE-2022-22806 and CVE-2022-22805] involve the TLS connection between the UPS and the Schneider Electric cloud. Devices that support the SmartConnect feature automatically establish a TLS connection upon startup or whenever cloud connections are temporarily lost” - Armis Labs
Both vulnerabilities are caused by improper TLS error handling in the TLS connection from the Smart-UPS to the Schneider Electric server, and they lead to remote code execution when properly exploited.
One of the security issues is an authentication bypass caused by “state confusion in the TLS handshake,” the other is a memory corruption bug.
In a blog post today, Armis shows how the vulnerabilities could be leveraged by a remote threat actor:
Mitigation recommendations
The researchers’ report explains the technical aspects for all three TLStorm vulnerabilities and provides a set of recommendations to secure UPS devices:
- Install the patches available on the Schneider Electric website
- If you are using the NMC, change the default NMC password (“apc”) and install a publicly-signed SSL certificate so that an attacker on your network will not be able to intercept the new password. To further limit the attack surface of your NMC, refer to the Schneider Electric Security Handbook for NMC 2 and NMC 3.
- Deploy access control lists (ACLs) in which the UPS devices are only allowed to communicate with a small set of management devices and the Schneider Electric Cloud via encrypted communications.
Armis has also published technical white paper with all the details of the research.
APC UPS zero-day bugs can remotely burn out devices, disable power
- aum and Reefa
-

 2
2



3175x175(CURRENT).thumb.jpg.b05acc060982b36f5891ba728e6d953c.jpg)
Recommended Comments
There are no comments to display.
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.