Researchers at Tencent Labs and Zhejiang University have presented a new attack called 'BrutePrint,' which brute-forces fingerprints on modern smartphones to bypass user authentication and take control of the device.
Brute-force attacks rely on many trial-and-error attempts to crack a code, key, or password and gain unauthorized access to accounts, systems, or networks.
The Chinese researchers managed to overcome existing safeguards on smartphones, like attempt limits and liveness detection that protect against brute-force attacks, by exploiting what they claim are two zero-day vulnerabilities, namely Cancel-After-Match-Fail (CAMF) and Match-After-Lock (MAL).
The authors of the technical paper published on Arxiv.org also found that biometric data on the fingerprint sensors' Serial Peripheral Interface (SPI) were inadequately protected, allowing for a man-in-the-middle (MITM) attack to hijack fingerprint images.
BrutePrint and SPI MITM attacks were tested against ten popular smartphone models, achieving unlimited attempts on all Android and HarmonyOS (Huawei) devices and ten additional attempts on iOS devices.
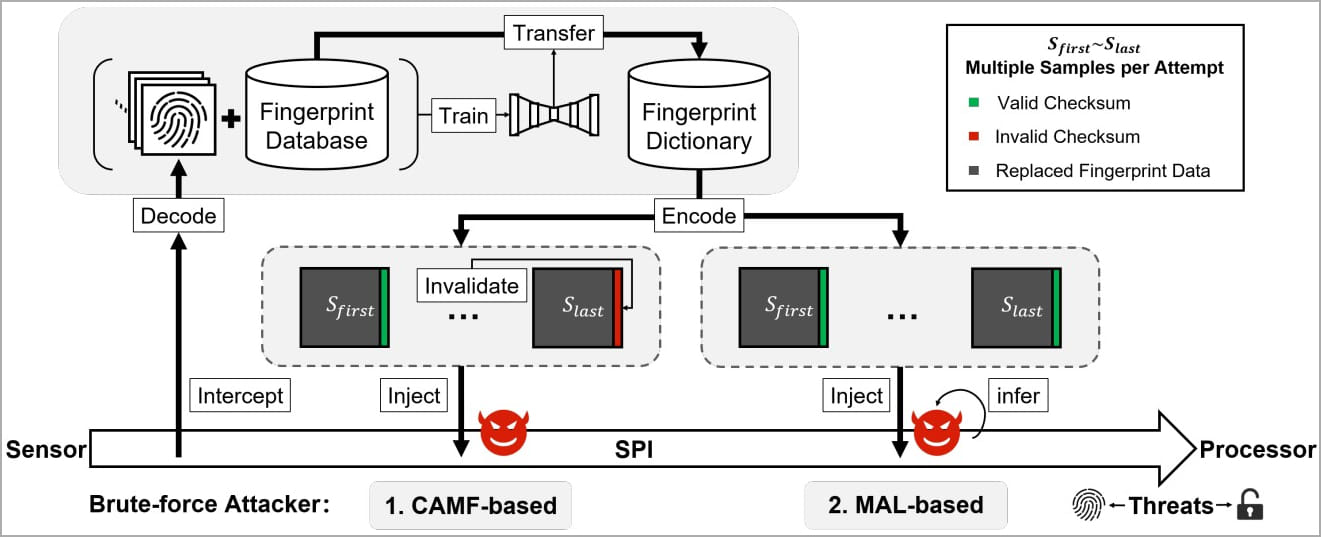
How BrutePrint works
The idea of BrutePrint is to perform an unlimited number of fingerprint image submissions to the target device until the user-defined fingerprint is matched.
The attacker needs physical access to the target device to launch a BrutePrint attack, access to a fingerprint database that can be acquired from academic datasets or biometric data leaks, and the necessary equipment, costing around $15.
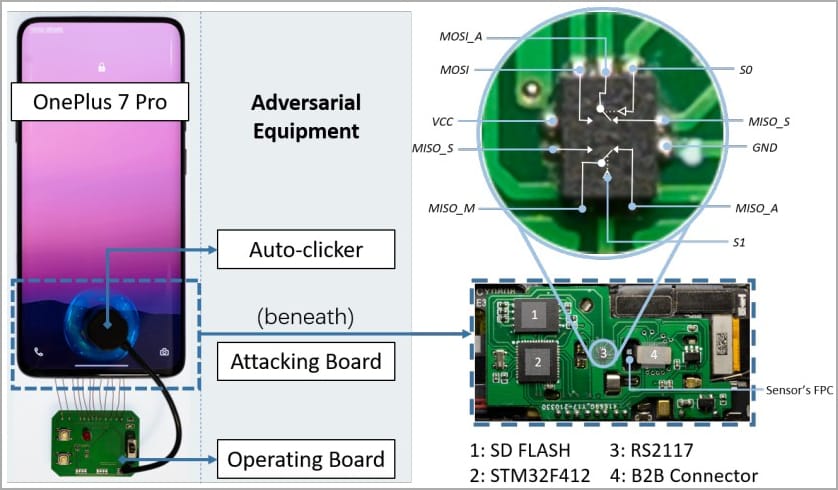
Equipment required for launching BrutePrint (arxiv.org)
Contrary to how password cracking works, fingerprint matches use a reference threshold instead of a specific value, so attackers may manipulate the False Acceptance Rate (FAR) to increase the acceptance threshold and create matches more easily.
BrutePrint stands in between the fingerprint sensor and the Trusted Execution Environment (TEE) and exploits the CAMF flaw to manipulate the multi-sampling and error-canceling mechanisms of fingerprint authentication on smartphones.
CAMF injects a checksum error in the fingerprint data to stop the authentication process at a pre-mature point. This allows the attackers to try out fingerprints on the target device while its protection systems won't register failed attempts, hence giving them infinite tries.
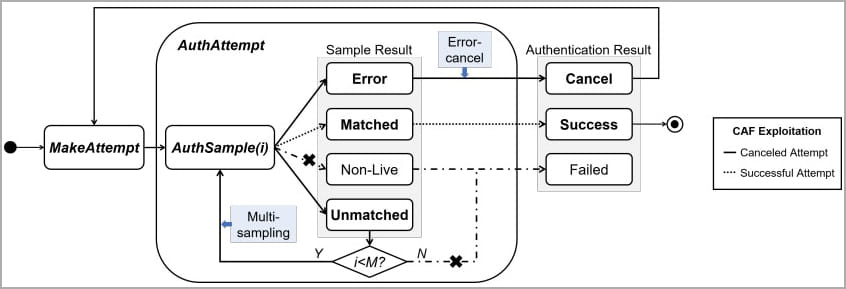
CAMF vulnerability attack logic (arxiv.org)
The MAL flaw enables the attackers to infer authentication results of the fingerprint images they try on the target device, even if the latter is in "lockout mode."
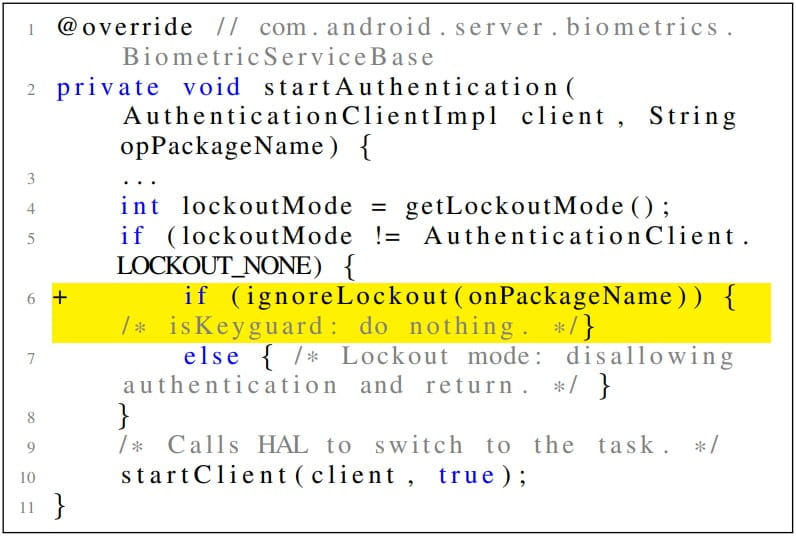
Keyguard exception introduced by device vendors causing MAL (arxiv.org)
The lockout mode is a protection system activated after a certain number of failed consecutive unlock attempts. During the lockout "timeout," the device shouldn't accept unlocking attempts, but MAL helps bypass this restriction.
The final component of the BrutePrint attack is using a "neural style transfer" system to transform all fingerprint images in the database to look like the target device's sensor scanned them. This makes the images appear valid and thus have better chances of success.
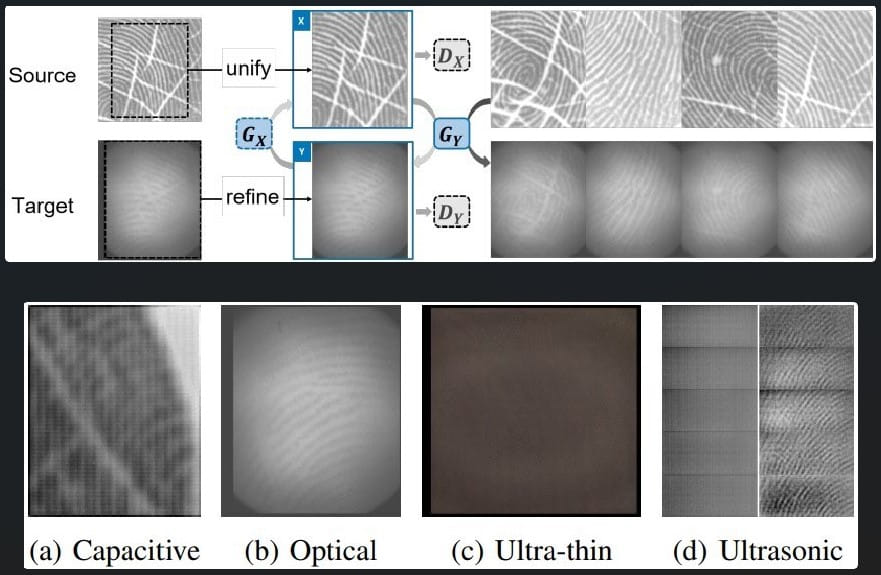
Tests on devices
The researchers conducted experiments on ten Android and iOS devices and found that all were vulnerable to at least one flaw.
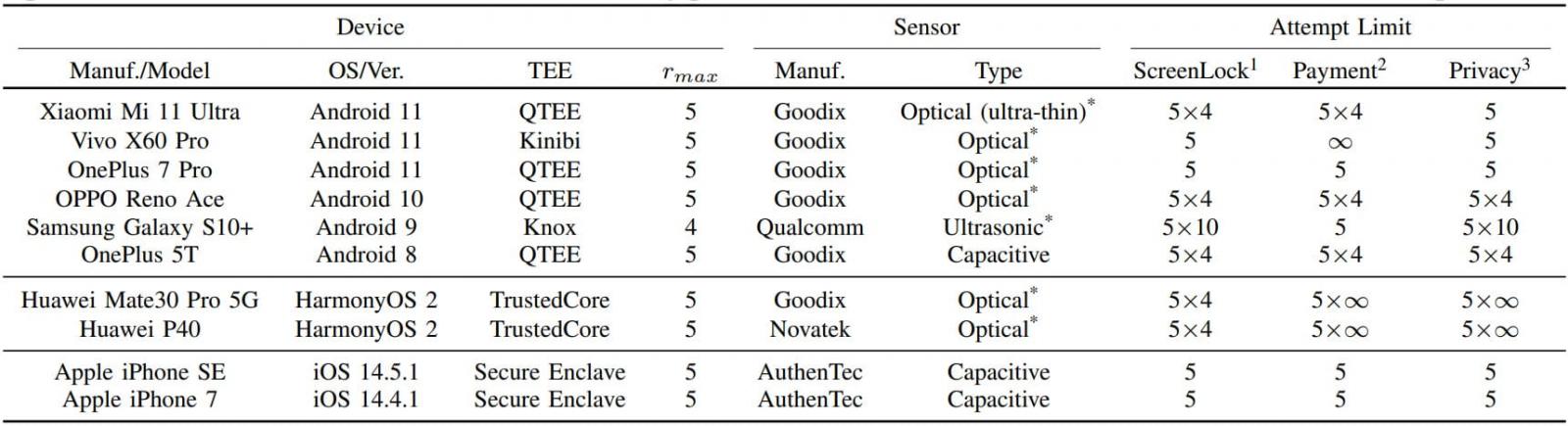
Details of tested devices (arxiv.org)
The tested Android devices allow infinite fingerprint tryouts, so brute-forcing the user's fingerprint and unlocking the device is practically possible given enough time.
On iOS, though, the authentication security is much more robust, effectively preventing brute-forcing attacks.
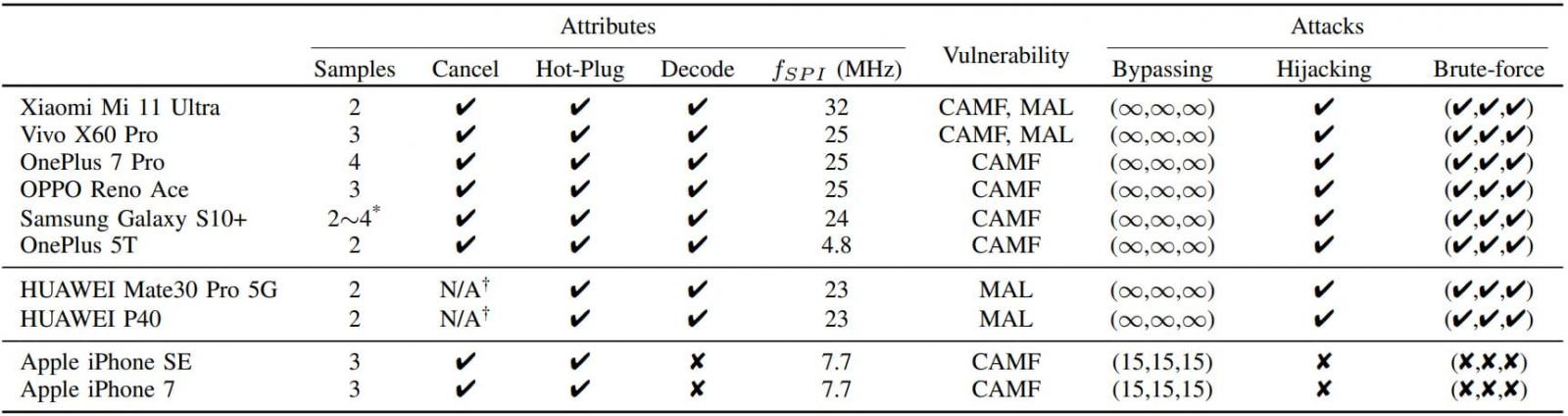
Test results table (arxiv.org)
Although the researchers found that iPhone SE and iPhone 7 are vulnerable to CAMF, they could only increase the fingerprint tryout count to 15, which isn't enough to brute-force the owner's fingerprint.
Regarding the SPI MITM attack that involves hijacking the user's fingerprint image, all tested Android devices are vulnerable to it, while iPhones are again resistant.
The researchers explain that the iPhone encrypts fingerprint data on the SPI, so any interception has little value in the context of the attack.
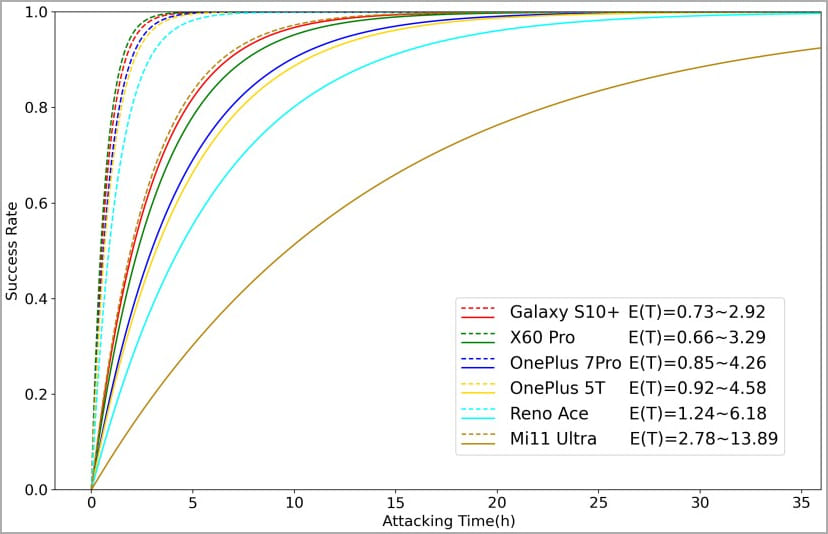
In summary, the conducted experiments showed that the time it takes to complete BrutePrint against vulnerable devices successfully ranges between 2.9 and 13.9 hours when the user has enrolled one fingerprint.
When multiple fingerprints are enrolled on the target device, the brute-forcing time drops to just 0.66 to 2.78 hours as the likelihood of producing matching images increases exponentially.
Conclusion
At first glance, BrutePrint may not seem like a formidable attack due to requiring prolonged access to the target device. However, this perceived limitation should not undermine its value for thieves and law enforcement.
The former would allow criminals to unlock stolen devices and extract valuable private data freely.
The latter scenario raises questions about privacy rights and the ethics of using such techniques to bypass device security during investigations.
This constitutes a rights violation in certain jurisdictions and could undermine the safety of certain people living in oppressive countries.
- Karlston
-

 1
1




Recommended Comments
There are no comments to display.
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.