A set of 38 Minecraft copycat games on Google Play infected devices with the Android adware 'HiddenAds' to stealthily load ads in the background to generate revenue for its operators.
Minecraft is a popular sandbox game with 140 million monthly active players, which numerous game publishers have attempted to recreate.
The Minecraft-like games hiding adware were downloaded by roughly 35 million Android users worldwide, mainly from the United States, Canada, South Korea, and Brazil.
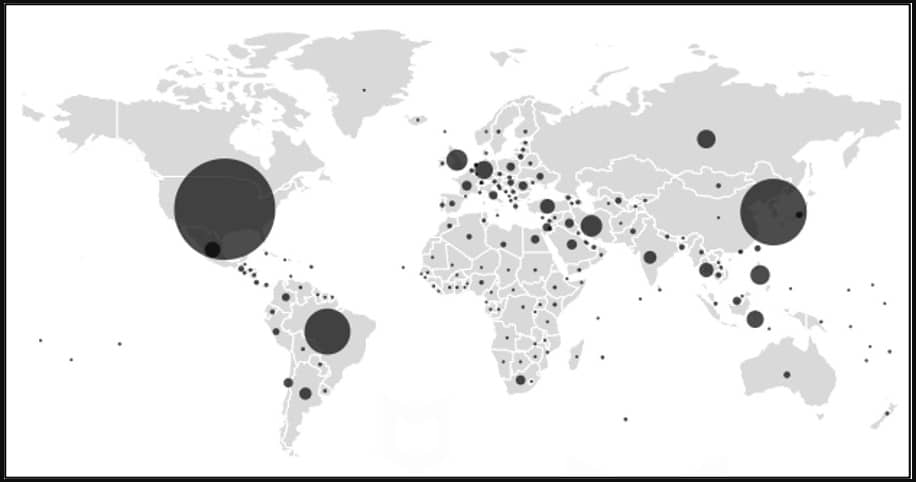
HiddenAds victim map (McAfee)
Those users didn't notice the malicious adware activity conducted in the background, as they could play the games as promised. Furthermore, any possible overheating, increased network data, or battery consumption caused by loading many ads may be perceived as caused by the game.
The adware set was discovered by McAfee's Mobile Research Team, a member of the App Defense Alliance created to protect Google Play from all types of threats.
After reporting and all apps have been reported and subsequently removed from the store now, with the most downloaded apps from this malicious set listed below:
- Block Box Master Diamond – 10 million downloads
- Craft Sword Mini Fun – 5 million downloads
- Block Box Skyland Sword – 5 million downloads
- Craft Monster Crazy Sword – 5 million downloads
- Block Pro Forrest Diamond – 1 million downloads
- Block Game Skyland Forrest – 1 million downloads
- Block Rainbow Sword Dragon – 1 million downloads
- Craft Rainbow Mini Builder – 1 million downloads
- Block Forrest Tree Crazy – 1 million downloads
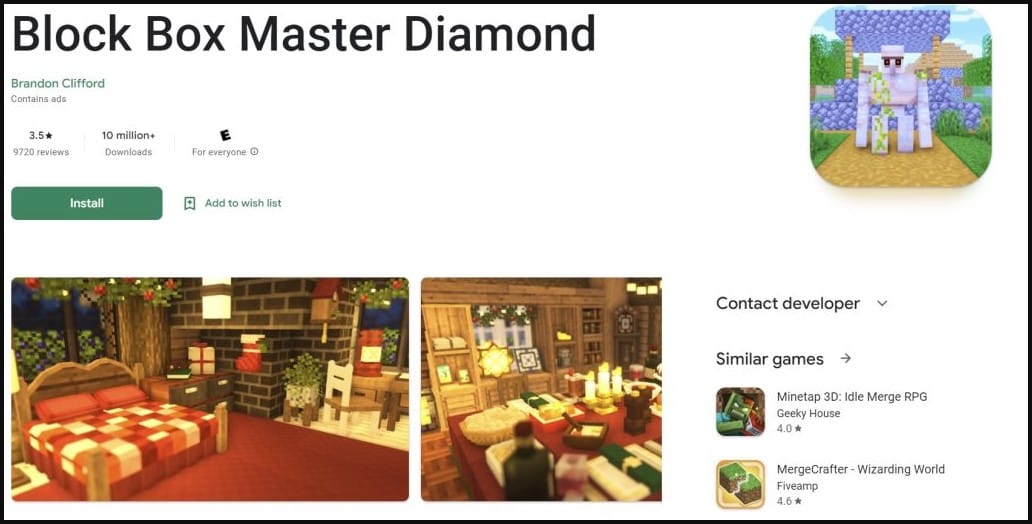
The most popular of the adware-ridden games (McAfee)
The advertisements are loaded in the background once the user launches the game, but nothing is displayed on the game screen.
Network traffic analysis, though, shows the exchange of several questionable packets generated by ad libraries of Google, AppLovin, Unity, and Supersonic, among others.
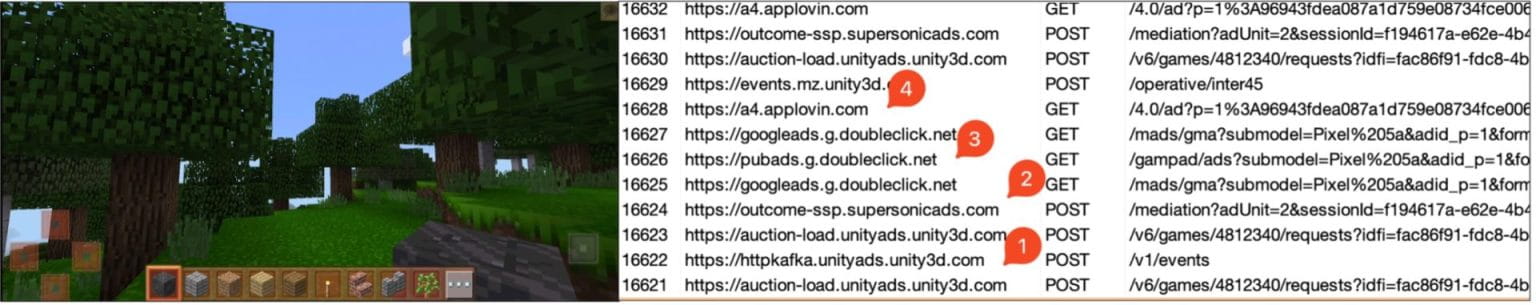
Suspicious network packets exchanged in the background (McAfee)
McAfee reports that the initial network packets on several of the apps share similar structures, using "3.txt" as the path in the form of "https://(random).netlify.app/3.txt," although the domains in each app are different.
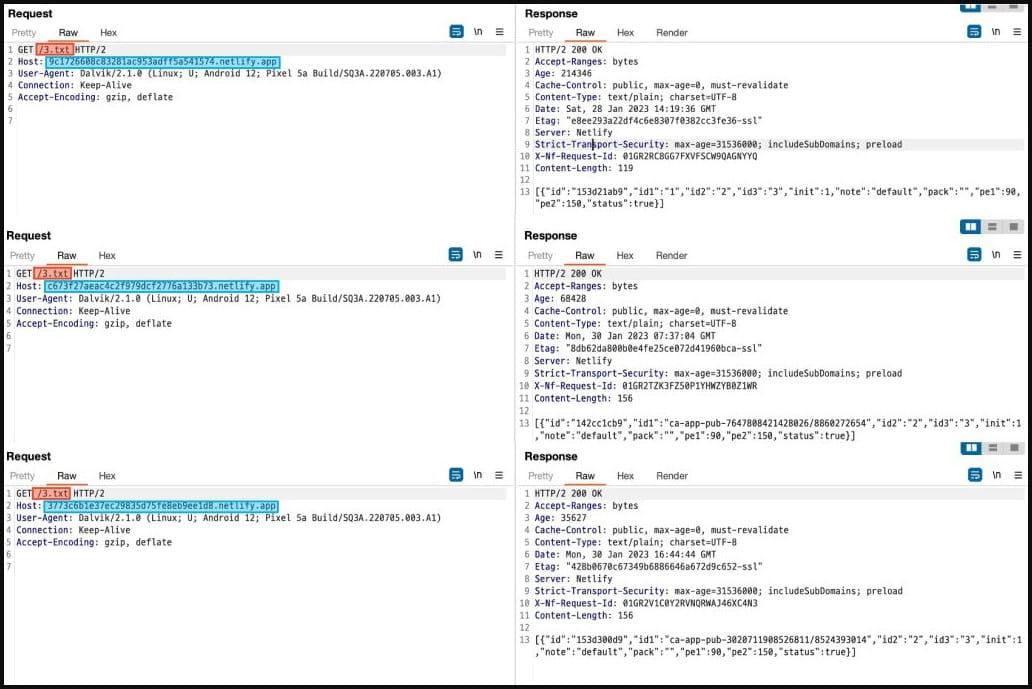
Initial packets from three of the set's apps (McAfee)
This, in combination with the similar names of the games, suggests a possible connection between them, making it likely that the same author created the apps. However, McAfee does not explicitly mention any definitive links.
While adware apps aren't considered particularly dangerous for users, it can reduce the performance of a mobile device, raise privacy concerns, and even potentially create security loopholes that might expose users to nastier infections.
Android users should check McAfee's report for a complete list of affected apps and manually remove them if they have not been removed already.




Recommended Comments
There are no comments to display.
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.