A set of Android malware droppers were found infiltrating the Google Play store to install banking trojans pretending to be app updates.
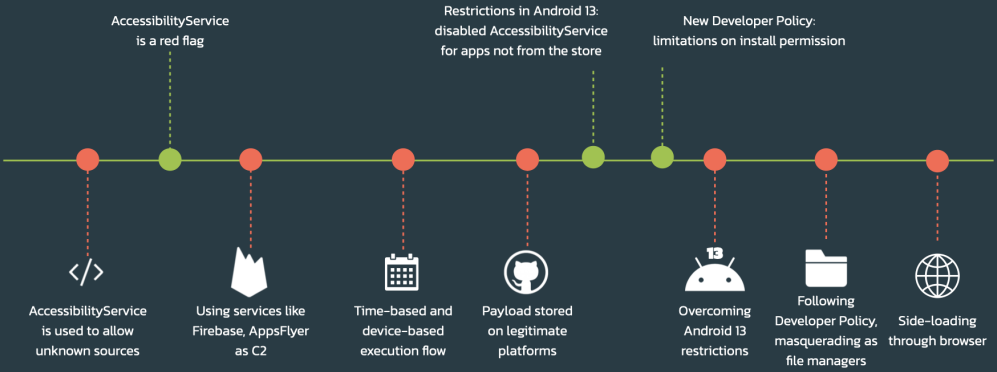
Malware droppers are a challenging category of apps to stop because they do not contain malicious code themselves and thus can more easily pass Google Play reviews when submitted to the store.
At the same time, they do not raise suspicion among the users as they provide the advertised functionality, and malicious behavior is conducted behind the scenes.
Researchers at Threat Fabric, who discovered the new set of droppers, report a rise in the use of droppers for Android malware distribution precisely because they can offer a stealthy pathway to infecting devices.
This is particularly important considering the ever-increasing restrictions and safeguards introduced with each major Android release, preventing malware from abusing permissions, fetching malicious modules from external resources, or using the Accessibility service to perform unlimited actions on the device.
The SharkBot campaign
The first dropper campaign spotted by Threat Fabric at the beginning of October 2022 pushes the banking trojan known as SharkBot.
SharkBot is an Android malware that can steal credentials through fake login prompts overlayed on legitimate website login forms, perform keylogging, steal and hide SMS messages, and take remote control over a mobile device.
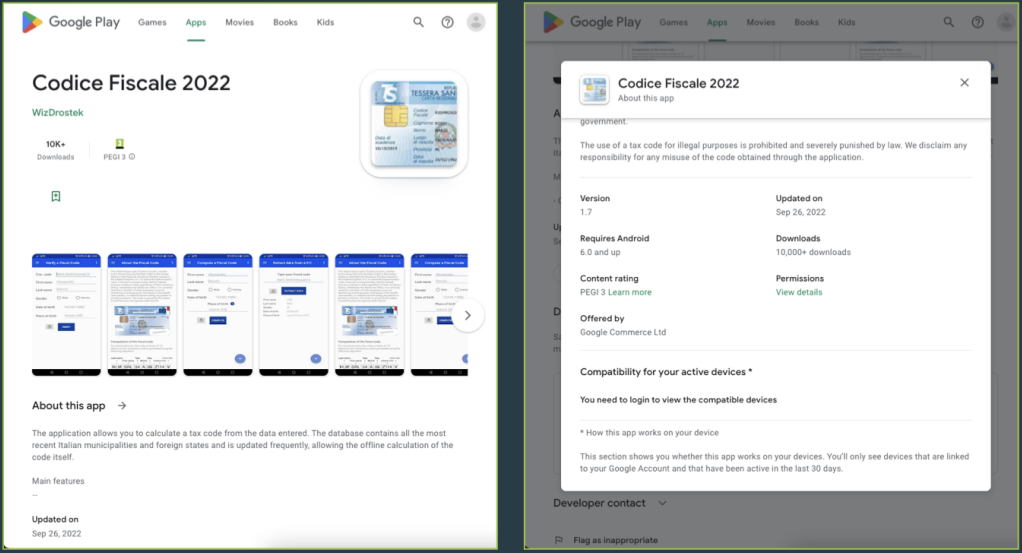
The researchers discovered two harmless-looking dropper apps, 'Codice Fiscale 2022' and 'File Manager Small, Lite,' that are used to install SharkBot on victims' mobile devices.
The first app, 'Codice Fiscale 2022,' is disguised as a tool to calculate tax payments in Italy and has been downloaded 10,000 times.
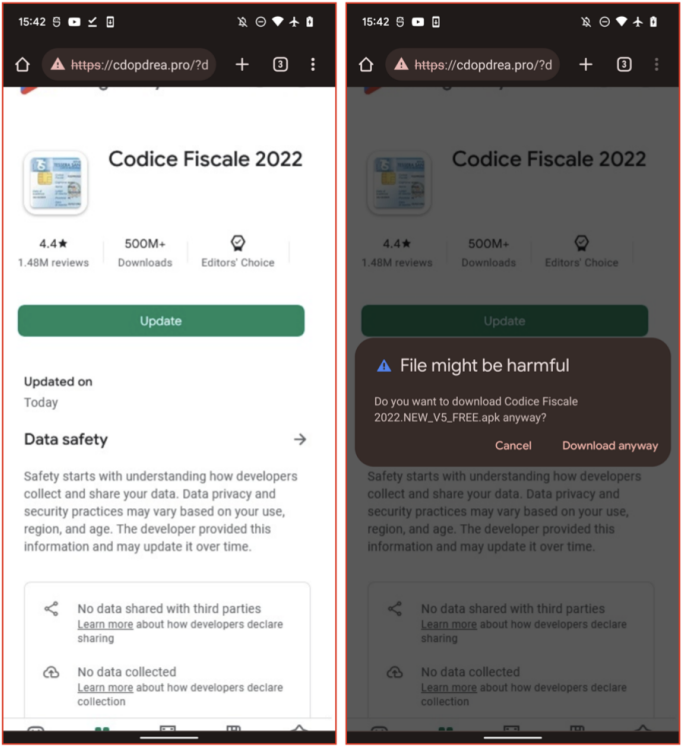
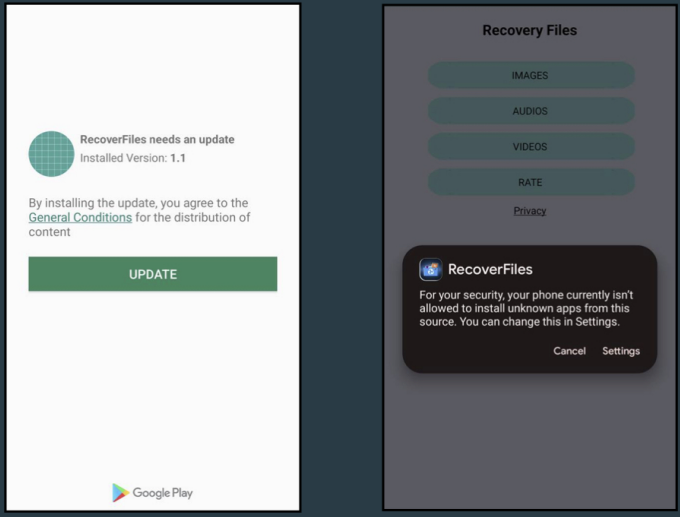
When a user installs the malicious dropper app, it will eventually prompt them to install a fake update, which installs the SharkBot malware on their device.
To install additional Android packages from a remote server, Google requires apps to request the 'REQUEST_INSTALL_PACKAGES.' However, newer versions of Android warn about the dangers of this permission, making it harder to convince users to install the 'update.'
The dropper instead opens a webpage made to appear like Google Play, tricking the user into tapping the "Update" button from the browser and thus bypassing the need for this permission.
The SharkBot version it drops targets Italian banks using fake login overlays, SMS interception for 2FA codes, keylogging, and a cookie stealer.
The File Manager dropper app delivers a more broadly-targeting SharkBot, configured to load overlays for banks in Italy, the UK, Germany, Spain, Poland, Austria, Australia, and the United States.
Vultur campaign
Another campaign using dropper apps delivers the Vultur malware, also a banking trojan operated by a threat actor known as the "Brunhilda Project."
Vultur can perform on-device fraud by offering its operators remote screen streaming and keylogging for social media and messaging apps.
The new variant distributed in the latest campaign also features a previously unseen system of UI logging, recording clicks, gestures, and all actions taken by the victim on the device.
Threat Fabric believes the malware developers added this feature to bypass the security flag restriction on Android, which prevents the content of certain app windows from appearing on screenshots or screencasts.
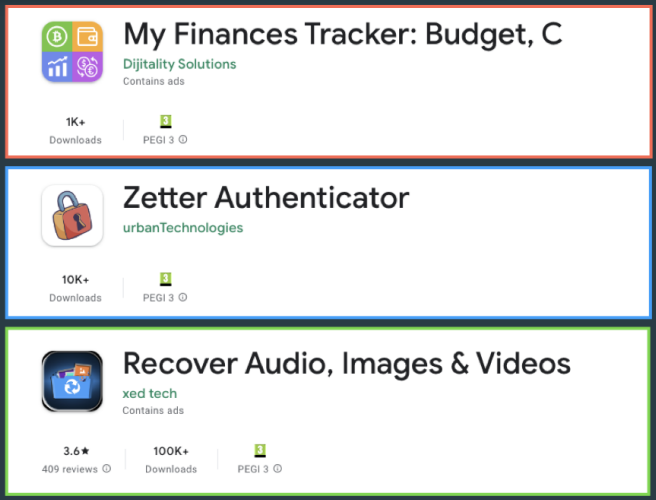
The droppers distributing Vultur are the following:
- ‘Recover Audio, Images & Videos’ – 100,000 downloads
- ‘Zetter Authentication’ – 10,000 downloads
- ‘My Finances Tracker’ – 1,000 downloads
Like the SharkBot droppers, these droppers also display a request to install a fake update, this time disguised as a Google Play notice. If the user allows the update to install, it will download and install the Vultur malware.
To evade detection when submitted to the Play Store, the installation logic isn’t contained in the dropper apps but instead loaded dynamically by an additional dex file sent by the attacker's command and control servers.
Moreover, the droppers use AES encryption to obfuscate their strings, to hide all functions from automated scanners.
Droppers gonna drop
The use of droppers has become a reliable method for malware installs to bypass scanners and fraud detection mechanisms; hence their deployment rate is expected to grow further.
"Distribution through droppers on Google Play still remains the most "affordable" and scalable way of reaching victims for most of the actors of different level," warns Threat Fabric.
"While sophisticated tactics like telephone-oriented attack delivery require more resources and are hard to scale, droppers on official and third-party stores allow threat actors to reach wide unsuspecting audience with reasonable efforts."
The only downside to droppers is the need to involve the victim in at least one manual action, as they must manually agree to the installation of the payloads, which is their most vulnerable moment.
However, using convincing websites and interfaces will likely continue to allow malware to be installed in this way.
Due to this, it is always important to never allow updates from remote sources if possible and to analyze URLs to confirm you are installing apps from the official Google Play Store rather than a third-party site.
- Matt
-

 1
1




Recommended Comments
There are no comments to display.
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.