Fast-growing e-commerce app Pinduoduo had an EvilParcel stow-away.
Android apps digitally signed by China’s third-biggest e-commerce company exploited a zero-day vulnerability that allowed them to surreptitiously take control of millions of end-user devices to steal personal data and install malicious apps, researchers from security firm Lookout have confirmed.
The malicious versions of the Pinduoduo app were available in third-party markets, which users in China and elsewhere rely on because the official Google Play market is off-limits or not easy to access. No malicious versions were found in Play or Apple’s App Store. Last Monday, TechCrunch reported that Pinduoduo was pulled from Play after Google discovered a malicious version of the app available elsewhere. TechCrunch reported the malicious apps available in third-party markets exploited several zero-days, vulnerabilities that are known or exploited before a vendor has a patch available.
Sophisticated attack
A preliminary analysis by Lookout found that at least two off-Play versions of Pinduoduo for Android exploited CVE-2023-20963, the tracking number for an Android vulnerability Google patched in updates that became available to end users two weeks ago. This privilege-escalation flaw, which was exploited prior to Google’s disclosure, allowed the app to perform operations with elevated privileges. The app used these privileges to download code from a developer-designated site and run it within a privileged environment.
The malicious apps represent “a very sophisticated attack for an app-based malware,” Christoph Hebeisen, one of three Lookout researchers who analyzed the file, wrote in an email. “In recent years, exploits have not usually been seen in the context of mass-distributed apps. Given the extremely intrusive nature of such sophisticated app-based malware, this is an important threat mobile users need to protect against.”
Hebeisen was assisted by Lookout researchers Eugene Kolodenker and Paul Shunk. The researcher added that Lookout’s analysis was expedited and that a more thorough review will likely find more exploits in the app.
Pinduoduo is an e-commerce app for connecting buyers and sellers. It recently was reported to have 751.3 million average monthly active users. While still smaller than its Chinese rivals Alibaba and JD.com, PDD Holdings, Pinduoduo’s publicly traded parent company, has become the fastest-growing e-commerce firm in that country.
After Google removed Pinduoduo from Play, PDD Holdings representatives denied the claims any of its app versions were malicious.
“We strongly reject the speculation and accusation that the Pinduoduo app is malicious from an anonymous researcher,” they wrote in an email. “Google Play informed us on March 21 morning that Pinduoduo APP, among several other apps, was temporarily suspended as the current version is not compliant with Google’s Policy, but has not shared more details. We are communicating with Google for more information.”
The company representatives didn’t respond to emails that asked follow-up questions and disclosed the results of Lookout’s forensic analysis.
Suspicions about the Pinduoduo app first surfaced last month in a post (English translation here) from a research service calling itself Dark Navy.
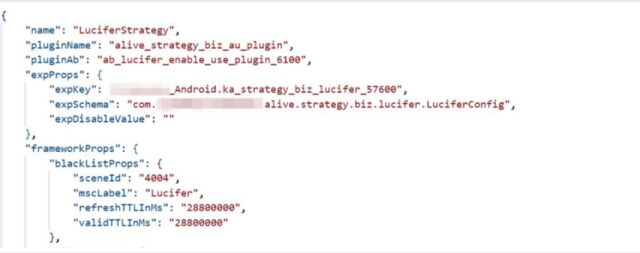
The English translation said that “well-known Internet manufacturers will continue to dig out new Android OEM-related vulnerabilities and implement vulnerability attacks on mainstream mobile phone systems in the current market in their publicly released apps.” The post didn’t name the company or the app, but it did say the app used a “bundle feng shui-Android parcel serialization and deserialization [exploit] that seems unknown in recent years.” The post included several code snippets found in the allegedly malicious app. One of those strings is "LuciferStrategy."
A few weeks later, someone with the username davinci1012 published a Github post with the translated name “Pinduoduo backdoor.” It referred to the Dark Navy post and provided code and steps researchers could follow to pierce anti-analysis defenses and find an alleged exploit in Pinduoduo Android apps published prior to March 5. A follow-up Github post a few days later included still more details claiming to show the malicious functionality in the Pinduoduo apps. Google removed the Pinduoduo app from Play a few days after the second davinci1012 post went live.
Lookout’s forensic analysis of two Pinduoduo APK app samples released prior to March 5—one with the SHA256 cryptographic signature 3c5a0eba055633f0444b9f69ae70dc93938ecb6b5df34d8e677c96d7c77f113f and the other 234aa7a4a70026e0585a3bf2acae1cb21d414aeb6f3d76955e92e445de998944—has determined that both contain malicious code that exploits CVE-2023-20963, the Android privilege-escalation vulnerability that wouldn’t become public until March 6 and wouldn’t be patched in user devices for up to two weeks later. Both of these malicious APKs were signed with the same private signing key used to sign the benign Pinduoduo app available in Google Play.
According to the DarkNavy post, the malicious Pinduoduo app includes functionality allowing for the app to be installed covertly with no ability to be uninstalled, falsely inflating the number of Pinduoduo daily active users and monthly active users, uninstalling competitor apps, stealing user privacy data, and evading various privacy compliance regulations.
Dark Navy and davinci1012 vindicated
Lookout’s analysis was performed over a span of two days, which isn’t enough time to review all the relevant technical aspects of the two Pinduoduo app samples. Further complicating the analysis is the downloading of a second-stage payload from the Internet.
Lookout has been unable to attribute it to PDD Holdings since this stage isn’t digitally signed.
Nonetheless, the analysis appears to validate the accuracy of the Dark Navy write-up. Besides determining the presence of the Android zero-day, it also uncovered evidence of:
- Adding widgets to infected devices
- Tracking usage stats of installed apps
- Parsing notifications
- Accessing Wi-Fi and Location information
“We're far from having a full and thorough picture of what they all do (in total, there are over 30 DEX files) but preliminary analysis essentially seems to support the claims,” Hebeisen wrote. “There is also some code that looks like it would be consistent with preventing apps from being uninstalled. So from what we can see, the claims seem to reflect what's in the files.”
There are other consistencies. For one, the “LuciferStrategy” string that’s shown in the Dark Navy post appears in the samples Lookout analyzed. Additionally, the analyzed exploit chain uses EvilParcel, a class of exploit for privilege-escalation vulnerabilities that has been in use since 2012. Dark Navy described the zero-day exploited by the app as a “bundle feng shui-Android parcel serialization and deserialization” exploit, a description that (allowing for translation) accurately captures the gist of EvilParcel.
“EvilParcel exploits are a class of exploits targeting a related set of vulnerabilities of which CVE-2023-20963 is one," Lookout's Kolodenker wrote. “These exploits allow for usage of an old privilege escalation technique (originally from 2012) that was previously patched. However, that fix can now be bypassed with EvilParcel.





The Dark Navy post references another Android zero-day tracked as CVE-2021-25337 that Google discovered was being exploited in Samsung phones. There is no indication that the malicious Pinduoduo app exploited this vulnerability at all.
With little doubt that zero-day exploit code appears in at least two Pinduoduo app samples signed with the official key, there are a few possible conclusions. The code could be present due to:
- An intentional distribution of malicious code by Pinduoduo developers
- The work of a malicious insider
- A leaked secret key obtained by an outside party
- A supply chain attack that compromised the software build system for the Pinduoduo app
Under the circumstances, the removal of Pinduoduo from Google Play seems warranted.
With no evidence of malicious versions in Play or the App Store, Pinduoduo users who obtained their app from either of these sources aren’t affected. Android users who obtained their app from a third-party market—as virtually all in China do—aren’t as lucky. It’s not known how many third-party downloads Pinduoduo has, but given the wide reach of the app, the number is surely in the millions, if not hundreds of millions.




Recommended Comments
There are no comments to display.
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.