Security researchers at McAfee have discovered a set of 16 malicious clicker apps that managed to sneak into Google Play, the official app store for Android.
Clicker apps are a special category of adware that loads ads in invisible frames or in the background and clicks them to generate revenue for their operators.
The effect on the device may be a drop in performance, overheating, increased battery usage, and inflated mobile data charges.
All 16 apps have been removed from Google Play after McAfee reported them. However, they still amassed an install count of 20 million.
.png)
The nastiest of the bunch is DxClean, which was installed five million times before it being removed. It had a relatively positive overall user rating of 4.1 out of 5 stars.

DxClean posed as a system cleaner and optimizer, promising to detect causes of system slowdowns and stop advertisement annoyances while performing the exact opposite actions in the background.
Clicker app functions
After launch, the apps download their configuration from a remote location via an HTTP request and register an FCM (Firebase Cloud Messaging) listener to receive push messages.
These messages contain instructions for the clickers, such as which functions to call and what parameters to use.
“When an FCM message receives and meets some condition, the latent function starts working,” McAfee explains in the report.
“Mainly, it is visiting websites which are delivered by FCM message and browsing them successively in the background while mimicking user’s behavior,” the researchers add.
The auto-clicking function is handled by the ‘click.cas’ component, while the agent managing the hidden adware services is ‘com.liveposting’.
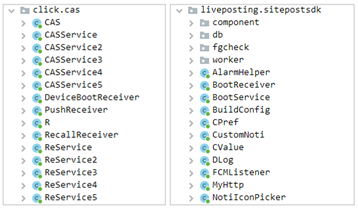
The two libraries supporting the clickers' operation - (McAfree)
McAfee analysts say that the liveposting SDK can operate on its own, too, possibly to create only ad impressions, but recent versions of the apps feature both libraries.
The victim never interacts with the opened websites and is unlikely to realize the underground processes that generate profit for the remote operators.
To stay below the user's radar, the malicious operation does not begin in the first hour after installing the app delays its start when the user is actively using the device.
Some ways to discover if apps of this kind are present on the device, users should check battery and internet usage. If the system stayed unused for a period, there is no justification for higher battery drainage and increased mobile data consumption.
For the complete list of the 16 clicker apps, check out the indicators of compromise section at the bottom of McAfee’s report.




Recommended Comments
There are no comments to display.
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.