A new mobile malware campaign since March 2023 pushes the Android banking trojan 'Anatsa' to online banking customers in the U.S., the U.K., Germany, Austria, and Switzerland.
According to security researchers at ThreatFabric, who have been tracking the malicious activity, the attackers are distributing their malware via the Play Store, Android's official app store, and already have over 30,000 installations via this method alone.
ThreatFabric discovered a previous Anatsa campaign on Google Play in November 2021, when the trojan was installed over 300,000 times by impersonating PDF scanners, QR code scanners, Adobe Illustrator apps, and fitness tracker apps.
New Anatsa campaign
In March 2023, after a six-month hiatus in malware distribution, the threat actors launched a new malvertizing campaign that leads prospective victims to download Anatsa dropper apps from Google Play.
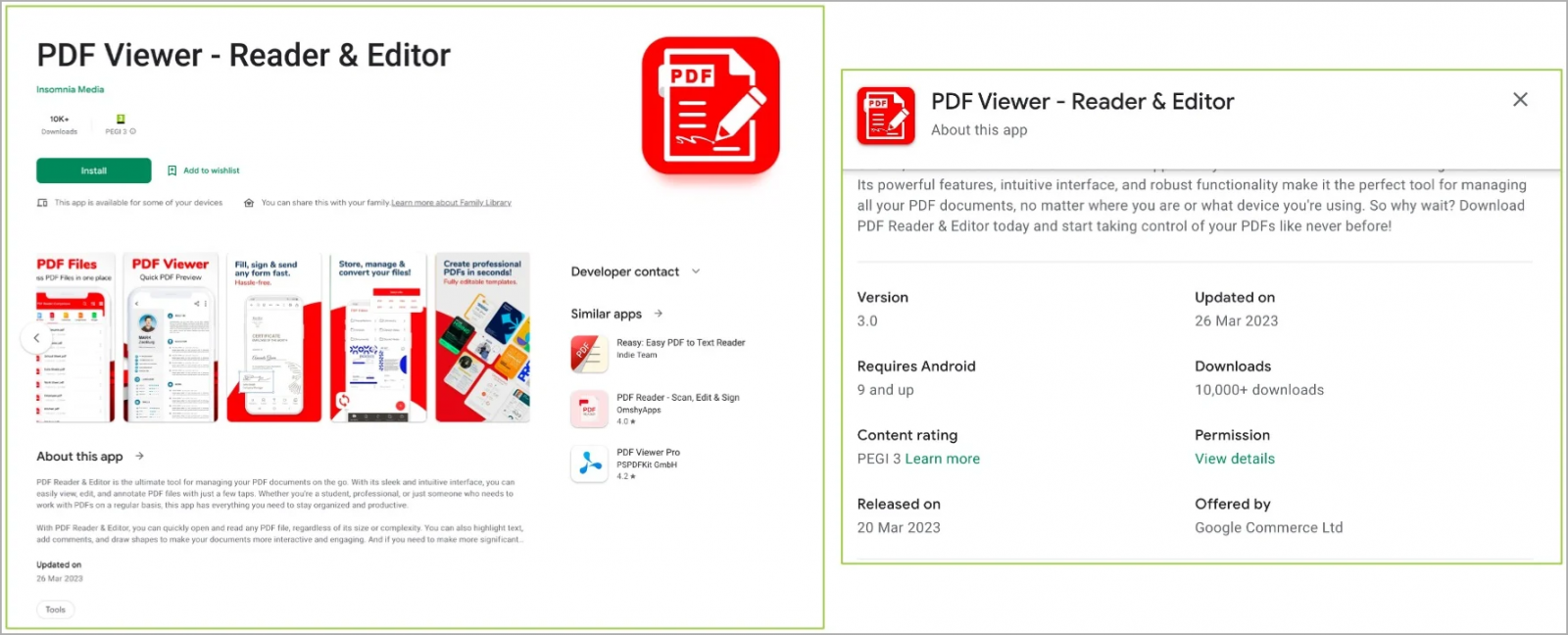
Malicious app on Google Play (ThreatFabric)
The malicious apps continue to belong to the office/productivity category, posing as PDF viewer and editor apps and office suites.
Whenever ThreatFabric reported the malicious app to Google and it was removed from the store, the attackers returned quickly by uploading a new dropper under a new guise.
In all five cases of the identified malware droppers, the apps were submitted onto Google Play in clean form and were later updated with malicious code, likely to evade Google's stringent code review process on the first submission.
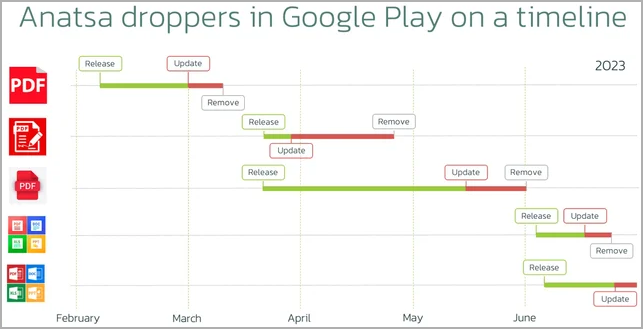
Timeline of malicious dropper app submissions (ThreatFabric)
Once installed on the victim's device, the dropper apps request an external resource hosted on GitHub, from where they download the Anatsa payloads masqueraded as text recognizer add-ons for Adobe Illustrator.
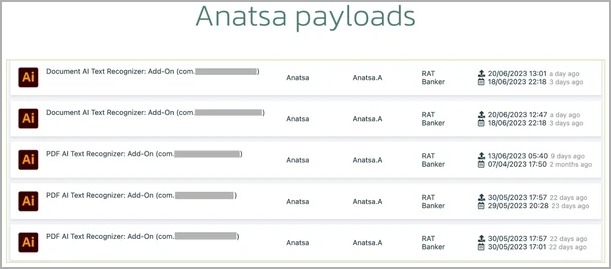
Payloads retrieved from GitHub (ThreatFabric)
Anatsa collects financial information such as bank account credentials, credit card details, payment information, etc., by overlaying phishing pages on the foreground when the user attempts to launch their legitimate bank app and also via keylogging.
In its current version, the Anatsa trojan supports targeting nearly 600 financial apps of banking institutions from around the world.
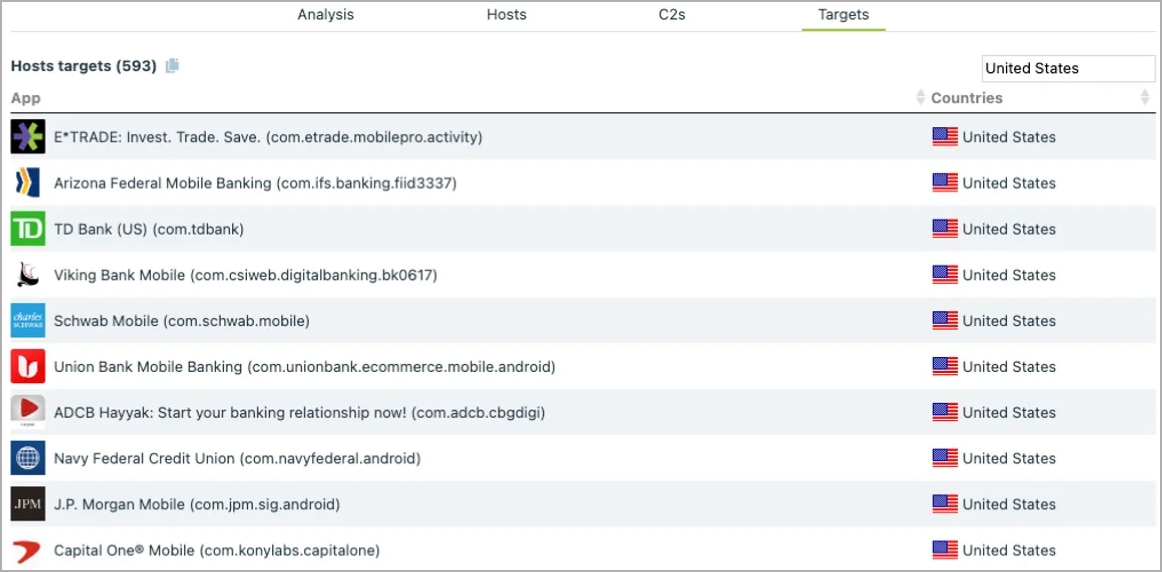
Some of the U.S. banks targeted by Anatsa (ThreatFabric)
Anatsa uses the stolen information to perform on-device fraud by launching the banking app and performing transactions on the victim's behalf, automating the money-stealing process for its operators.
"Since transactions are initiated from the same device that targeted bank customers regularly use, it has been reported that it is very challenging for banking anti-fraud systems to detect it," explains ThreatFabric.
The stolen amounts are converted to cryptocurrency and passed through an extensive network of money mules in the targeted countries, who will keep a portion of the stolen funds as a revenue share and send the rest to the attackers.
Protecting Android
As malware campaigns, such as Anatsa, expand their targeting to other countries, users must be extra vigilant about the apps they install on Android devices.
Users should avoid installing apps from dubious publishers, even if those are on a well-vetted store like Google Play. Always check the reviews and see if a pattern of reports indicates malicious behavior.
Furthermore, if possible, avoid apps with few installs and reviews and instead install apps that are well-known and commonly cited on websites.
As many apps on Google Play have the same name as the malicious apps, it is recommended to check the ThreatFabric report's appendix for the list of package names and signatures that are pushing Anatsa and remove them immediately from your Android device if installed.
BleepingComputer asked Google to explain how Anatsa's operators can submit malicious updates on their dropper apps on the Play Store and replace the reported droppers quickly, but a comment wasn't available by publication.
Update 6/27 - A Google spokesperson has sent BleepingComputer the following comment:
All of these identified malicious apps have been removed from Google Play and the developers have been banned.
Google Play Protect also protects users by automatically removing apps known to contain this malware on Android devices with Google Play Services.
- Karlston
-

 1
1




Recommended Comments
There are no comments to display.
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.