Amazon Simple Storage Service (S3) will now automatically encrypt all new objects added on buckets on the server side, using AES-256 by default.
While the server-side encryption system has been available on AWS for over a decade, the tech giant has enabled it by default to bolster security.
Administrators will not have to take any actions for the new encryption system to affect their buckets, and Amazon promises it won't have any negative performance impact.
"This change puts another security best practice into effect automatically—with no impact on performance and no action required on your side," reads Amazon's announcement.
"S3 buckets that do not use default encryption will now automatically apply SSE-S3 as the default setting. Existing buckets currently using S3 default encryption will not change."
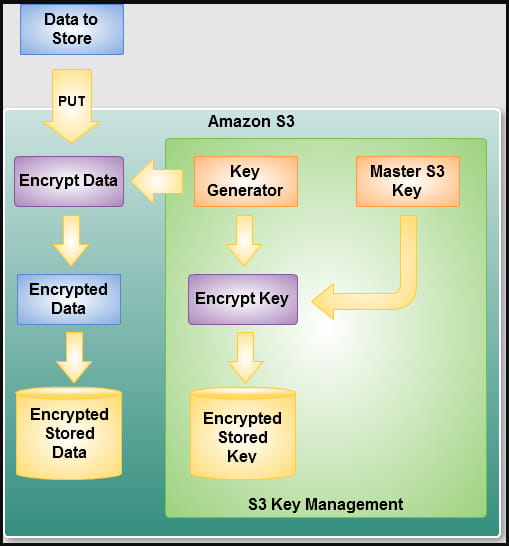
AWS server-side encryption (Amazon)
Administrators may leave the system to encrypt at the default 256-bit AES or choose one of the alternative methods, namely SSE-C or SSE-KMS.
The first option (SSE-C) gives bucket owners control of the keys, while the second (SSE-KMS) lets Amazon do the key management. However, bucket owners can set different permissions for each KMS key to maintain more granular control over the asset access system.
To confirm that the changes have been applied to your buckets, admins can enable data events logging at no extra cost. Then perform a test object upload, and look in the event logs for the "SSEApplied": "Default_SSE_S3." field in the log for the uploaded file.
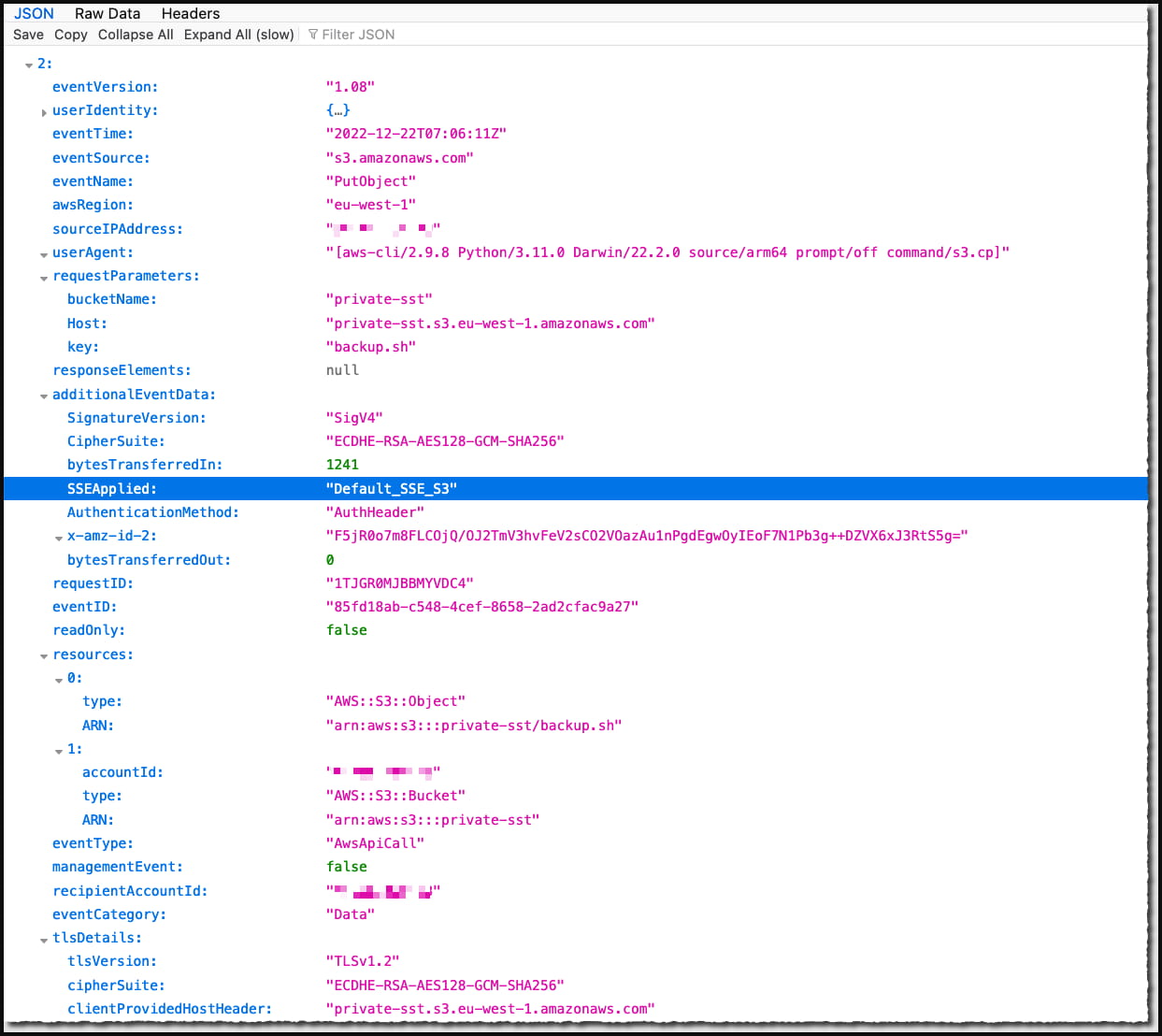
Data event log containing the encryption validating field (Amazon)
To retroactively encrypt objects already in S3 buckets, follow this official guide.
Solving a big security problem
Database leaks have been a bane for security for many years now, with poor practices and configuration mistakes often exposing the sensitive details of millions of people.
Two notable examples concerning Amazon S3 storage buckets are the leak of data from 123 million households in December 2017 and the leak of 540 million records of Facebook users in April 2019.
If that data had been encrypted, the leaks wouldn't have had nearly as dire consequences for the exposed individuals, but unfortunately, due to overhead costs, operational complexity, and performance sacrifices, database encryption is commonly avoided.
Amazon's move to make server-side encryption a "zero-click" process is a fundamental step towards better security and is bound to lessen the impact of upcoming data incidents that will inevitably happen.
As for the strength of the 256-bit AES encryption algorithm, it is still considered one of the strongest available, with the U.S. government recommending its use. Furthermore, despite numerous attempts to break it, the scheme has no known weaknesses.
- Karlston and Matt
-

 2
2





Recommended Comments
There are no comments to display.
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.