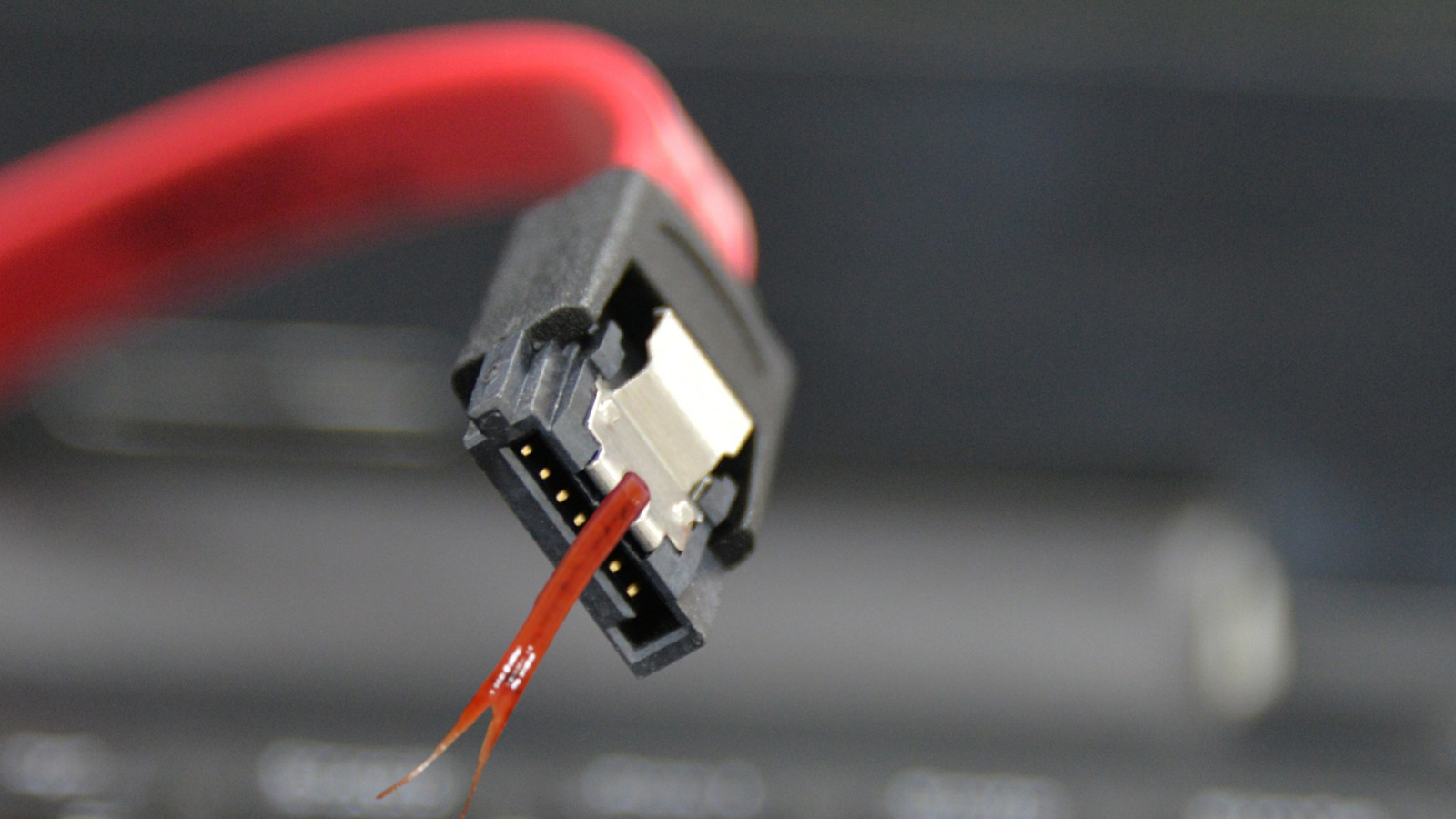
A security researcher has found a new way to steal data from air-gapped systems by using serial ATA (SATA) cables present inside most computers as a wireless antenna that sends out data via radio signals.
Air-gapped systems are used in critical environments that need to be physically isolated from less secure networks, such as those connected to the public internet.
They are typically seen in military, government, and nuclear development programs, as well as industrial control systems in critical sectors (e.g. oil, gas, financial, electric power).
Dubbed “SATAn”, the attack was discovered by Mordechai Guri, the Head of R&D of The Cyber Security Research Labs at Ben-Gurion University in Israel, and could theoretically help an adversary steal sensitive information.
SATAn attack
For a SATAn attack to succeed, an attacker first needs to infect the target air-gapped system. While this is not an easy task, there are reports of physical initial compromise since 2010, Sutxnet being the most notorious one.
The piece of malware planted on an air-gapped network can target the sensitive information and prepare it for exfiltration by modulating and encoding it.
The researcher found that SATA cables in computers can deliver over a radio channel between 5.9995 and 5.9996 GHz electromagnetic signals that correspond to specific characters.
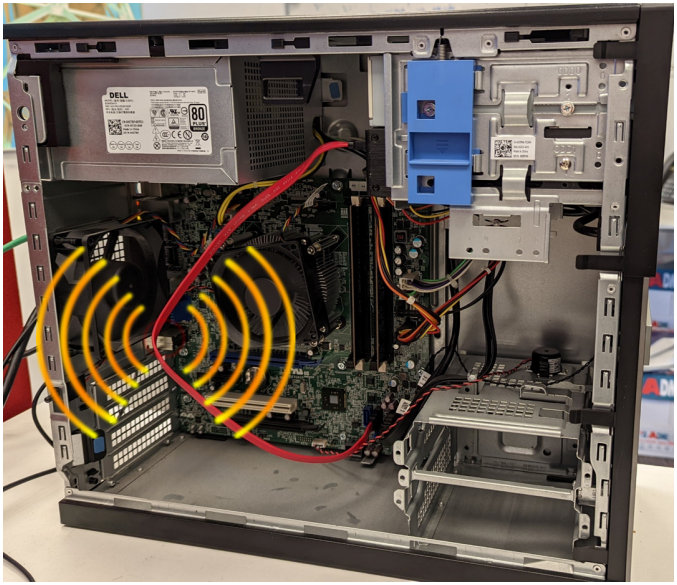
The SATA interface can emit radio signals during certain read and write operations. Malware used in SATAn attacks can hijack legitimate software processes to perform very specific read/write functions that reflect the content of the stolen data.
During the research, Guri was able to generate electromagnetic signals to deliver the word 'SECRET' from an air-gapped system to a nearby computer. The receiver needs to identify the start of a valid transmission from SATA 3 cables.
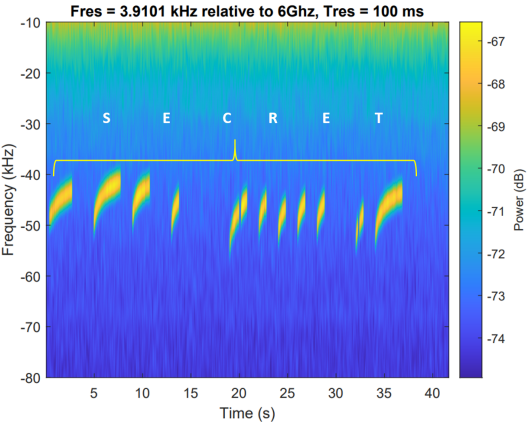
“In a real attack scenario, the receiver might be implemented as a process in the nearby computer or embedded in a dedicated hardware receiver,” the researcher explains in a technical paper.
Attack limitations
Through experimentation with various systems and settings, the researcher has determined that the maximum distance from the air-gapped computer to the receiver cannot be greater than 120 cm (3.9 ft), or the bit error rate increases too much to ensure the integrity of the message (above 15%).
The distance between the transmitter and the receiver also influences the time required to send the data. Depending on the gap, "sequences of three bits with 0.2 sec, 0.4 sec, 0.6 sec, 0.8 sec, 1.0 sec, and 1.2 sec have been modulated and received."
We transmitted the data with a bit rate of 1 bit/sec, which is shown to be the minimal time to generate a signal which is strong enough for modulation
Also, the researcher has found that when virtual machines are abused to perform the data-translating read/write operations, the signal quality on the SATA cable is reduced significantly.
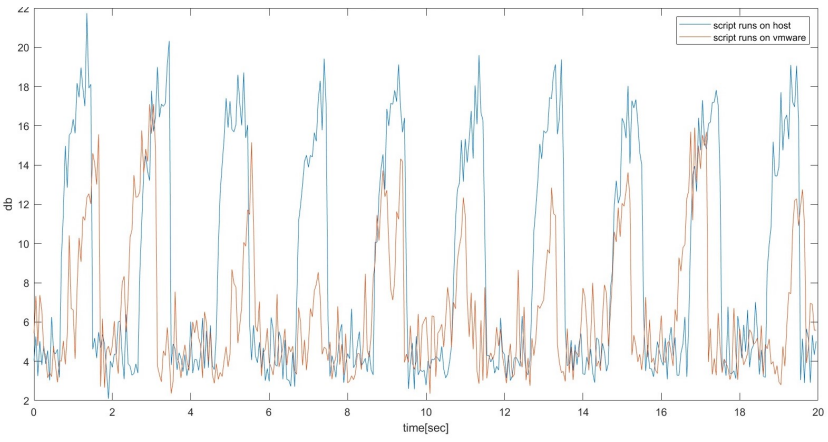
An interesting countermeasure proposed in the paper is that of a SATA jammer, which monitors for suspicious read/write operations from legitimate applications and adds noise to the signal.
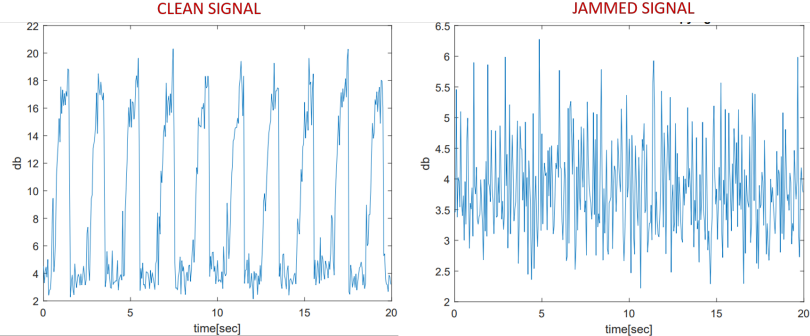
However, excessive disk usage for generating the jamming signal accelerates hardware wear, and distinguishing between legitimate and malicious operations would be challenging in a runtime environment.
Mordechai Guri is has been involved in more than two dozen projects researching various channels that allow stealing data from air-gapped networks covertly.
Over the years, Guri and his team demonstrated that isolated networks can still allow leaking of sensitive information via signals (light, vibrations, sound, heat, magnetic or electromagnetic fields) generated by components present in the systems like monitors, speakers, cables, CPU, HDDs, cameras, keyboards.
- aum
-

 1
1


3175x175(CURRENT).thumb.jpg.b05acc060982b36f5891ba728e6d953c.jpg)
Recommended Comments
There are no comments to display.
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.