A new Sugar Ransomware operation actively targets individual computers, rather than corporate networks, with low ransom demands.
First discovered by the Walmart Security Team, 'Sugar' is a new Ransomware-as-a-Service (RaaS) operation that launched in November 2021 but has slowly been picking up speed.
The name of the ransomware is based on the operation's affiliate site discovered by Walmart at 'sugarpanel[.]space'.
Unlikely most ransomware operations you read about in the news, Sugar does not appear to be targeting corporate networks but rather individual devices, likely belonging to consumers or small businesses.
As such, it is not clear how the ransomware is being distributed or infecting victims.
The Sugar Ransomware
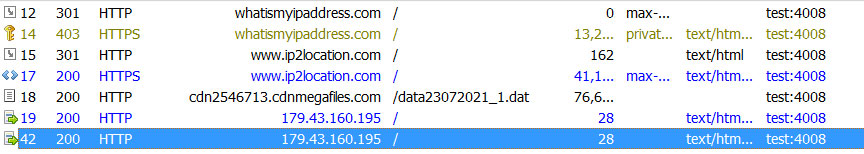
When launched, the Sugar Ransomware will connect to whatismyipaddress.com and ip2location.com to get the device's IP address and geographic location.
It will then proceed to download a 76MB file from http://cdn2546713.cdnmegafiles[.]com/data23072021_1.dat, but it is unclear how this file is used.
Finally, it will connect to the ransomware operation's command and control server at 179.43.160.195, where it transmits and receives data related to the attack. The ransomware will continue to call back to the command and control server as it is executed, likely updating the RaaS with the status of the attack.
Source: BleepingComputer
When encrypting files, the ransomware will encrypt every file except those listed in the following folders or have the following file names:
Excluded folders: \windows\ \DRIVERS\ \PerfLogs\ \temp\ \boot\ Excluded files: BOOTNXT bootmgr pagefile .exe .dll .sys .lnk .bat .cmd .ttf .manifest .ttc .cat .msi;
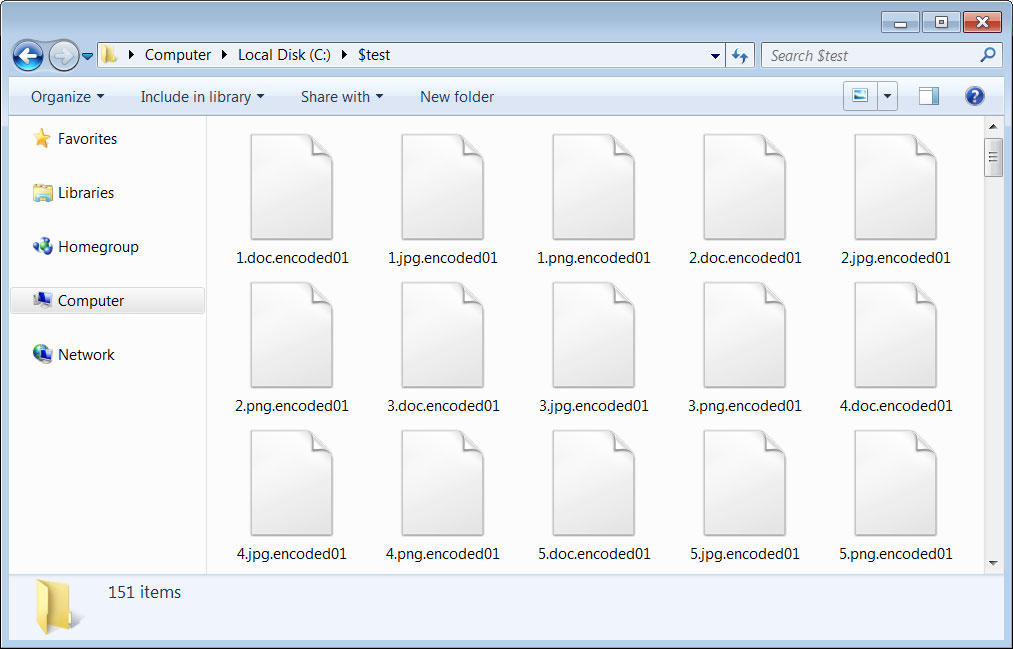
The Walmart researchers say that the ransomware encrypts files using the SCOP encryption algorithm. The encrypted files will have the .encoded01 extension appended to file names, as shown below.
Source: BleepingComputer
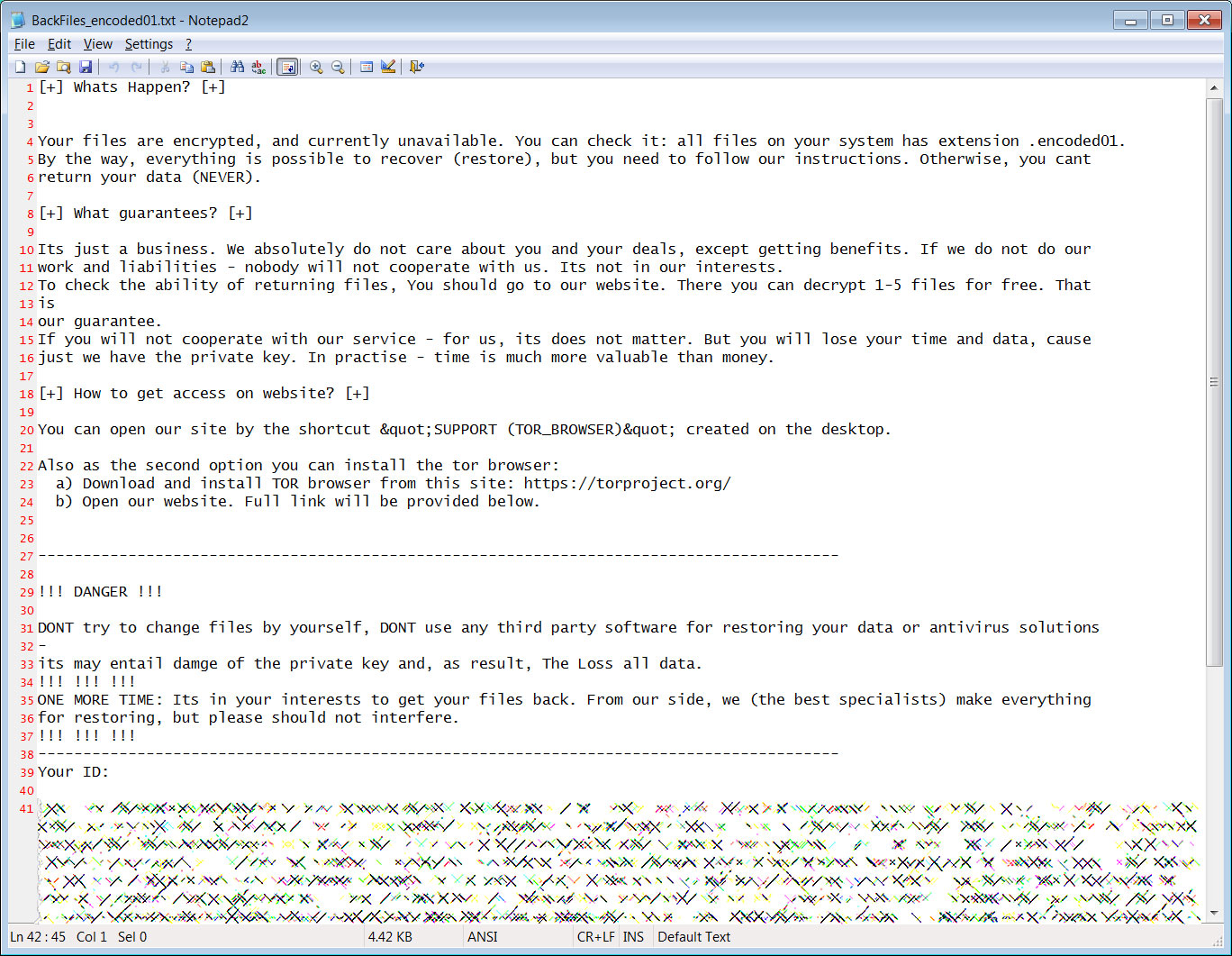
The ransomware will also create ransom notes named BackFiles_encoded01.txt in each folder that was scanned for files on the computer.
This ransom note contains information on what happened to the victim's files, a unique ID, and a link to a Tor site with information on how to pay the ransom. The Tor site is located at chat5sqrnzqewampznybomgn4hf2m53tybkarxk4sfaktwt7oqpkcvyd.onion.
Source: BleepingComputer
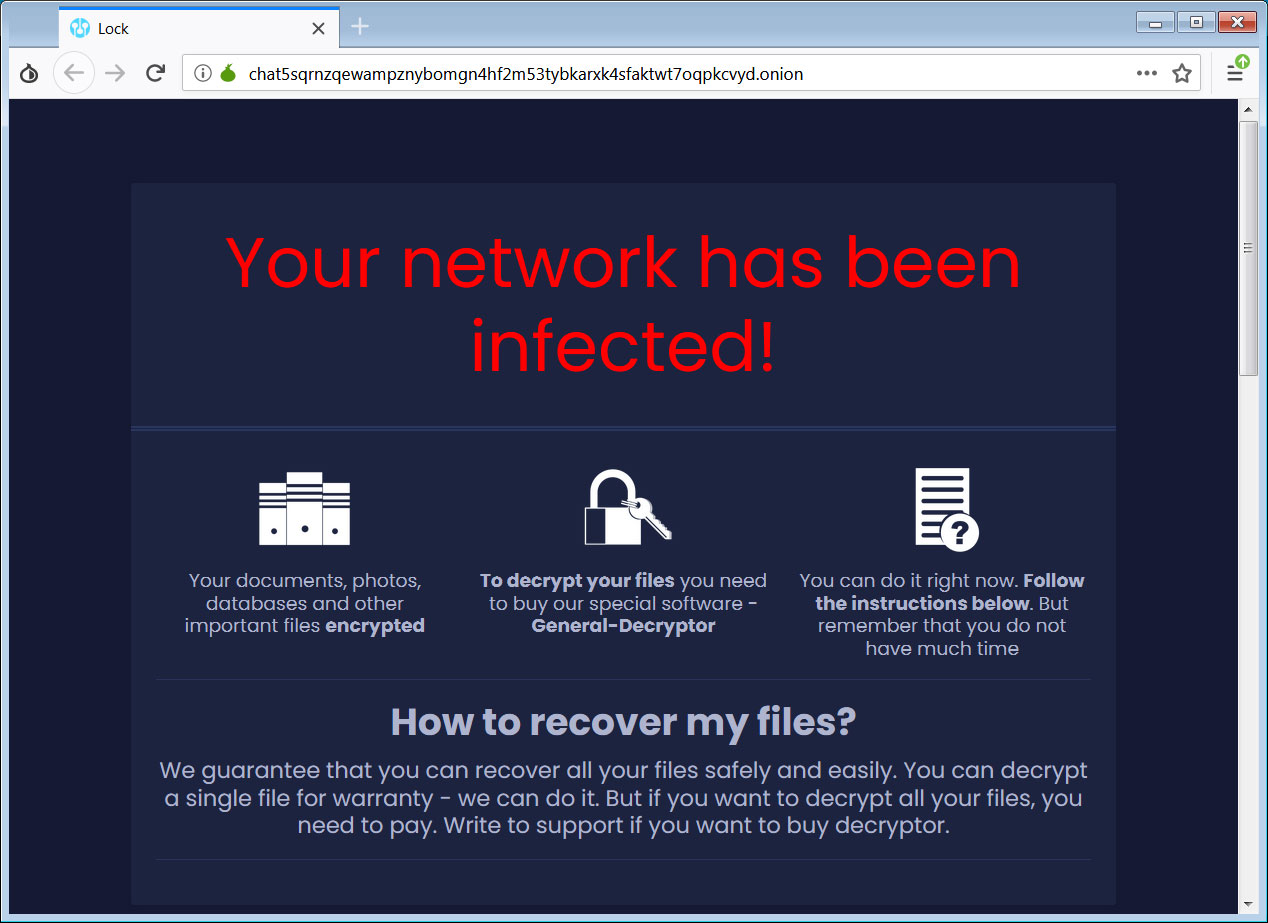
When visiting the Tor site, the victim will be presented with their own page that contains the bitcoin address to send a ransom, a chat section, and the ability to decrypt five files for free.
Source: BleepingComputer
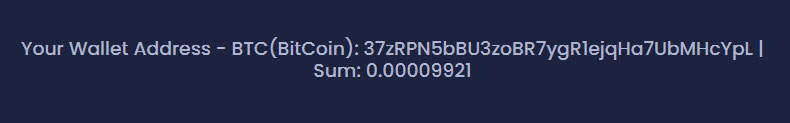
The ransom demands by this operation are very low, with attacks seen by BleepingComputer demanding only a few hundred dollars to receive a key. Strangely, on our test box, the resulting ransom demand was only 0.00009921 bitcoins, worth $4.01.
As BleepingComputer tested the ransomware on a virtual machine with a small number of files, it could indicate that the ransomware is generating ransom amounts based on the number of encrypted files.
Source: BleepingComputer
Unlike most ransomware infections, the malware executable runs even after encryption has finished. However, no auto-start setting is created, and it does not appear to continue encrypting new documents.
At this time, it is unclear if the ransomware has any weaknesses that could allow decryption for free. We will update this article as more information becomes available.
Furthermore, if you are affected by this ransomware, please let us know how you became infected.
- aum
-

 1
1



3175x175(CURRENT).thumb.jpg.b05acc060982b36f5891ba728e6d953c.jpg)
Recommended Comments
There are no comments to display.
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.