You don't have to be a sysadmin to keep your Linux desktop distribution safe from cybersecurity threats. But you do have to follow a few best practices.
It is no secret that Linux is a far more secure option than Windows. From the ground up, Linux was designed to be highly secure. Since I started using Linux (back in '97), I've only had one cybersecurity threat arise, which was a rootkit on a server I inherited. Sadly, that server was so badly compromised that I had to re-install the OS and start from scratch.
That was the only instance, in decades, of having to suffer the consequence of a security breach. Otherwise, it's been smooth sailing.
You, too, can enjoy the heightened security that comes with the Linux OS. However, you shouldn't just assume that you can install Linux and never worry about security again. My take on security is if a device is connected to a network, it's vulnerable.
To that end, I thought I'd share some advice that even those who are brand new to Linux can easily follow. Don't worry, I'm not going to have you editing init scripts, issuing complicated iptables commands, or installing software like fail2ban. Instead, this is all about what new users can do to help prevent malware, ransomware, or other attacks.
If you're a Linux admin, this might be a good thing to share with end users who are using Linux as their daily driver operating system.
With that said, let's get to the tips.
1. Upgrade regularly
This is the first piece of advice I give to any user, regardless of the operating system they use and I'm always shocked at how many people ignore it.
You see, upgrades aren't just about getting new features. More important in those upgrades are the security patches that address vulnerabilities. I check (and apply) updates daily. Sometimes those updates are minor but other times they include crucial patches that fix critical Common Vulnerabilities and Exposures (CVEs).
No matter what Linux distribution you've chosen, check daily (at best) or weekly for updates. As soon as you see updates available, apply them and (if the kernel is upgraded) reboot when the process completes.
2. Don't install apps from unknown sources
Similar to the advice I give to Android users, the safest thing you can do is only install applications from the built-in package manager(s). Whether your system uses apt, dnf, snap, flatpak, pacman, or zypper, I would highly recommend you only install apps using those methods.
I know what you're thinking: That removes a world of applications that can be installed. Although that's true, I always recommend the "safe over sorry" method when it comes to installing software.
Sure, you might find an app you really want to install that isn't found in the standard repositories. If that's the case, check to see if it's available as either a Snap or Flatpak package. If so, install with one of those methods. If not, and you seriously need that app, do a bit of research to see if the repository can be trusted.
It only takes the installation of one rogue app to compromise a system. A bit of caution can help you avoid such a problem.
3. Use a strong password
It's your desktop, not a server. Right? Although that may be true, it doesn't mean you should continue using password or 12345678 as your password. There are a couple of things you should keep in mind when setting your user password:
- Network attacks
- Prying eyes
The most likely cybersecurity breach on a desktop is someone logging into your computer and accessing your information. But just because you're using a desktop doesn't mean it can't be breached by a threat actor who's gained access to your network.
Because of that, it's essential that you use a strong/unique password. Remember, that password isn't only required to log into your desktop but to run upgrades, install apps, and handle other admin tasks.
4. Don't use Chrome
Most Linux distributions default to either the Firefox web browser or Chromium. Although Chrome is available to easily install on the open-source operating system (and is the most widely-used web browser on the planet), it's also one of the least secure.
If you check out our list of most secure browsers for 2023, you'll notice that Chrome is nowhere to be found. On that list you'll find Brave, Firefox, Tor, DuckDuckGo, and Mullvad. Of those browsers, I would suggest either Firefox or Tor for Linux.
5. Enable your firewall
It might come as a surprise to you but some Linux distributions ship without the firewall enabled. For example, many distributions based on Ubuntu do not enable Uncomplicated Firewall out of the box. And most of the popular Ubuntu-based Linux distributions also don't ship with a firewall GUI.
To avoid having to run commands (although enabling UFW from the command line is as simple as sudo ufw enable), you could install the gufw GUI app (which can be installed from your distribution's app store). Once installed, you can enable the firewall by switching the On/Off slider to the On position.
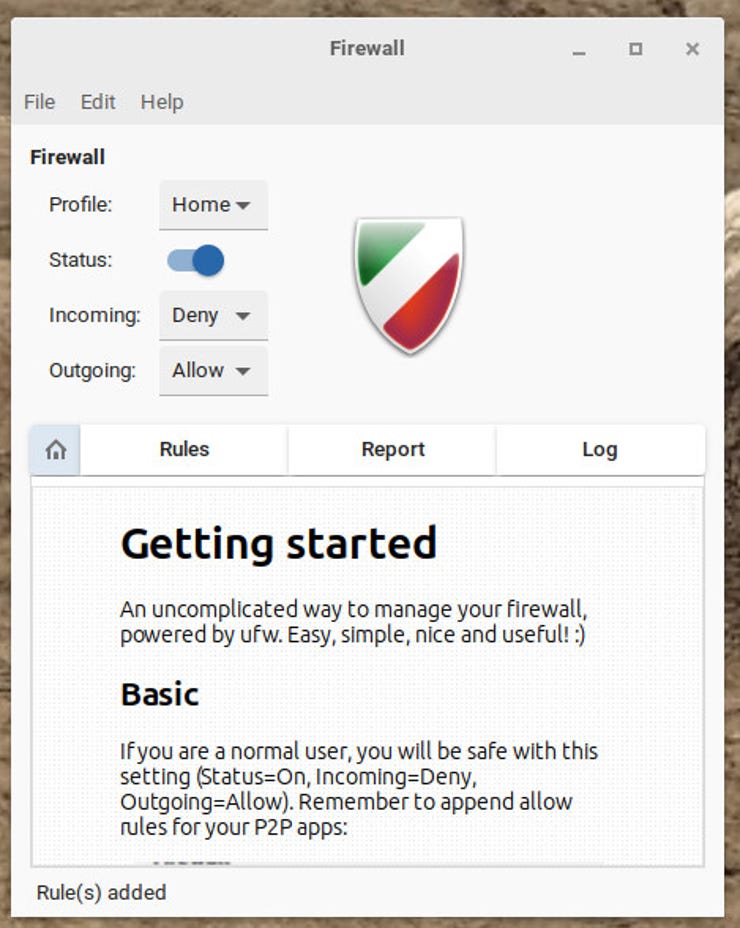
Gufw is one of the simplest firewall GUIs you'll ever use.
Jack Wallen/ZDNET
After you've enabled the firewall, you can enable any service (such as SSH or Samba) that you need to allow in, without having to run commands (such as sudo ufw allow ssh).
6. Never log in as root
Although Ubuntu-based distributions disable the root account, some distributions (such as Debian and Fedora) leave it enabled, so you could easily log in as the root user and do whatever you want without having to worry about sudo.
This is not good. If you log in as the root user, you open a hyper-privileged account. Should anyone breach your system, they too would have unfettered access to every service, app, and all of the data you've stored.
To that end, never log in as the root user. Ever. Always use sudo for admin tasks, so as to not leave your system open to heightened attacks.
7. Use Full Disk Encryption
If you're the one installing Linux on your machine, and your distribution of choice offers Full Disk Encryption (FDE), your best bet is to opt in. Why? Simple. Say someone were to steal your laptop. Without full disk encryption, they could remove the drive, mount it on another machine (which would avoid having to crack your user password) and have at the data within.
With FDE enabled, if that threat actor were to remove your drive and attempt to mount it, they would be unsuccessful, unless they knew your encryption password. Of course, this also isn't a guarantee. Remember the old saying, where there's a will, there's a way. But if you enable FDE, you'll make it considerably harder for someone to access your data without that encryption password.
Conclusion
You don't have to be a sysadmin to keep your Linux desktop distribution safe from cybersecurity threats. Follow these pieces of advice and you'll go a long way to keeping all of the data you have on your machine safe from attacks.
- Karlston and Adenman
-

 2
2



Recommended Comments
There are no comments to display.
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.